VMware Carbon Black Announces Splunk Integration to Streamline and Modernize SOC Workflows
Introducing Unified VMware Carbon Black Cloud App for Splunk
At VMware Carbon Black, our ecosystem of integration and alliance partners has been a core part of our vision and strategy. Today, with thousands of customers adopting the VMware Carbon Black Cloud to secure their endpoints and workloads, our partner ecosystem continues to grow, developing integrations to deliver enhanced workflows and security to our customers.
We are proud to announce the release of a consolidated integration to connect the VMware Carbon Black Cloud platform with Splunk. Through this application, customers can eliminate disparate log sources and outdated integrations in their Splunk instance and streamline their security operations and processes.
VMware Carbon Black Cloud App for Splunk
This initial release of the VMware Carbon Black Cloud App for Splunk provides a single solution to replace the product-specific VMware Carbon Black Cloud integrations with an updated solution that uses the latest VMware Carbon Black Cloud APIs and is compatible with the latest version of Splunk. Going forward, this app will be updated and improved to continually deliver the latest VMware Carbon Black Cloud features and data to Splunk users.
“The integration of the VMware Carbon Black Cloud and Splunk will provide our joint customers with real-time data to identify risks and secure their environments. Together, the two solutions will deliver the ability to detect and stop attacks and empower customers to improve the efficiency and accuracy of their existing SOC workflows.”
Jane Wong, Vice President, Security Products, Splunk
Extend Endpoint Visibility and Control to Splunk
Using this integration, joint customers can utilize their VMware Carbon Black Cloud data, alerts, and threat intelligence within Splunk alongside their other security and IT data. The VMware Carbon Black Cloud app for Splunk fully utilizes the Splunk Common Information Model (CIM) to provide immediate value to users through pre-populated dashboards while also eliminating upfront configuration and data mapping tasks.
The VMware Carbon Black Cloud App for Splunk reduces the number of log sources that need to be ingested into Splunk by providing direct access to watchlist alerts from multiple third-party sources, such as other security products or threat intel feeds, from directly within the app. Leveraging watchlist alerts enables context from email, network, or cloud monitoring solutions to be correlated alongside endpoint analytics to provide analysts with the information they need from across their environment to confidently investigate and respond to threats, all from a single console.
Streamline & Automate Remediation Tasks from within Splunk
The VMware Carbon Black Cloud App for Splunk includes multiple pre-built Adaptive Response Actions to enable analysts to orchestrate and deploy remediation actions to endpoints from within the Splunk console. Adaptive Response actions available in this app include Quarantine/Un-quarantine Endpoint, Add/Remove IoC from Watchlist, List Processes, Kill Processes, and Get File Metadata.
Leveraging these Adaptive Response actions alongside the VMware Carbon Black Cloud’s endpoint query capabilities provides a streamlined workflow for analysts to identify risks, audit their endpoints, and deploy updates to harden or remediate endpoints all from a single console.
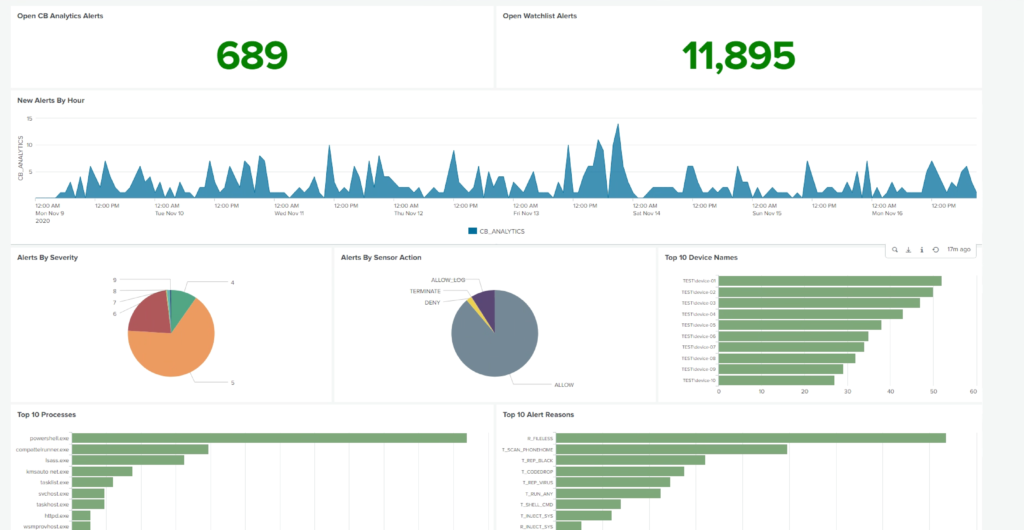
Key Features and Capabilities:
The new VMware Carbon Black Cloud App for Splunk provides access to our latest features and datasets from within the Splunk console. Key features and capabilities of this integration include:
- Support for Splunk 8+ and Splunk Enterprise Security 6+
- Single integration for all VMware Carbon Black Cloud products
- Support for multi-tenant environments
- Self-service, customizable configuration
- Multiple data delivery options (Event Forwarder via the AWS Add-on or Carbon Black Cloud Input Add-on)
- Out-of-the-box dashboards
- Pre-built Adaptive Response actions
- Support for the Splunk Common Information Model (CIM)
- Support for distributed Splunk environments via Input Add-on or Tech Add-on
Additional enhancements will be available in early 2021, including full integration of Carbon Black Cloud Audit & Remediation capabilities and vulnerability management reports with support for CIM.
Check out the app listing on Splunkbase to download the latest VMware Carbon Black Cloud App for Splunk.
The post VMware Carbon Black Announces Splunk Integration to Streamline and Modernize SOC Workflows appeared first on VMware Carbon Black.

