An End-to-End Approach to Next-Gen Web Application and API Security
It was almost 10 years ago that Marc Andreessen wrote that software is eating the world. It is still true today, but I would be even more specific and say that web applications and APIs are eating the world. Our businesses run on web apps and APIs, and their ubiquity means that securing them has become a bigger challenge than ever before, as I explained in my QSC USA 2020 presentation “An End-to-End Approach to Next-Gen Web Application and API Security.”
Introduction
From Verizon’s 2020 Data Breach Investigations Report, we know that web applications are both the top hacking vector and data breach pattern. This is probably for the simple reason of their prevalence and availability to be probed for weaknesses. A vulnerability in any small or seemingly insignificant web app or API can potentially serve as an entry point for intrusion into your network.
Securing your web applications and REST APIs starts with knowing what you have. All organizations have apps and APIs in production, both Internet facing and internal. Some may be hosted in the public cloud, and we know that the cloud providers and not responsible for the security of your application code. Some are probably vendor-supplied apps whose security posture is unknown to you. Then of course, since software is eating the world, new web apps and APIs are being built on a continuous basis. Security must be considered here, but testing can’t slow down the development process.

The WAS Catalog
Having a good inventory of your web apps and APIs is crucial, and Qualys Web Application Scanning (WAS) can help. In fact, asset inventory has been a major theme at QSC USA 2020. Web apps and APIs are essentially services that function over HTTP and/or HTTPS. The WAS catalog serves as a repository and triaging area for these services that you may or may not know about. The WAS catalog is fed currently by three different sources:
- Vulnerability Management (VM) scans
- VM map scans
- WAS scans
By using the WAS catalog, you may find web apps or APIs that you’re unaware of and are absent from your current inventory. By selecting “Add to WAS Subscription” on any catalog entry, you’ll quickly be set up to launch or schedule a WAS scan against that service. We’ve made significant enhancements to the WAS catalog in 2020 and have more improvements in the works, including a subdomain discovery capability.
Scanning in Development Phase
When it comes to new web apps (and APIs) being developed, it’s important to perform security testing early and to automate that process. As a dynamic scanner, Qualys WAS requires only a running instance of the web app or API to scan it for vulnerabilities. We provide plugins (“WAS connectors”) for Jenkins , Bamboo, TeamCity, and most recently Azure DevOps to help your development teams build scans into their CI/CD pipelines. The plugins allow for unobtrusive security testing and pass/fail criteria to be configured so that pipeline builds can proceed seamlessly unless the scan identifies a vulnerability. Developers can view the scan results and details of any offending vulnerability without leaving their CI/CD tool.
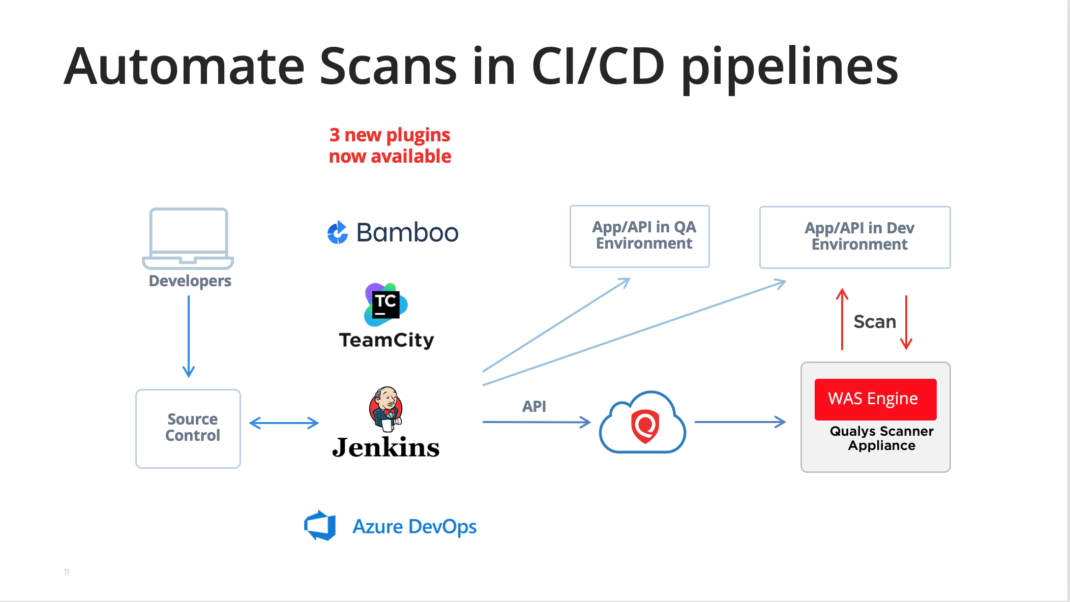
The self-service model is another option to have security testing performed during the development phase. With this model, developers have access to the Qualys UI and are given the responsibility to do vulnerability scans against the web apps and APIs they are building. With role-based access control (RBAC) and tags for dev teams to zero-in on apps they’re working on, Qualys WAS provides everything required. The security team’s role is to administer the program, including answering questions, setting up user logins, configuring scan option profiles, and monitoring scanning activity to ensure scans are being done. We have published the Qualys WAS Self-Service Model white paper in case you are interested in a more detailed explanation.
Scanning REST APIs
Scanning REST APIs is an important capability of Qualys WAS. Unlike with a browser-based web application, the concept of crawling an API does not exist. The scanner needs to be given details about the API to know how to properly invoke the API calls and test the endpoints for vulnerabilities. In 2017, WAS added initial support for API scanning by allowing customers to upload a proxy capture file containing the API calls (HTTP requests) for the various operations supported by the API.
In 2018, we simplified the setup by adding support for Swagger version 2 and making it unnecessary to provide a proxy capture file. In 2019, we significantly increased the power of WAS’ API testing capability by implementing support for Postman Collections. This enabled, for example, defining a workflow within the API, such as having the output of one API call be used as input in another. It’s similar to how Selenium scripts are used to have the scanner navigate through a workflow in a web application. This year, we added support for OpenAPI version 3.
Qualys Browser Recorder and TOTP
Speaking of Selenium scripts, we’ve recently released version 1.2 of the Qualys Browser Recorder (QBR) browser extension. QBR is a free extension for the Chrome web browser and it also works in the new Microsoft Edge browser. Qualys WAS customers use QBR to record a Selenium script to help the scanner navigate through complex authentication or a business workflow in a web app. The script is uploaded into WAS and played back during a scan.
One of the exciting features in QBR 1.2 is support for the time-based one-time password (TOTP) algorithm. With this, WAS can now authenticate to web apps using two-factor authentication (2FA).
Scanning in Production
If you’re running application vulnerability scans early in the development cycle and vulnerabilities are being quashed before they ever reach production, good for you! However, don’t let your guard down. Apps and APIs in production cannot be forgotten. Once in production, the software is in maintenance mode. Security testing is still important since code changes will almost certainly occur, and changes are oftentimes where vulnerabilities are introduced. That’s because different developers are typically assigned and they aren’t as familiar with the application functionality and code. It’s a lot like container drift. It had been a fully tested and secure application when it was first deployed, but things can degrade over time.
Production apps, whether external or internal, need to be monitored in case new vulnerabilities pop up. Qualys WAS provides the scalability needed to make this possible. With WAS you have unlimited scans and the ability to schedule scans against your production apps and APIs on a daily, weekly, monthly, or quarterly basis. WAS customers are able to easily manage the scanning of thousands of production apps per week using the multi-site scan (aka “multi-scan”) feature. Tags are used to group applications in a logical way and scheduling/scanning is done on a tag basis rather than on a single application basis.
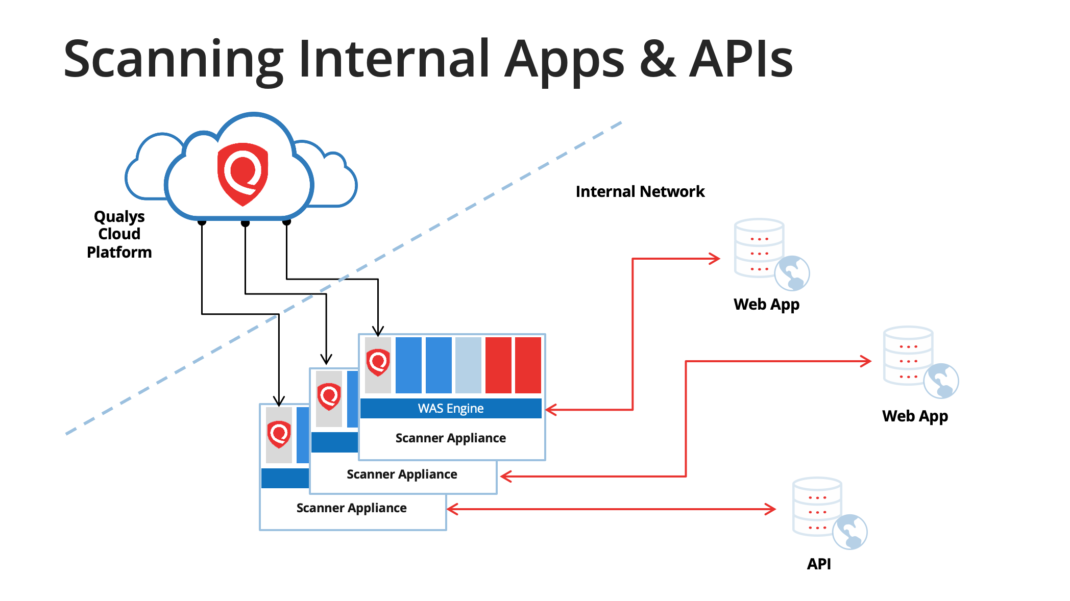
One caveat about scanning production apps and APIs: We don’t recommend running authenticated scans against production apps or APIs. Depending on the functionality and the user’s level of access, production data could be deleted or irreversibly corrupted. If it’s decided to run authenticated scans in production, don’t use an administrator or other high-privilege user account. A read-only user would be safest.
What’s Next for WAS?
In terms of the WAS roadmap, we will be releasing some interesting capabilities early in 2021 to detect defaced websites. It will be a bonus for WAS customers, similar to the web malware detection scans that WAS customers have today.
We are excited about a brand new user interface for WAS coming in 2021. It will roll out in phases, with the first phase being a powerful new dashboard with editable widgets. Customers will be able to try the new UI and switch back to the old UI at any time.
In terms of the WAS scanning engine, improvements and new detection capabilities will continue to be released on a regular basis. Highlights include a vulnerability test for NoSQL injection, fuzzing of GraphQL requests, and a more powerful brute forcing tool for files and directories.
Also in the first half of 2021, WAS customers will see useful integrations come out. Integrations with the CyberArk authentication vault, ServiceNow Application Vulnerability Response (AVR), and GitLab CI/CD are planned.
The WAS roadmap for 2021 also includes support for the OWASP Application Security Verification Standard (ASVS), including a report specifically around ASVS Level 1 compliance.
This post was first first published on Qualys Security Blog’ website by Dave Ferguson. You can view it by clicking here

