At the User’s Expense: Threat Actors Weaponize Companies’ Employee Reimbursements During the Pandemic
With the health crisis that is COVID-19, employees are dutifully working from home. While some already had home offices decked out with dual monitors, printers and the like to complete their jobs, others did not. Because of this many companies took to offering their employees a chance to buy the tools needed for their newly designated remote positions through added reimbursements.
By Harsh Patel, Cofense Phishing Defense Center
s 1 and 2: Email Body
The Cofense Phishing Defense Center (PDC) has identified a campaign that attempts to steal employee credentials by leveraging reimbursement emails. This campaign was seen across multiple employee groups in the insurance, medical, professional services and banking industries. 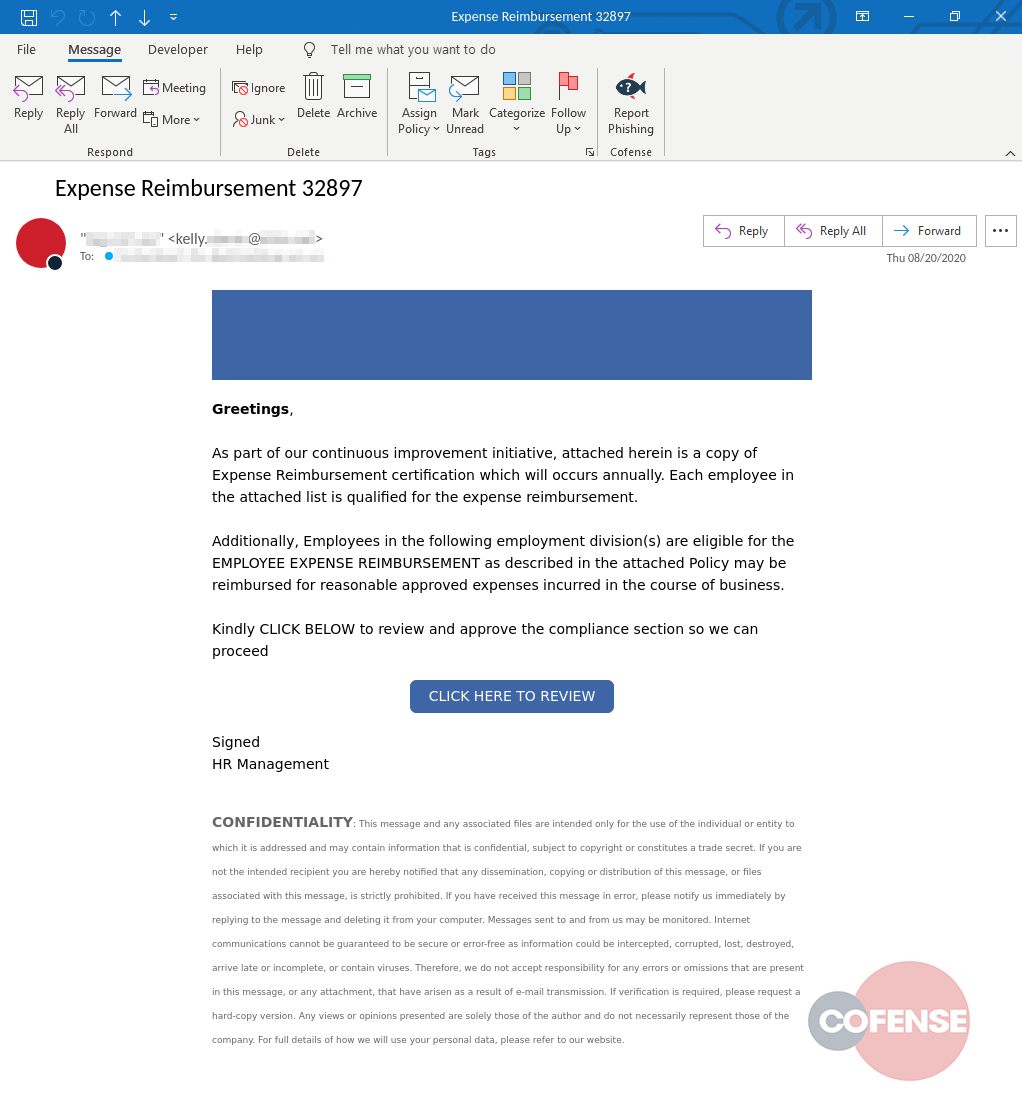
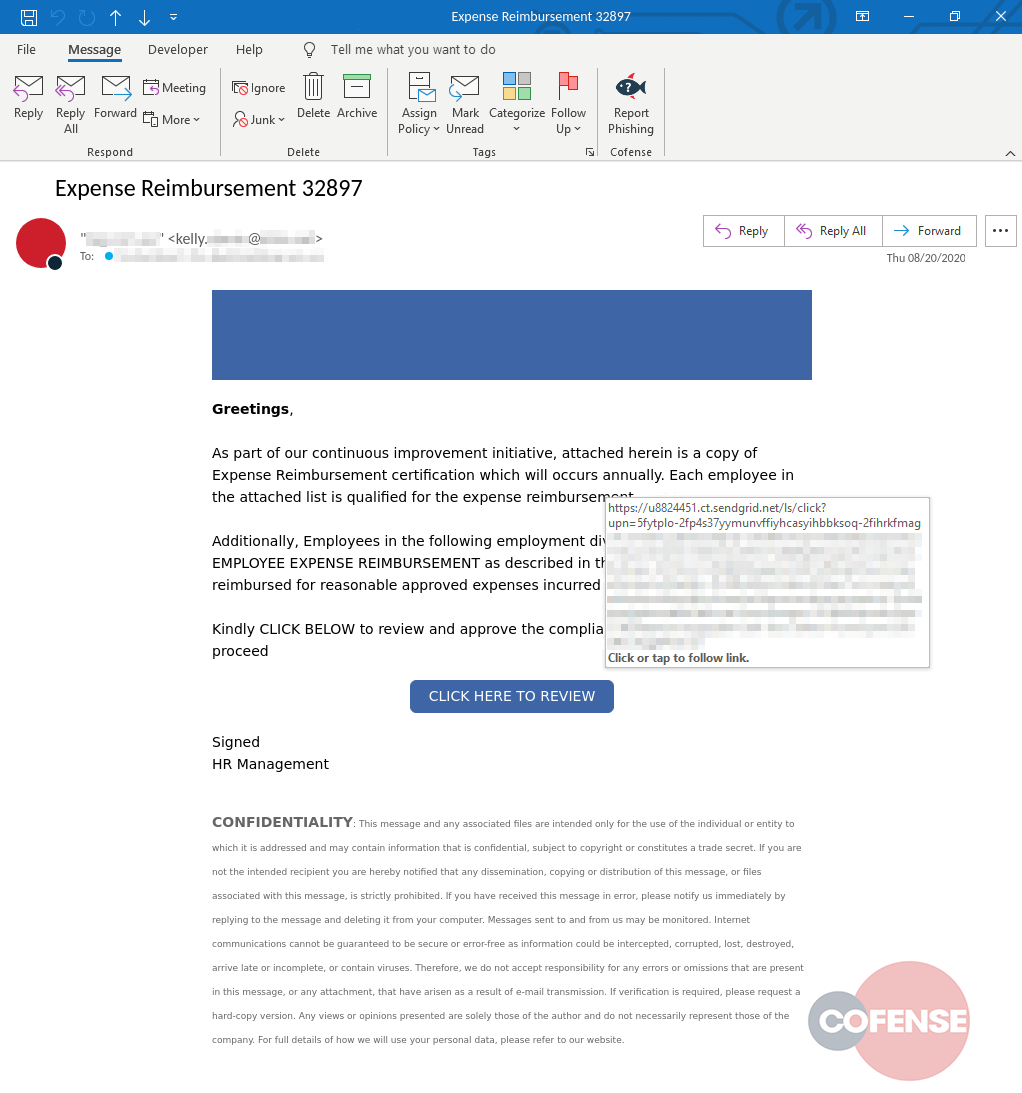
The email body continues to explain the reason for this email, and mentions an attached file with expense reimbursement certification, list of qualified employees and attached reimbursement policy. Although there is no attached file, the email contains a button “CLICK HERE TO REVIEW” with a hyperlink to take the recipient to the phishing landing page.
The first thing the recipient will notice is the nickname field displays their company’s name. This will make it appear as if the email originated from within the company to put the recipient at ease about its legitimacy. However, the real sender can be seen right next to it. In this case, it was sent from a compromised account. The “Expense Reimbursement” subject also indicates conversation that would happen between a user and finance to further help with the credibility.
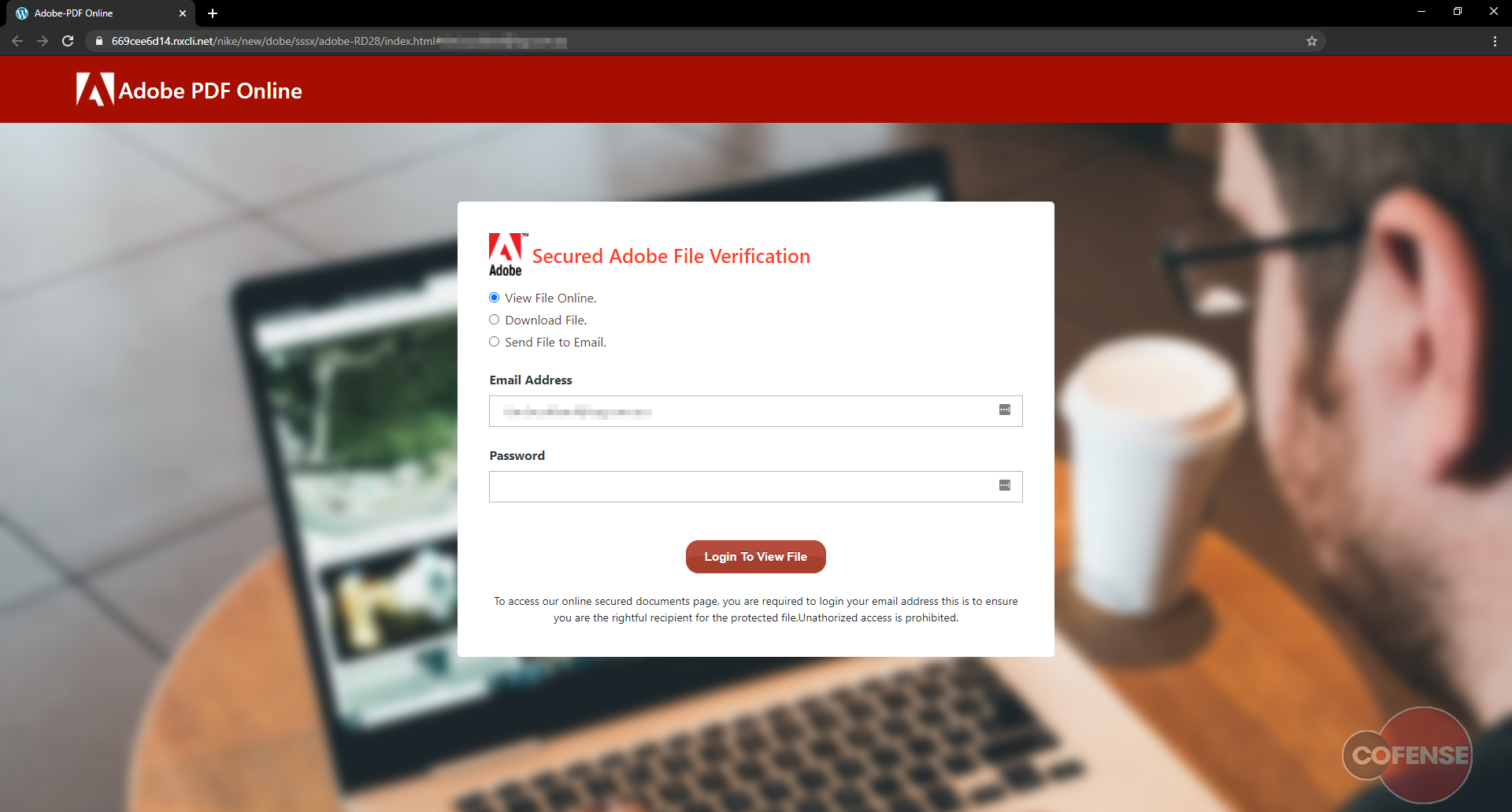
Upon clicking the button found in the email, users are redirected to the page shown in Figure 3. At a glance, it appears to be a login page for Adobe, offering the user options to view, download or send. Note that the email of the recipient is already filled out; the only field left empty is for the password. Despite all these attempts to appear legitimate, this is not the real Adobe login page. The URL in the address bar is not Adobe.com and this isn’t the typical Adobe login users would normally see or receive.
| Network Indicators of Compromise | IP |
| hXXps://u8824451[.]ct[.]sendgrid[.]net/ls/click?upn=5fYtplO-2FP4S37YYMUNVFFIYhCASYIhBbksOQ-2FihRkfMagXRLczMdDWyGKLdaZ2fGhDy-2F2d9wvh3PmFD5Sd8Ylj1giWERtRpL-2BYsNOHEY5W-2BBEnizS435nr7Iu6j9LQ83iSwjaVHWuQCdmZsBXdcJvA-3D-3Dso-6_92JbB3bEppNSos0IRm49Wrp0NXARSmPYQFezDWMyIFHQkj2X-2FV88He6bzn3ZQbN4zh3Px7vCRVXXJQVUHQKFM6tWC6htmDfIm2iAnxbxF4QYUCwxdxpxyJXzJnEiiVU-2B4RBPNQjJGDMSdA8h3kr8CxAU7MmcKmgZO-2F1dJRFBqLVw6c45Gn27jKYlDGmJUCIAsGGZAJhw-2B0-2Frp-2B9eu1VCNrNiXpM353O-2Fk1OfygI64nk-3D | 167[.]89[.]123[.]16 |
| hXXps://669cee6d14[.]nxcli[.]net/nike/new/dobe/sssx/adobe-RD28/index[.]html | 209[.]126[.]25[.]245 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
However, should users continue to enter login details, they are redirected to their company’s site as if nothing happened. And that is exactly what threat actors want. These pointless redirects to legitimate documents or company sites have become increasingly common as a way to distract users from the series of spoofed pages and/or actions they have just taken.
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here