Direct Access to Threat Intelligence With Mandiant Advantage
Our customers and partners have been asking for an easier way to stay informed of threat intelligence announcements. To address this need, earlier this year we launched Mandiant Advantage, our SaaS based platform for all Mandiant Solutions, with an initial launch focused on threat intelligence.
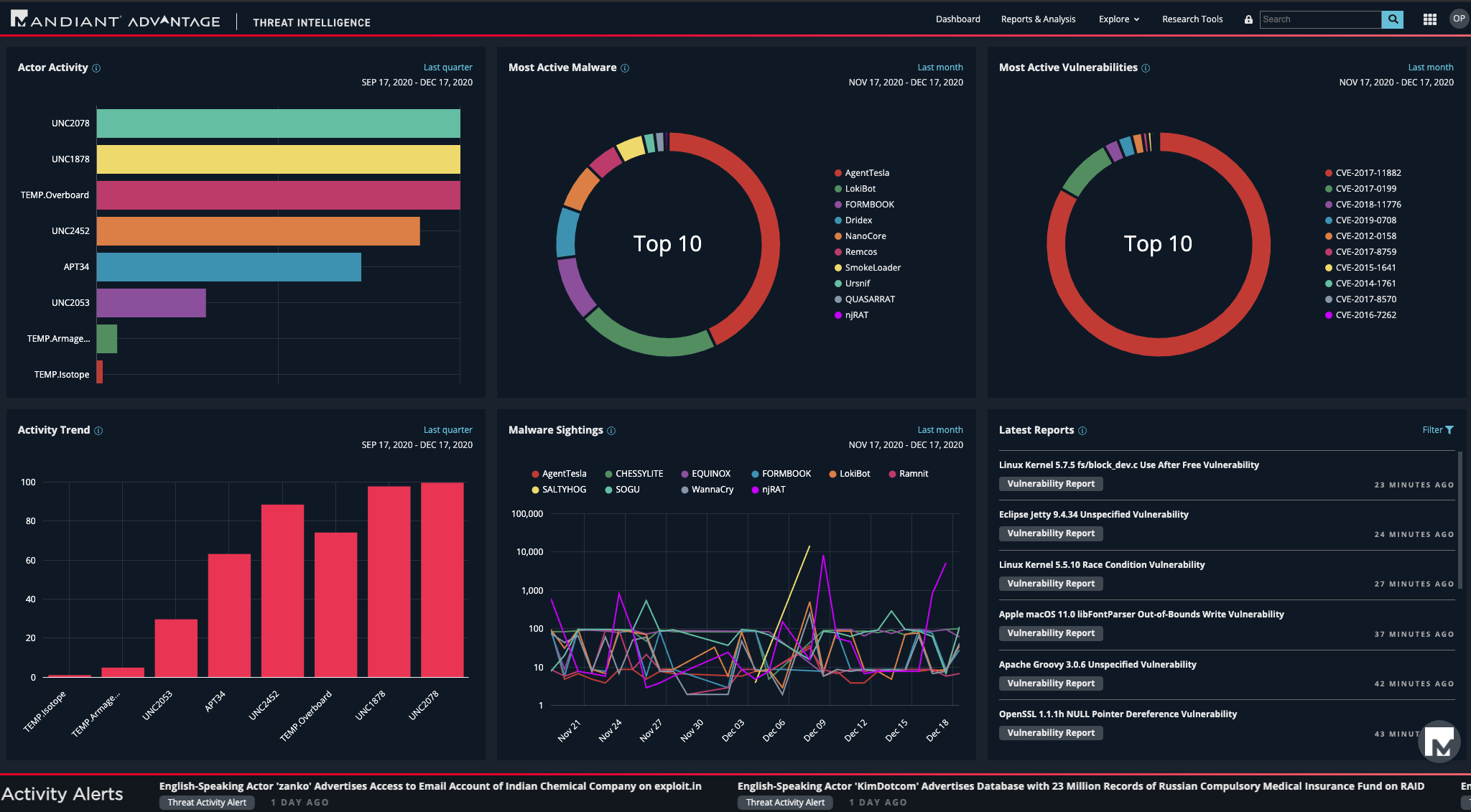
Mandiant Advantage Threat Intelligence Suite provides organizations of all sizes up-to-the-minute, relevant cyber threat intelligence. The Suite delivers four subscriptions, each focusing on a security persona such security operations analysts, vulnerability managers, threat analysts and security planners. In addition to the paid versions, Mandiant Advantage Free offers a no-cost subscription with capabilities such as:
- Global dashboards providing actor, malware, vulnerabilities activity trends
- Access to open-source indicators with Mandiant maliciousness score
- News analysis with Mandiant expert judgements and commentary
- Actor, malware and vulnerability descriptions accessible via portal
Key Use Cases and Benefits From Mandiant Advantage Free
- Community preparedness for global, high priority events: When Mandiant discovers major threat events (such as SUNBURST, FIN11, UNC1945) we publish the actor profile and related malware details, so any user in the security community can be informed and act against these high impact, global adversaries.
- Threat descriptions for investigators and responders: More than just a yes-no validation, security operations users can review hundreds of actor or malware names to find the description, targeted industries, and active geographic regions. Users have a first glimpse on the nature of the malware and plan for investigation using more specific tools of choice (i.e., NTA, SIEM, EDR)
- Threat risk trends and news analysis: Timeframe customizable actor, vulnerability and malware dashboards provide threat risk managers important activity trends and ensure they are informed of sudden activity changes. A continuous stream of news tickers allows security professionals to review news media content with Mandiant intel analyst ratings and comments.
UNC2452 and SUNBURST
On Dec. 13th, we posted to all Mandiant Advantage: Threat Intelligence users a series of specific intelligence reports related to the recent UNC2452 campaign involving the SUNBURST backdoor. The report includes detailed views on SUNBURST, TEARDROP and BEACON malware, plus an UNC2452 overview that includes descriptions, targeted industries, motivations, associated malware, MITRE ATT&CK map and indicators.
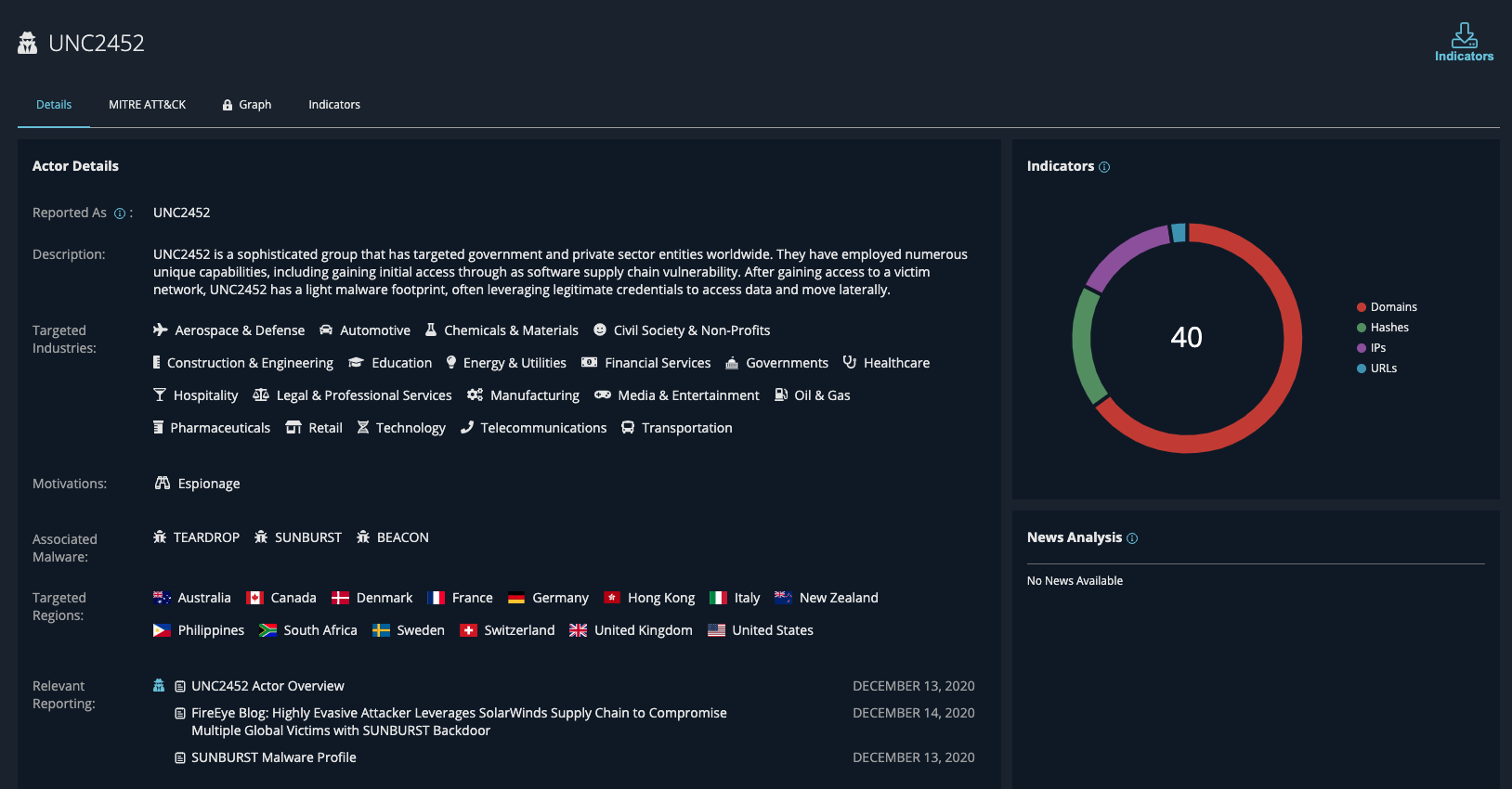
The UNC2452 campaign has been one of the major cyber events of the past few years targeting thousands of organizations around the world. FireEye was the first organization to detect the campaign and Mandiant Advantage is the outlet for easy access to information on this and other new discoveries. The key details we published include:
- MITRE ATT&CK map for the actor as well as the leveraged three malware families to give users an understanding of the attacker path
- Indicators of compromise including domains, hashes and URLs, so users can immediately update their detection tools of choice (SIEM, NTA, EDR)
- Direct consumable YARA rules to power up endpoint detection tools
- Operational report describing the malware families
- UNC2452 actor profile with targeted industries, motivations and region
More than just another threat intelligence feed or consolidation of open-source indicators, Mandiant Advantage provides security organizations of all sizes with threat insights directly from the Mandiant front lines, enabling users to see newly discovered threats through the eyes of a Mandiant analyst and allowing decision makers to take the right actions.
Visit our website for more information and to register for Mandiant Advantage Free.
This post was first first published on
‘s website by Phil Montgomery. You can view it by clicking here

