Indicators of Behavior (IOBs) – With 2020 Vision
Q: How are Indicators of Behavior different than Indicators of Compromise?
A: It is important to look at Indicators of Behavior because we, as an industry, are focused on detecting behaviors such as data theft, sabotage, espionage, malicious or compromised insider and to achieve these goals it became apparent that the industry needs to push beyond activity monitoring and truly understand the aspects of breaking down Scenarios like Data Theft into various use cases (e.g. Data Collection) and then breaking down the use cases into IOBs. See Nicolas Fischbach’s post on the topic for more detail.
Q: What are IOBs?
A: IOBs are cyber-behaviors which are monitored to understand risk within an organization. Anytime a document is created, saved, changed, mailed, shared, uploaded, downloaded or deleted those actions are analyzed as a series to determine context and intent. Actions that are modifications to systems are IOBs, such as creating or modifying scheduled tasks, installing new applications or services, or creating new user accounts. Email activities, such as sending to a personal domain, sending attachments or using automated email forwarding generates IOBs. Cloud administration and usage actions are IOBs, including creating new compute instances, accessing stored information, running queries and exporting the results. Collaboration tools and website activities are all IOBs, such as messaging, sending attachments, uploading information or leveraging new tools or sites.
A: By examining the activity of user accounts and devices and understanding how these IoBs fit together. Sometimes it is building a jigsaw puzzle where these indicators of behavior fall into place to show a full picture. There are times when there is a sequence of IOBs that indicate bad behavior. Often, looking at the behavior of user accounts and devices over time and finding changes based on IoBs. There are hundreds of Indicators of Behavior that we can observe and collect. Once we collect the IOBs, we can put them together to spell out specific behaviors, personas, and business outcomes that may manifest from these behaviors. We can also use Indicators of Behavior to predict what will happen if an organization makes a security process change (for example, disabling USB for external storage devices).
Q: How are IOBs used to understand risk?
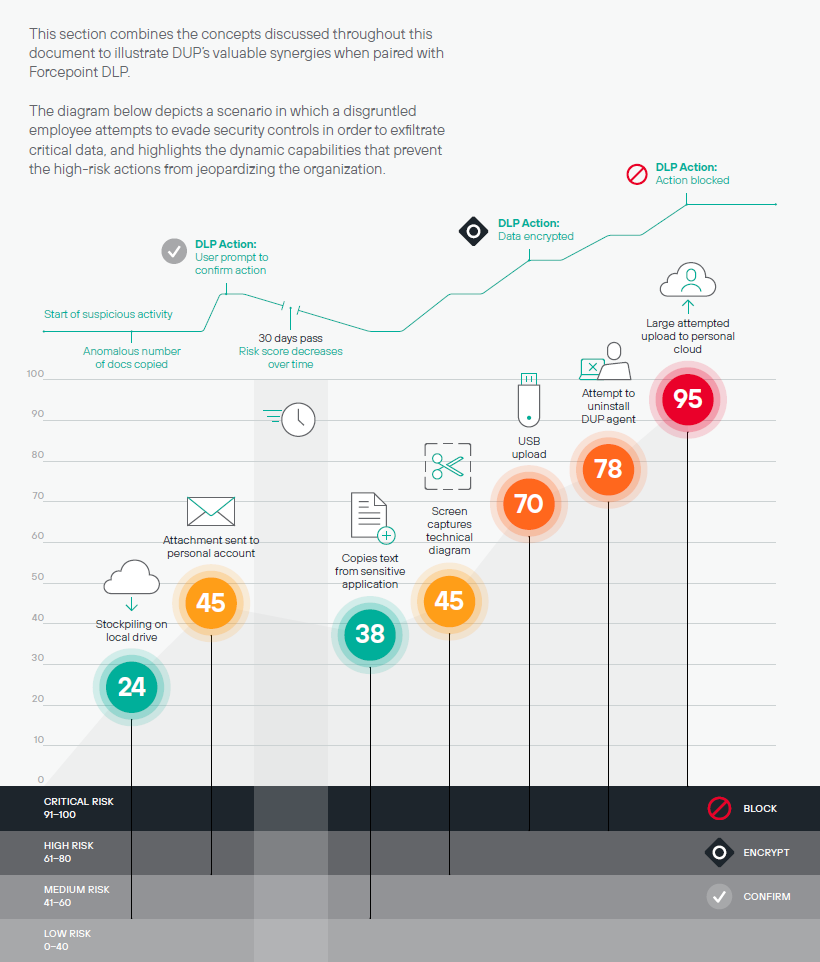
Here’s a visual that shows how different actions affect a user’s risk score over time:
User installed a personal cloud application on their laptop. This is an indicator of behavior. User uploaded files to an unknown domain. This is an indicator of behavior. User denied access to internal collaboration website. This is an indicator of behavior.
Q: What are some real-world examples of IOBs?
A: User created an email forwarding address to a Slack channel. This is an indicator of behavior. User changed from corporate network to phone hotspot and back again. This is an indicator of behavior. User uploaded code into Git repository. This is an indicator of behavior. User downloaded gigabytes of information to a removable storage device. This is an indicator of behavior. User sent email with attachment named “resume” to an external domain. This is an indicator of behavior.
Perhaps more importantly, leveraging IoBs to formulate behavioral detections will drastically reduce the amount of noise and false positives that an organization needs to chase down. We are very aware of analyst “alert fatigue” and believe there is a much better way to collect and present the most relevant information to the end user.
Q: What’s the “So What” of IOBs?
The way forward is going to be protecting the assets of the organization by taking action depending on the risk level and context of the user’s situation. We can warn the user and allow them to stop or proceed, we can take action to protect the data, block activities or even disable access for the user’s account and device. This will enable the organization to know that their data is protected from leakage, exfiltration or theft.
To summarize, IOBs present the best opportunity to provide adaptive trust and “stop the bad and free the good.”
By understanding cyber behavior and by understanding the history of the user, we can continue to allow behaviors to happen, especially if we have contextual information. If I’m at a conference and the conference organizer wants a copy of my presentation, I may save it to a USB and hand it to them. This may be the more important aspect of the business value of IOBs and Risk; we can enable the business to function “out of bounds” because we have a broader understanding of the user and the situation.
Additional Resources
To hear about IOBs in more detail, join me and Sarah Radin Wednesday, December 16, 11 am CST(17:00 GMT) for our “IOBs – A New Predictive Approach to Cybersecurity webinar.
This post was first first published on Forcepoint website by Alan Ross. You can view it by clicking here

