Find and Verify Threats in Splunk Phantom With FireEye Detection On Demand
Threats can and do come from everywhere, and every organization approaches security differently based on their needs, industry and environment. But the one thing organizations all have in common is the need for an intelligence-backed, validated threat detection capability with enough contextual analysis to act on.
With the new FireEye Detection On Demand application for Splunk Phantom, any company can integrate with FireEye’s award-winning detection and intelligence to verify threats. Security teams can now analyze any file, object or URL with FireEye in their Splunk Phantom playbooks, regardless of where that alert was generated.
FireEye compares submissions to the latest known tactics and signatures of threat actors using static analysis, artificial intelligence and machine learning. FireEye also determines the possibility of secondary or combinatory effects across multiple phases of the attack lifecycle to discover never-before-seen exploits and malware.
Specifically, our new app can help organizations with:
- Validating alerts: Validate alerts from security tools against FireEye Detection On Demand to reduce false positives and to help teams focus on top threats.
- Checking websites: Investigate suspicious websites being viewed in an organization for malicious behavior.
- Threat Hunting: Get detailed reports on malicious files and websites to better understand what they do and how they work, which can help stop threats from spreading and prevent them from reoccurring in the future.
Use FireEye to Enhance Existing Splunk Phantom Playbooks
Splunk® Phantom provides security orchestration, automation and response (SOAR) capabilities that allow analysts to improve efficiency and shorten incident response times. With Phantom, organizations are able to improve security and better manage risk by integrating teams, processes and tools together. Security teams can automate tasks, orchestrate workflows and support a broad range of security operations center functions including event and case management, collaboration and reporting. Here are just some of the ways that the FireEye Detection On Demand application can be used to enhance Splunk Phantom playbooks:
Stopping Ransomware
By leveraging the preexisting Splunk Phantom Ransomware playbook, quickly use the FireEye Detection On Demand app to analyze suspicious files to automate key investigation and containment steps.
Triaging Events
Quickly check any event that contains objects or URLs to verify if FireEye deems it malicious. This can help prioritize the thousands of events that security teams see each day.
Automating Website Unblock Requests
FireEye Detection On Demand can check if a website is malicious before security teams decide to unblock it for accessibility.
Verifing Alerts and False Positives
It’s not possible to review every security alert that is sent every day by all security tools. Verifying with FireEye can help teams quickly understand which alerts they should spend their limited time on.
Investigating Phishing Emails
Integrating FireEye Detection On Demand, teams can analyze files and retrieve threat intelligence on the URLs and files relating to a particular suspicious email.
Enriching Cases with FireEye Intelligence
Utilize the reports generated from the analysis of objects and URLs as teams investigate cases throughout an investigation. Quickly access reports such as in Figure 1 to understand the details of the threat and get key information about where it falls in the MITRE ATT&CK framework (Figure 2).
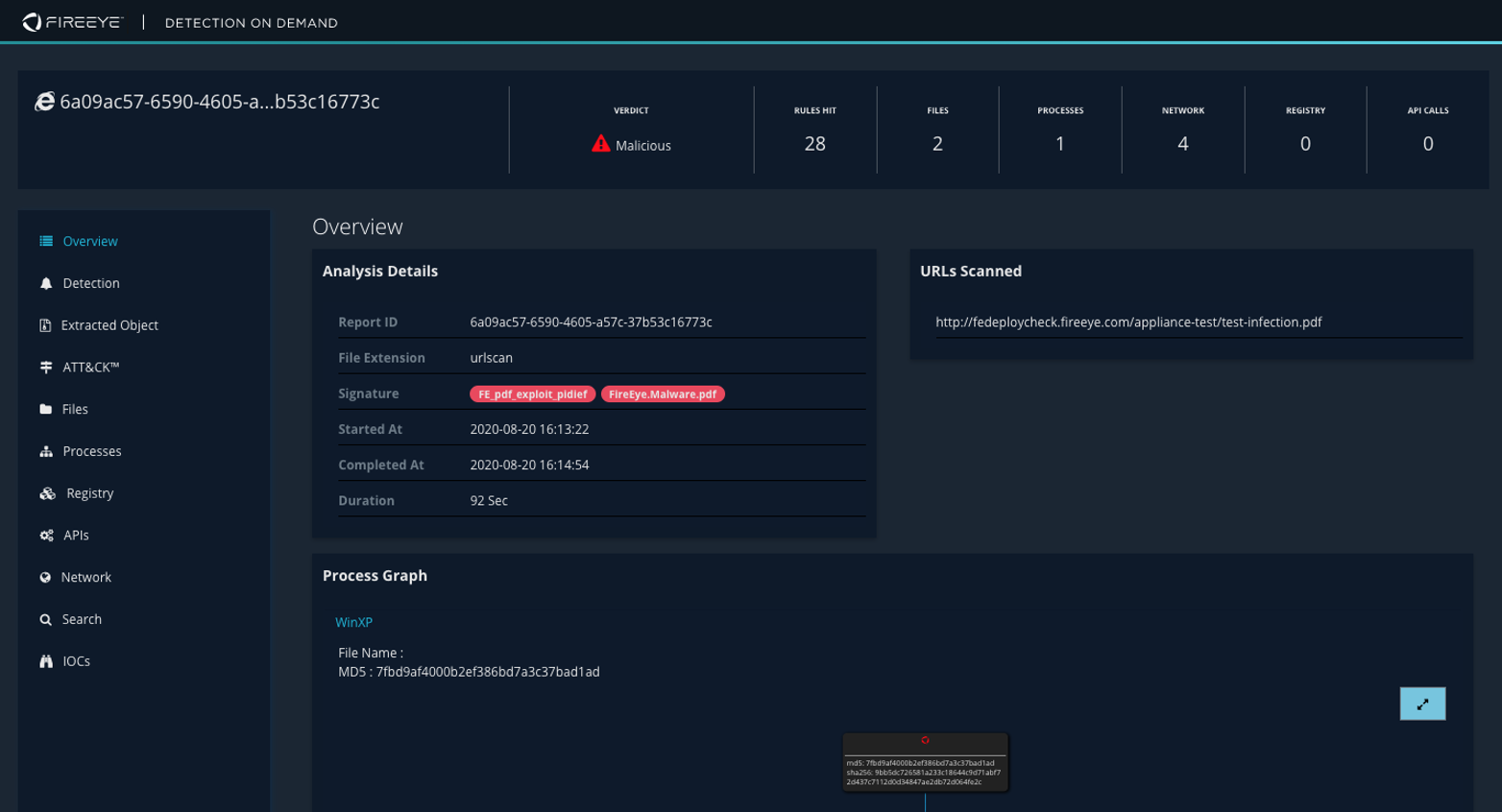
Figure 1: Sample FireEye generated report
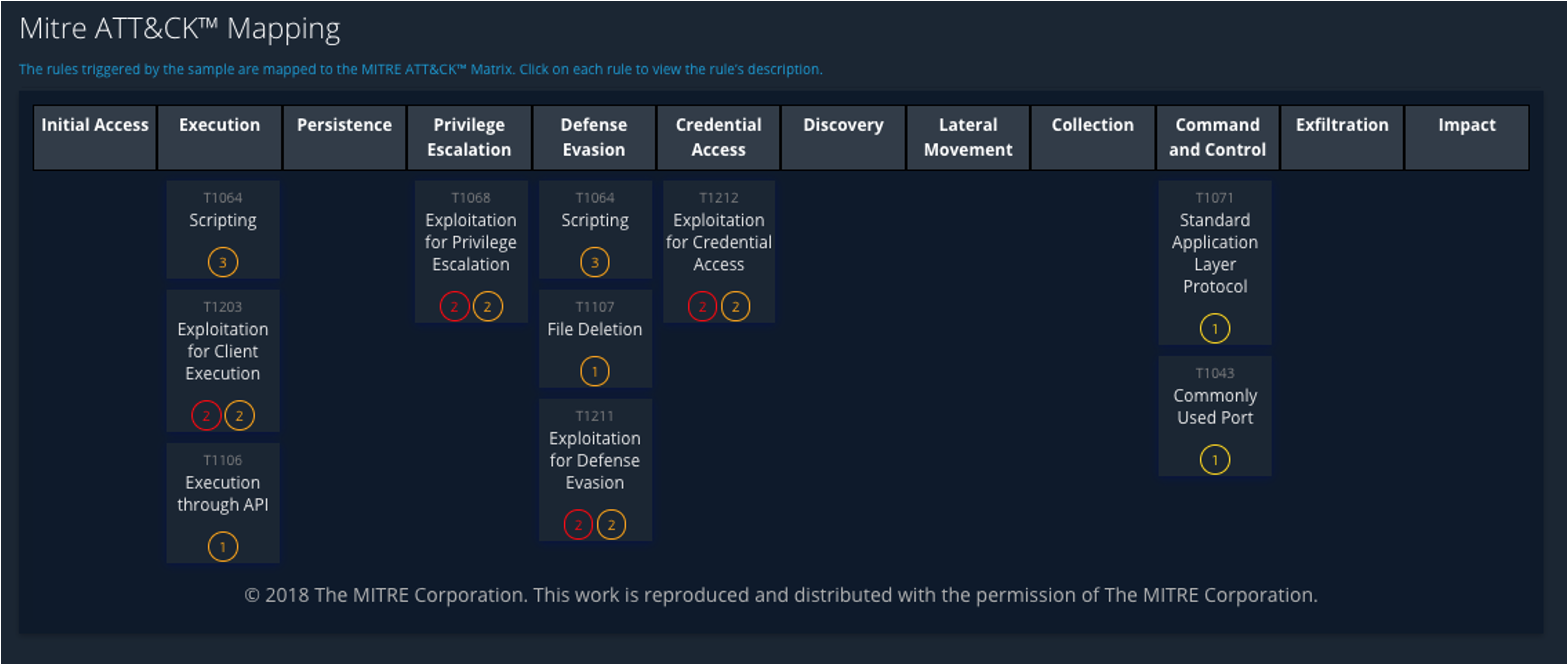
Figure 2: Sample MITRE ATT&CK Mapping report
Get Started
To start automating security operations with FireEye detection, please request a free one month trial of Detection On Demand at the AWS Marketplace (for up to 100 submissions), download the FireEye Detection On Demand Phantom app, drop in the API key and be ready to go!
To install the app in a Splunk Phantom instance, download and extract the ZIP file at the FireEye Market.
Log in to the Phantom instance and navigate to the “Apps” page from the dropdown menu. In the top right corner, click on “Install App” (as seen in Figure 3) and upload “phdetectionondemand.tgz”. A message should appear that reads, “App successfully imported”.
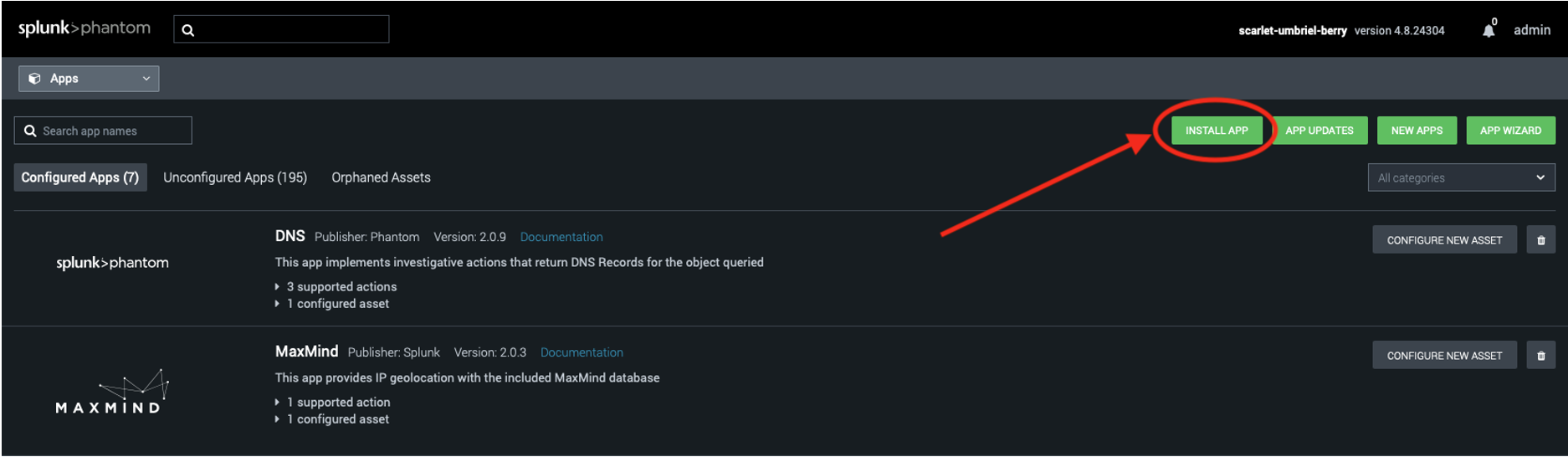
Figure 3: Apps page with “Install App” button circled
Configure
The Detection On Demand app can be found in the “Unconfigured Apps” tab on the “Apps” page (Figure 4). Click on this tab and search for “detection”. Click on “Configure New Asset” to configure connection details to Detection On Demand.
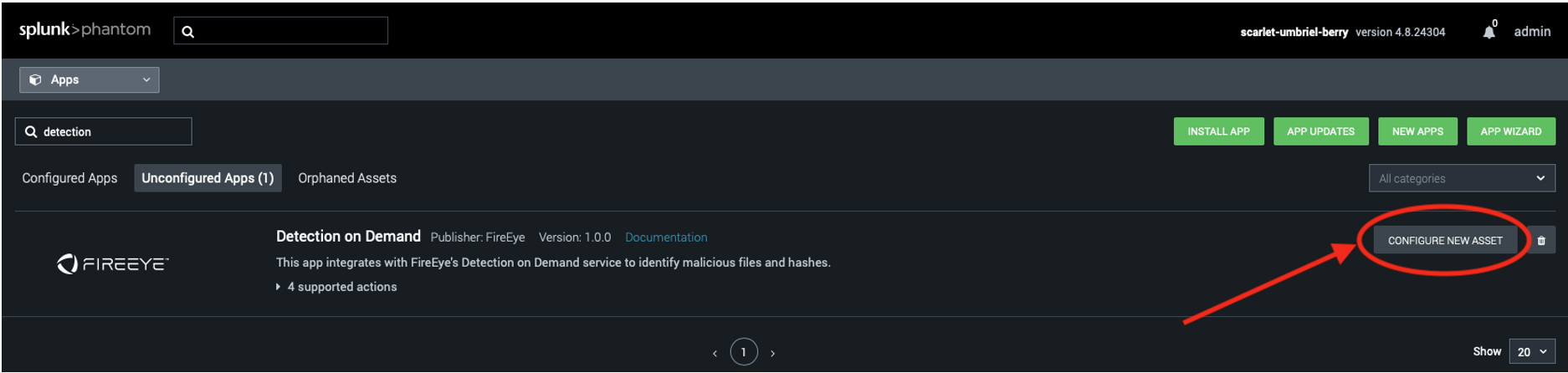
Figure 4: Search results for “detection” under “Unconfigured Apps” tab
On the “Asset Info” tab, fill out the information shown in Figure 5. Any name can be used for the asset.
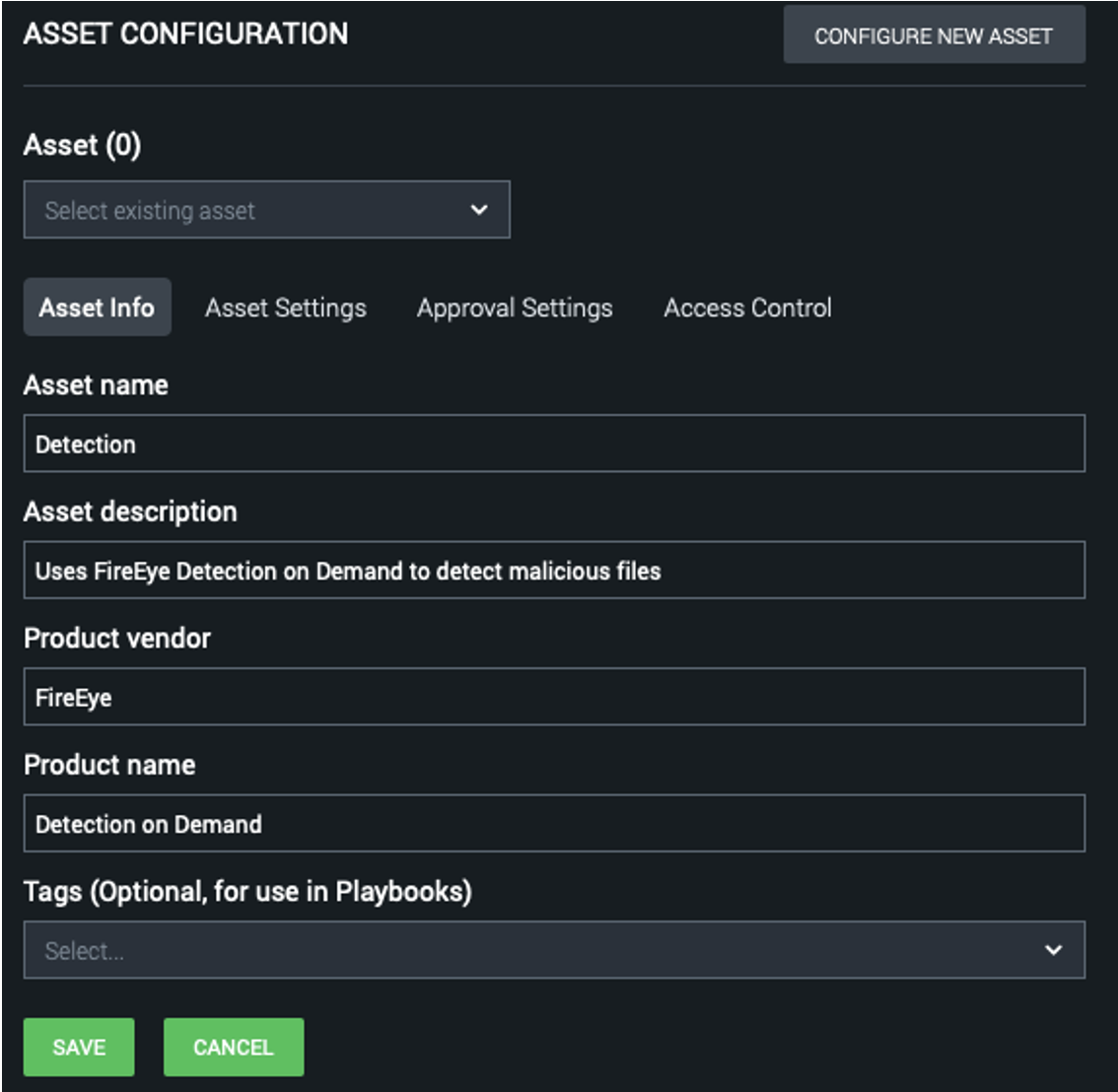
Figure 5: Asset Info tab
In the “Asset Settings” tab (Figure 6), leave the base URL field as the default, but paste the API token into the other field. Click “Save” and then click “Test Connectivity” to make sure the connection to the Detection On Demand service works, as seen in Figure 7.
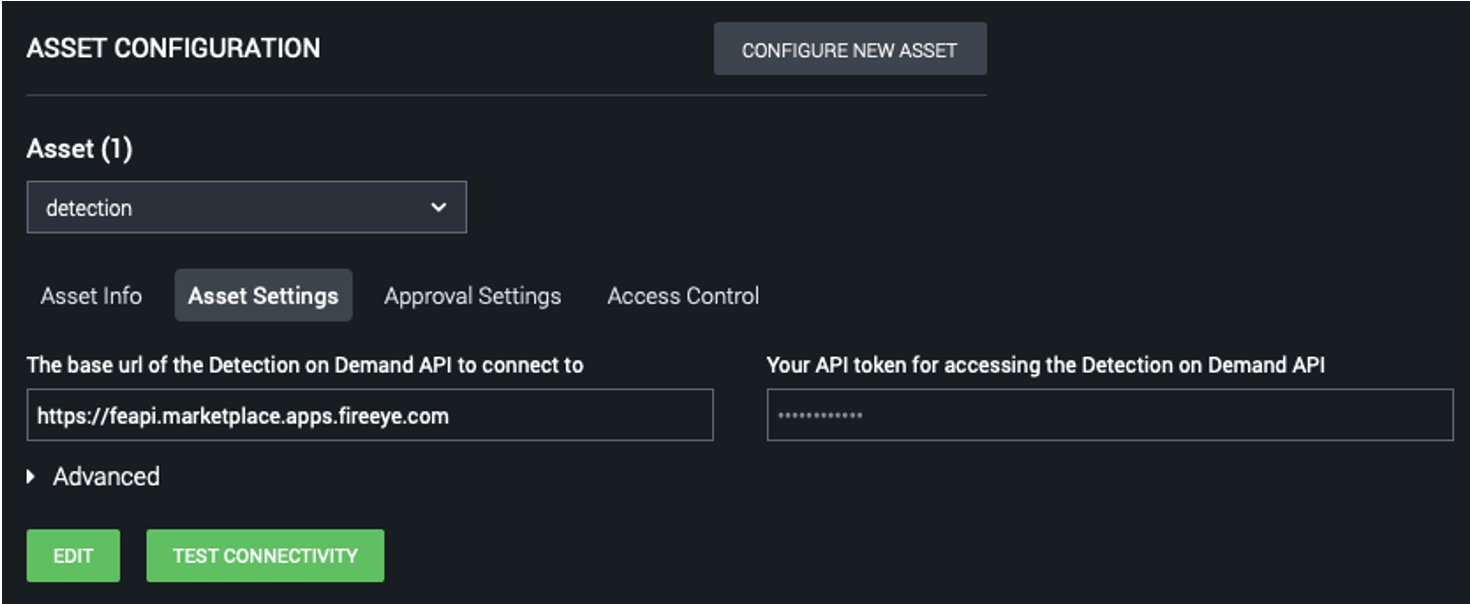
Figure 6: Asset Settings tab
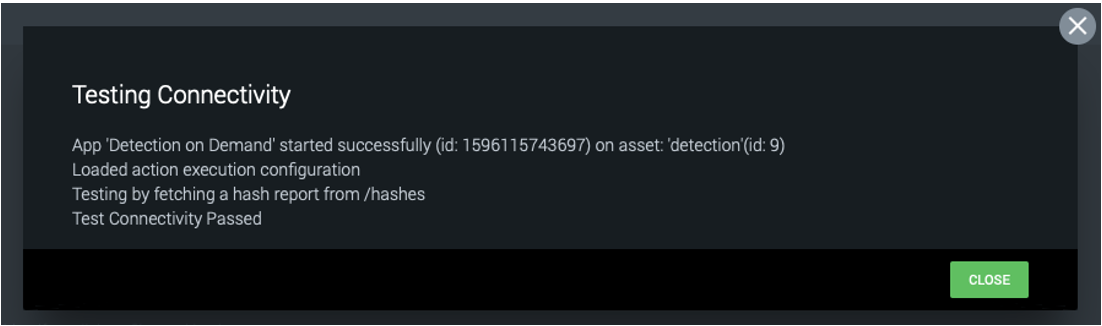
Figure 7: Connectivity testing
If the test connection fails, please make sure the API key is valid by executing an API request from Postman, the command line, or any other API request tool. If the API key is valid but the test connection still fails, please contact [email protected] with the output from the test connection.
For More Information
Please reference the FireEye Market for more information and more detailed instructions on how to setup playbooks using the FireEye Detection On Demand Splunk Phantom app. Please ask questions in our FireEye Community Splunk topic about the app, new features or any other feedback.
This post was first first published on
‘s website by Christopher Unick. You can view it by clicking here

