Variants of Emotet Malware
The Cofense Phishing Defense Center (PDC) team has seen a resurgence in the number of Emotet variants in the past few months, with the majority of payloads being delivered via highly obfuscated macros embedded within Microsoft word documents.
By Ala Dabat and Adam Martin
Figure 1
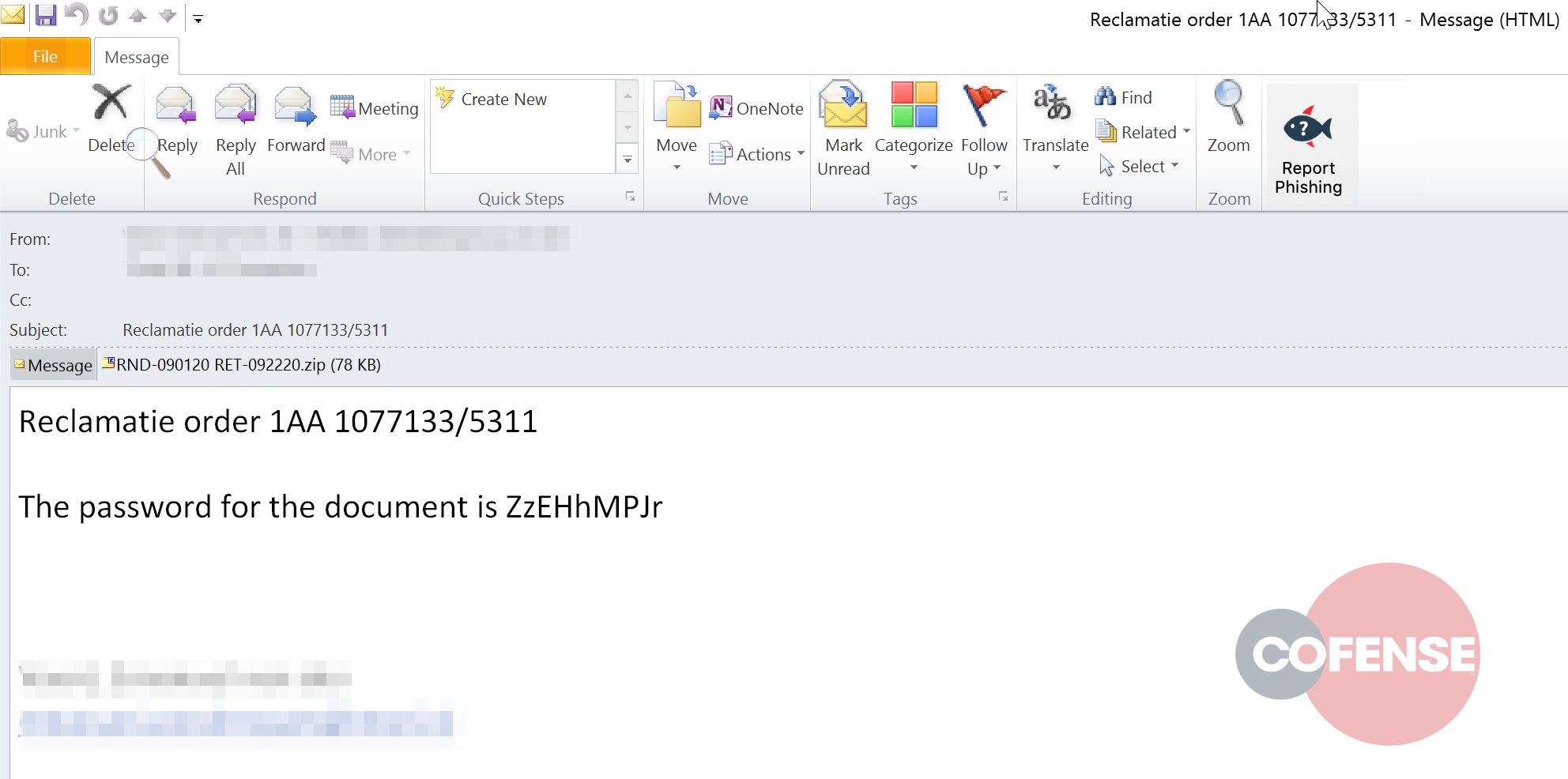
We will be taking a look at an example of Emotet that has managed to bypass Office365 SEGs using simple email layouts with a limited number of red flags usually picked up by traditional spam filtering.
Figure 2
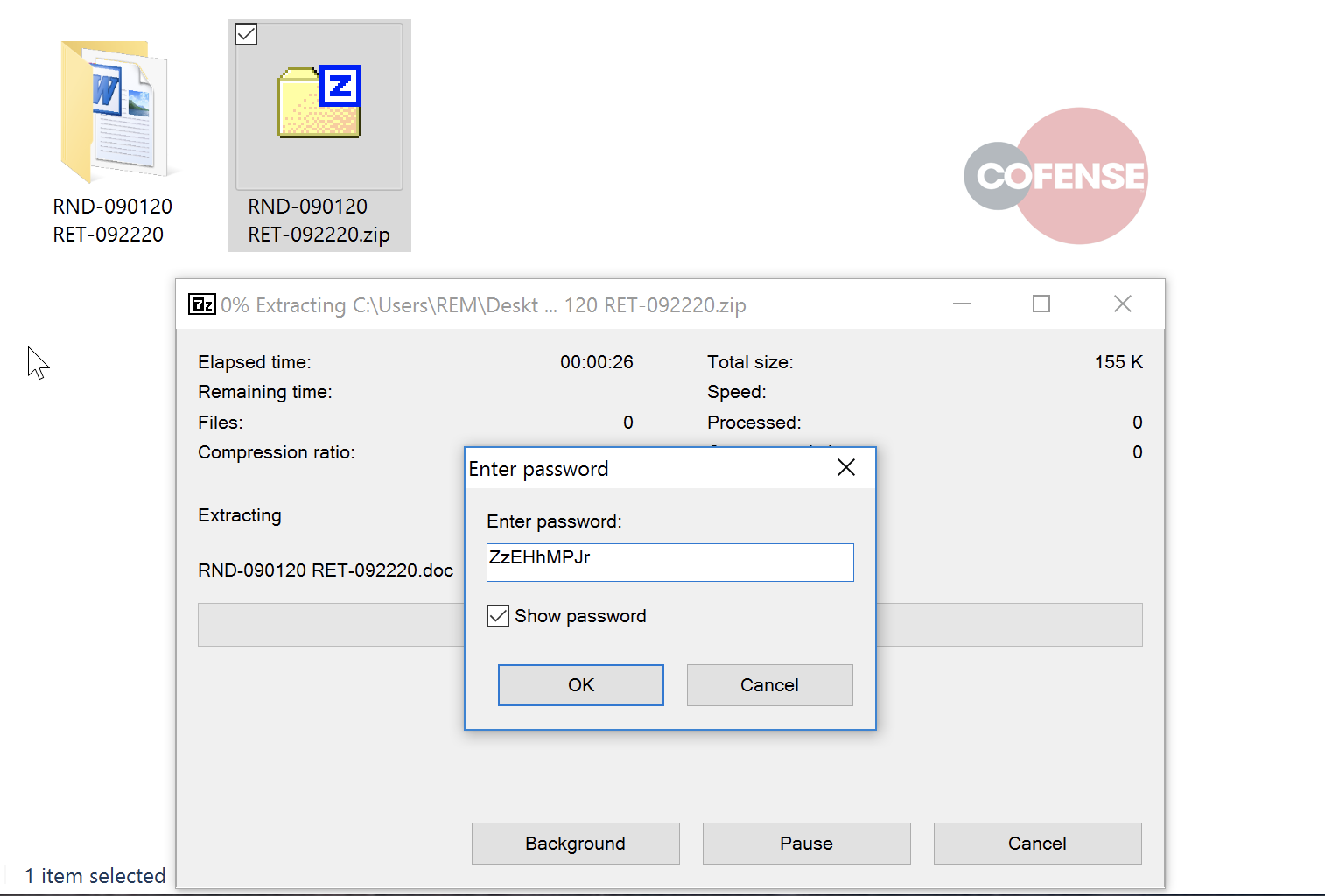
A common pattern being observed has involved the number of payload deliveries bypassing traditional security scanning methods through both compressing and password protecting folders containing the malicious file. This makes it impossible for security scan engines to examine folder content.

Once the password protected file is decompressed the malicious Emotet payload is presented, ready for the target to open.
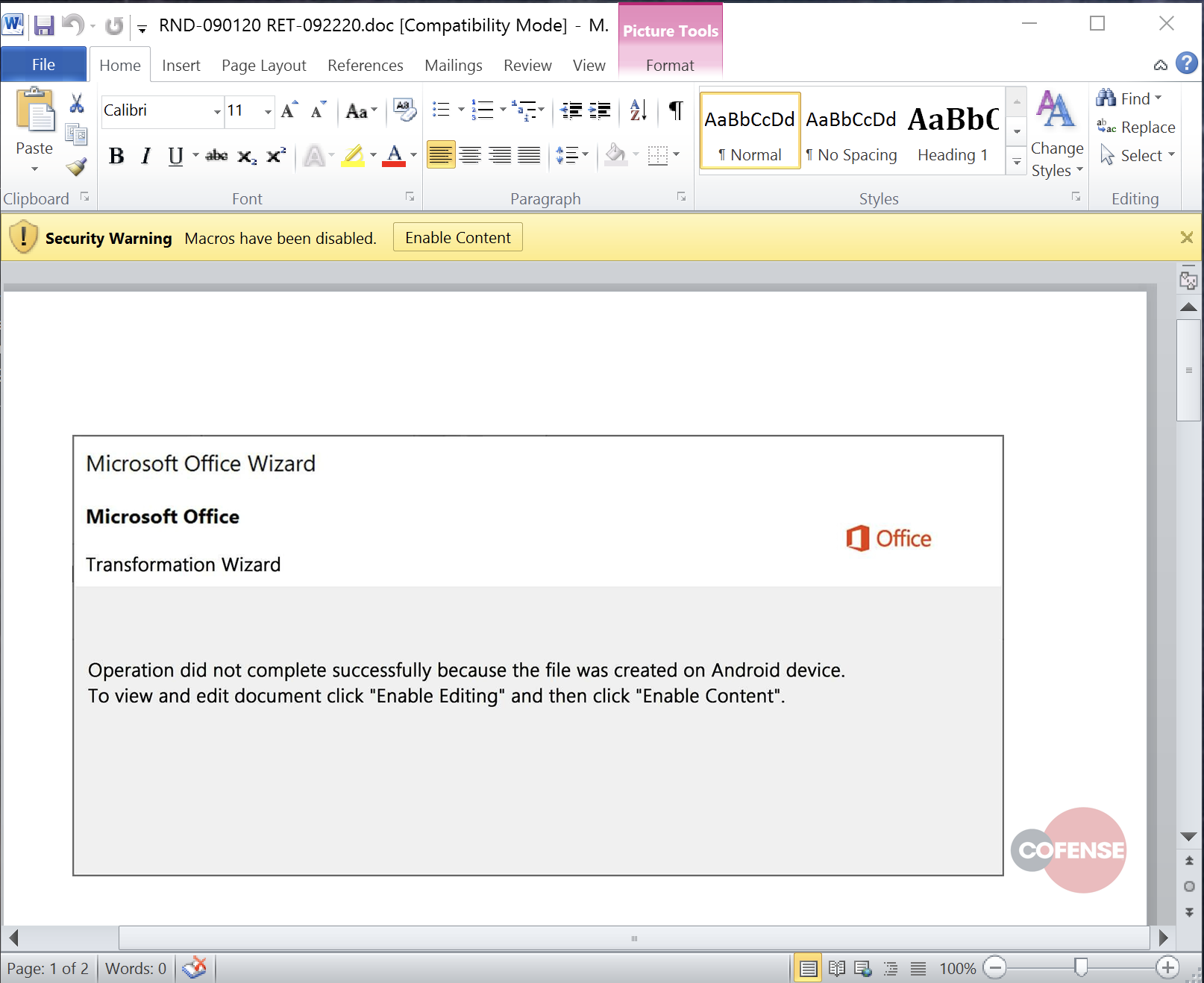
Figure 3
A call–to–action command is then executed (usually using PowerShell) via heavily obfuscated macros.
Figure 4
Figure 5
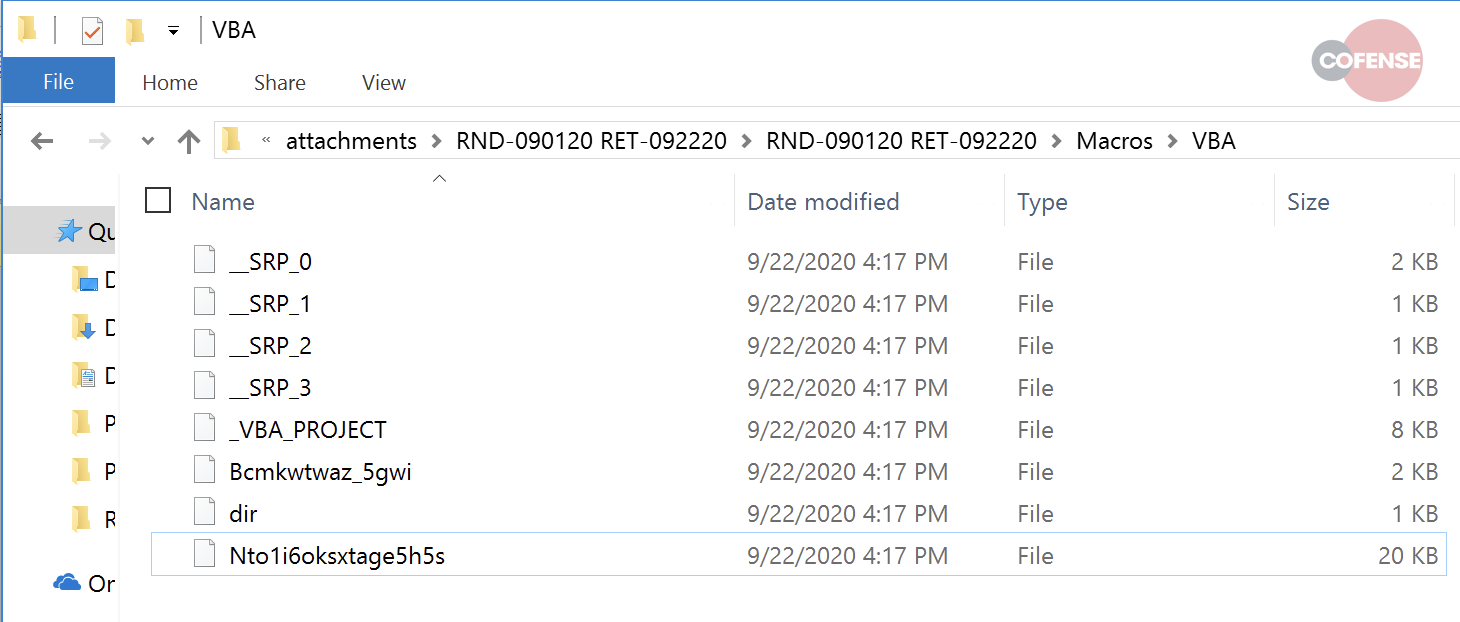
The call to action then downloads up to several variants of both Emotet and other malware families from a number of different command–and–control operations, which is in stark contrast to earlier generations of Emotet malware. Emotet appears to have the capability of exploiting known Windows system vulnerabilities, as well as having the ability to scan Windows directories in order to harvest sensitive data.
Following on from the contacted URLs displayed in the above figure, some testing was carried out on payloads downloaded. The URL found in Figure 7 was used as a hosting service for the Emotet sample. This is illustrated by the executable downloaded to the host machine.
Figure 6
Figure 7
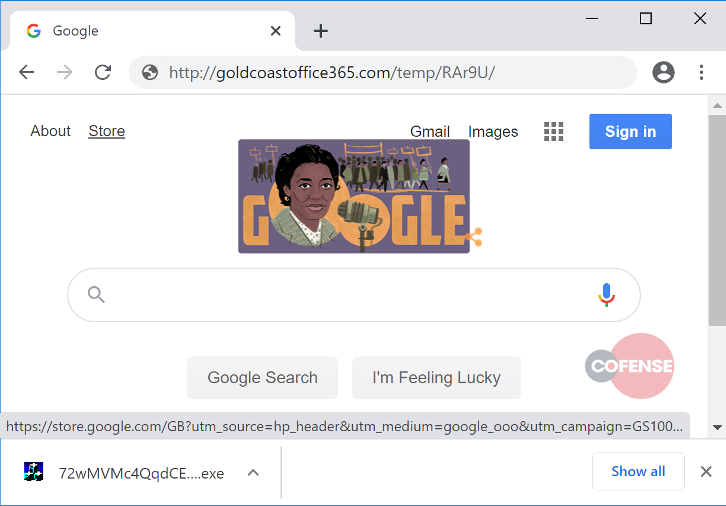
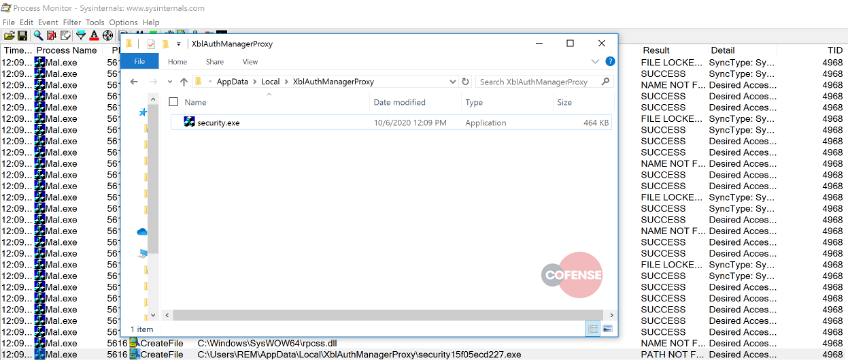
Once executed, this malicious binary will delete itself from the original folder it was downloaded to, and will terminate its running processes. Then it will create a carbon copy of itself in “/AppData/Local/XBAuthManagerProxy” under the name “security.exe.” A comparison of both the original SHA256 and the newly created file confirms they are identical.
Dynamic analysis of the dropped executable reveals a host of interesting functions being created and called. Native Windows DLLs associated with networking are utilized for connectivity seen in Figures 9 & 10.
Figure 8
Figure 9
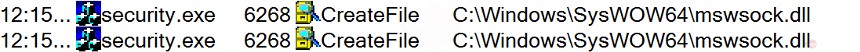
Figure 10
![]()
A network traffic analysis confirms that information was posted to the aforementioned C2 address.
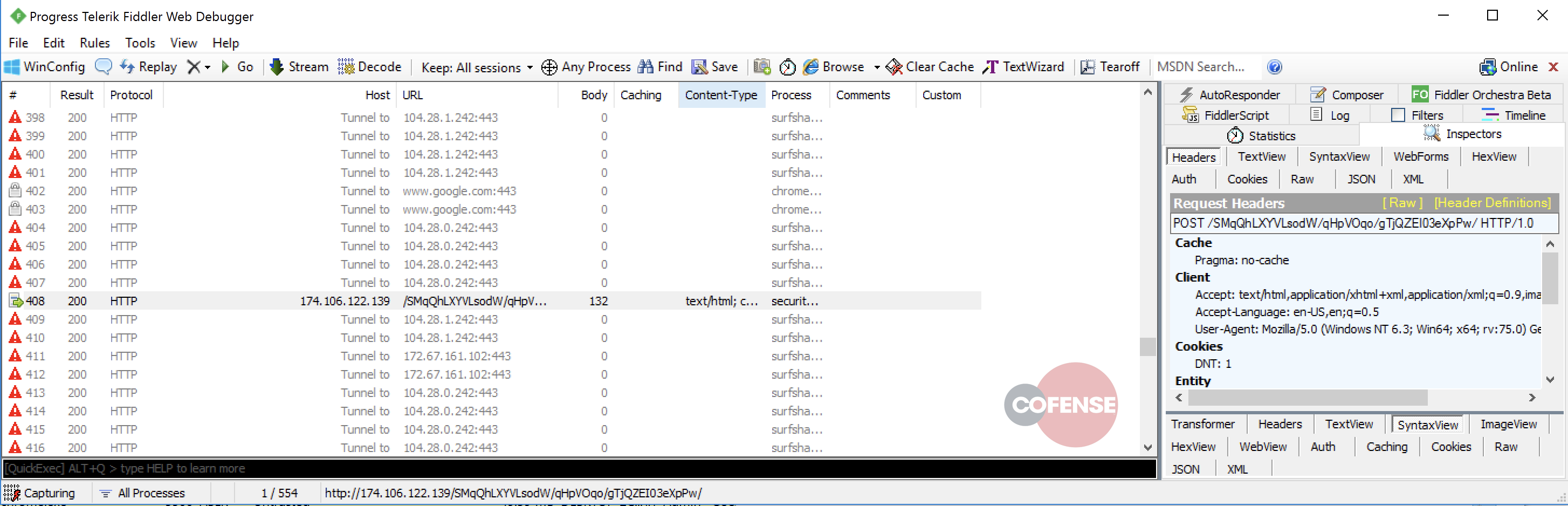 Figure 11
Figure 11
Figure 12
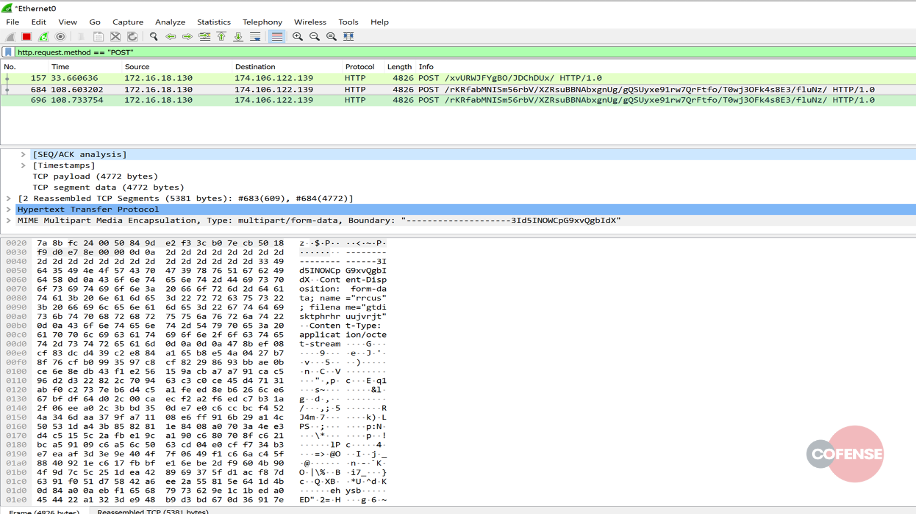
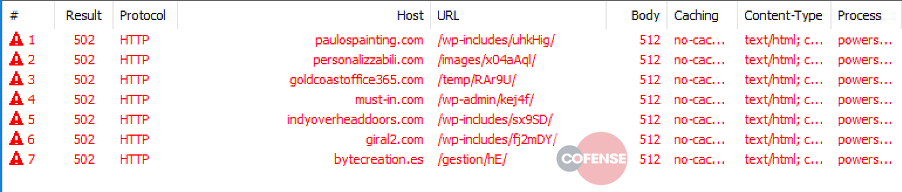
hxxp://personalizzabili[.]com/images/x04aAql/
Indicators of Compromise
hxxp://paulospainting[.]com/wp-includes/uhkHig/
hxxp://must-in[.]com/wp-admin/kej4f/
hxxp://goldcoastoffice365[.]com/temp/RAr9U/
hxxp://giral2[.]com/wp-includes/fj2mDY/
hxxp://indyoverheaddoors[.]com/wp-includes/sx9SD/
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
hxxp://bytecreation[.]es/gestion/hE/174[.]106[.]122[.]139/SMqQhLXYVLsodW/qHPV
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here