FireEye Breach Leveraged SolarWinds Orion Software
On December 8, 2020, FireEye disclosed theft of their Red Team assessment tools. FireEye has confirmed the attack leveraged trojanized updates to SolarWinds Orion IT monitoring and management software.
A highly skilled manual supply chain attack on the SolarWinds Orion IT network monitoring product allowed hackers to compromise the networks of public and private organizations, FireEye said. Meanwhile, SolarWinds released a hotfix for customers asking them to upgrade to Orion Platform version 2020.2.1 HF 1 as soon as possible to ensure their environment is safe. An additional hotfix release that both replaces the compromised component and provides several additional security enhancements is expected to be made available Tuesday, December 15.
Threat Hunting for Solarigate/SUNBURST
It is recommended to hunt for the evidence of exploitation of this attack, as traditional antivirus tools may not be aware of the attack. In a support advisory originally date from 2018, SolarWinds had recommended exempting their products from AV scans and group policy restrictions in order to run.
The compromised file in the SolarWinds supply chain attack was SolarWinds.Orion.Core.BusinessLayer.dll. You can hunt for the existence of this file by executing the following QQL query from Qualys Multi-Vector EDR. If this DLL has been found in your environment, you should immediately upgrade your SolarWinds deployment as described in the security advisory.
file.name:SolarWinds.Orion.Core.BusinessLayer.dll and file.properties.certificate.hash: 0fe973752022a606adf2a36e345dc0ed
Based on the hashes provided by FireEye, a more targeted query can be written as:
(file.hash.sha256:[`32519b85c0b422e4656de6e6c41878e95fd95026267daab4215ee59c107d6c77`, `ce77d116a074dab7a22a0fd4f2c1ab475f16eec42e1ded3c0b0aa8211fe858d6`, `019085a76ba7126fff22770d71bd901c325fc68ac55aa743327984e89f4b0134`, `dab758bf98d9b36fa057a66cd0284737abf89857b73ca89280267ee7caf62f3b`, `eb6fab5a2964c5817fb239a7a5079cabca0a00464fb3e07155f28b0a57a2c0ed`, `c09040d35630d75dfef0f804f320f8b3d16a481071076918e9b236a321c1ea77`, `ac1b2b89e60707a20e9eb1ca480bc3410ead40643b386d624c5d21b47c02917c`, `a25cadd48d70f6ea0c4a241d99c5241269e6faccb4054e62d16784640f8e53bc`, `d3c6785e18fba3749fb785bc313cf8346182f532c59172b69adfb31b96a5d0af`, `c15abaf51e78ca56c0376522d699c978217bf041a3bd3c71d09193efa5717c71`] or file.hash.md5:[`2c4a910a1299cdae2a4e55988a2f102e`, `846e27a652a5e1bfbd0ddd38a16dc865`, `b91ce2fa41029f6955bff20079468448`])
Additionally, according to CISA the evidence of C:WindowsSysWOW64netsetupsvc.dll should be considered suspicious and reported as an incident. The netsetupsvc.dll file is associated with the Microsoft Network Setup Service, which is a legitimate service and DLL when loaded from System32. The attacker appears to be masquerading as legitimate software to evade detection.
file.name:netsetupsvc.dll and file.path:`C:windowssyswow64` and file.properties.certificate.signed: false
The SolarWinds DLL file is a backdoor which then installs a Windows service to execute malicious code. Evidence of this can be detected by looking for the SolarWinds.BusinessLayerHost.exe process being ran. Evidence of this process execution can be hunted for with the following QQL query:
type:`process` and action:`running` and process.name:SolarWinds.BusinessLayerHost.exe
Based on the information provided by FireEye, a more targeted query can be written as:
type:FILE and action:WRITE and parent.name:`solarwinds.businesslayerhost.exe` and file.extension:[`exe`, `dll`, `ps1`, `jpg`, `png`]
Once malicious code has been executed, the malicious DLL then establishes a connection to avsvmcloud[.]com to download additional payloads, move laterally, and exfiltrate data.
Using this level of access, the attacker has been observed to steal credentials and increase privileges. Once access to highly privileged accounts is achieved, the attacker can achieve their actions on objectives in any number of ways. If any of these indicators has been seen in your environment, you should perform a thorough analysis of the environment looking for new accounts, external DNS requests, and other indicators to expose the breadth of the breach.
Identify SolarWinds Orion Assets using Global IT Asset Inventory
Qualys Global IT Asset Inventory allows you to gain visibility into SolarWinds Orion Assets using hybrid data collection sensors such as network scanners and Qualys Cloud Agent.
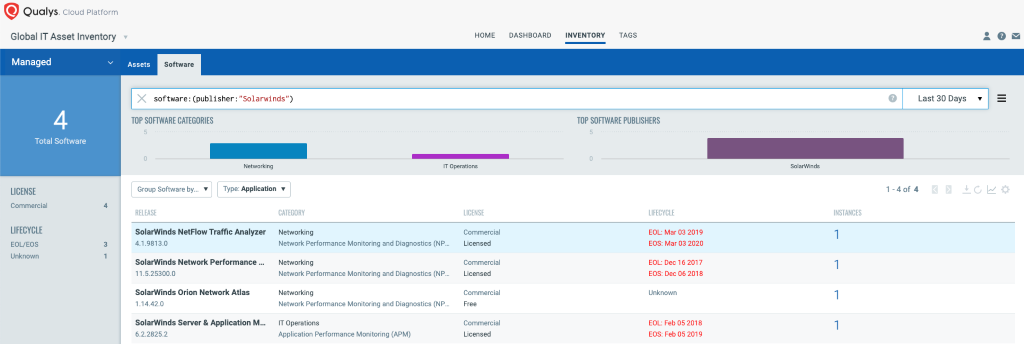
Discover SolarWinds Orion Vulnerability
Qualys has issued the information gathered (IG) QID 13903 to help customers track systems on which SolarWinds Orion is installed. This QID can be detected remotely using unauthenticated scan or via Windows authenticated scan or the Qualys Cloud Agent.
QID 13903: SolarWinds Orion Detected
To identify the presence of the hotfix issued by SolarWinds, Qualys has issued authenticated QID 374560:
QID 374560 : SolarWinds Orion Code Compromise
These QIDs are included in signature version VULNSIGS-2.5.57-3 and above and Cloud Agent manifest version 2.5.57.3-2 and above.
With Qualys Unified Dashboard, you can track SolarWinds Orion vulnerabilities, impacted hosts, their status and overall management in real time from vulnerabilities to EDR detections. Enable trending so you can keep track of these vulnerability trends across your environments. Unified Dashboard contains 50+ widgets from EDR & VM.
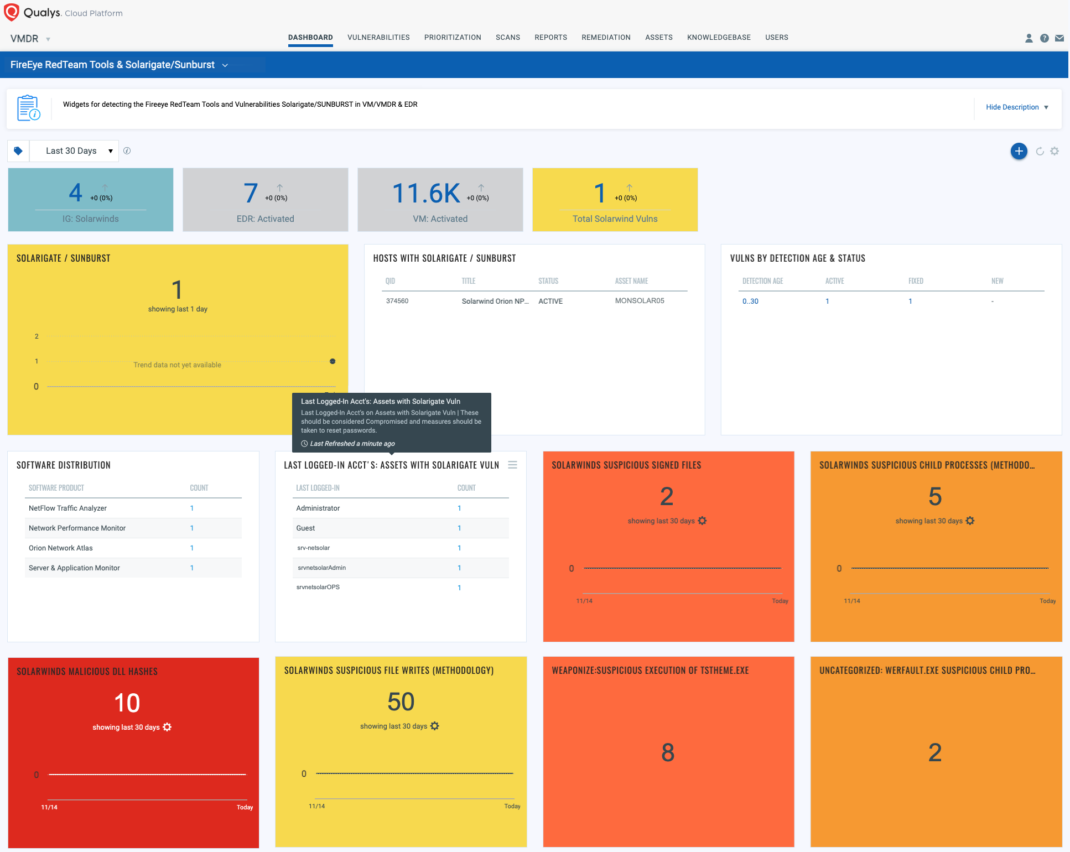
Solution
Users are advised to upgrade to SolarWinds Orion Platform version 2020.2.1 HF 1 or 2019.4 HF 6 as soon as possible. An additional hotfix release, 2020.2.1 HF 2 is anticipated to be made available Tuesday, December 15, 2020. We recommend that all customers update to release 2020.2.1 HF 2 once it is available, as the 2020.2.1 HF 2 release both replaces the compromised component and provides several additional security enhancements.
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching the high-priority SolarWinds Orion vulnerability.
Start your Qualys Multi-Vector EDR trial to protect the entire attack chain, from attack and breach prevention, to detection and response using the power of the Qualys Cloud Platform – all in a single, cloud-based app.
This post was first first published on Qualys Security Blog’ website by Animesh Jain. You can view it by clicking here

