3 Ways to Hunt for the ZeroLogon Vulnerability on Your Windows Servers
Vulnerability assessment and patch management can be painful time-consuming processes. From the Security team looking at vulnerability reports and prioritizing the riskiest ones for their environment to the IT or Infrastructure team determining exactly which machines need to be patched and successfully deploying the patches, it’s a tireless cross-team effort.
Over the past year, Carbon Black’s Threat Analysis Unit (TAU) has been working to simplify and expedite this process by building and deploying live queries for our users. These live queries, which are sent directly to the devices themselves to pull back artifacts about the current state of each device, show up on the Carbon Black Cloud console as pre-built, recommended queries that can be run against one device or your entire fleet with the click of a button. The query catalog now features more than 90 recommended queries to help administrators track down rogue USB devices, unwanted browser extensions, misconfigured device firewall and RDP settings, and more.
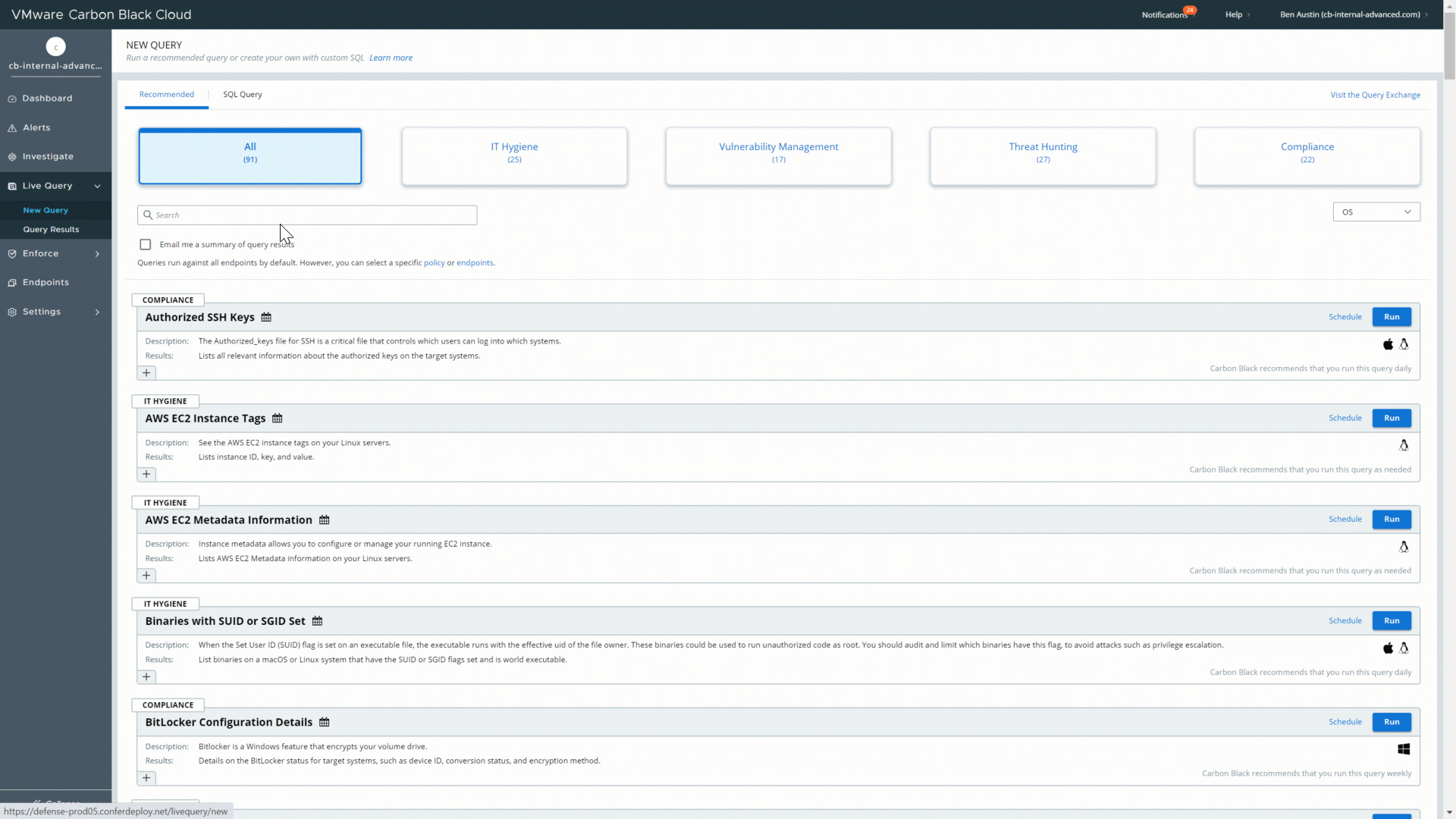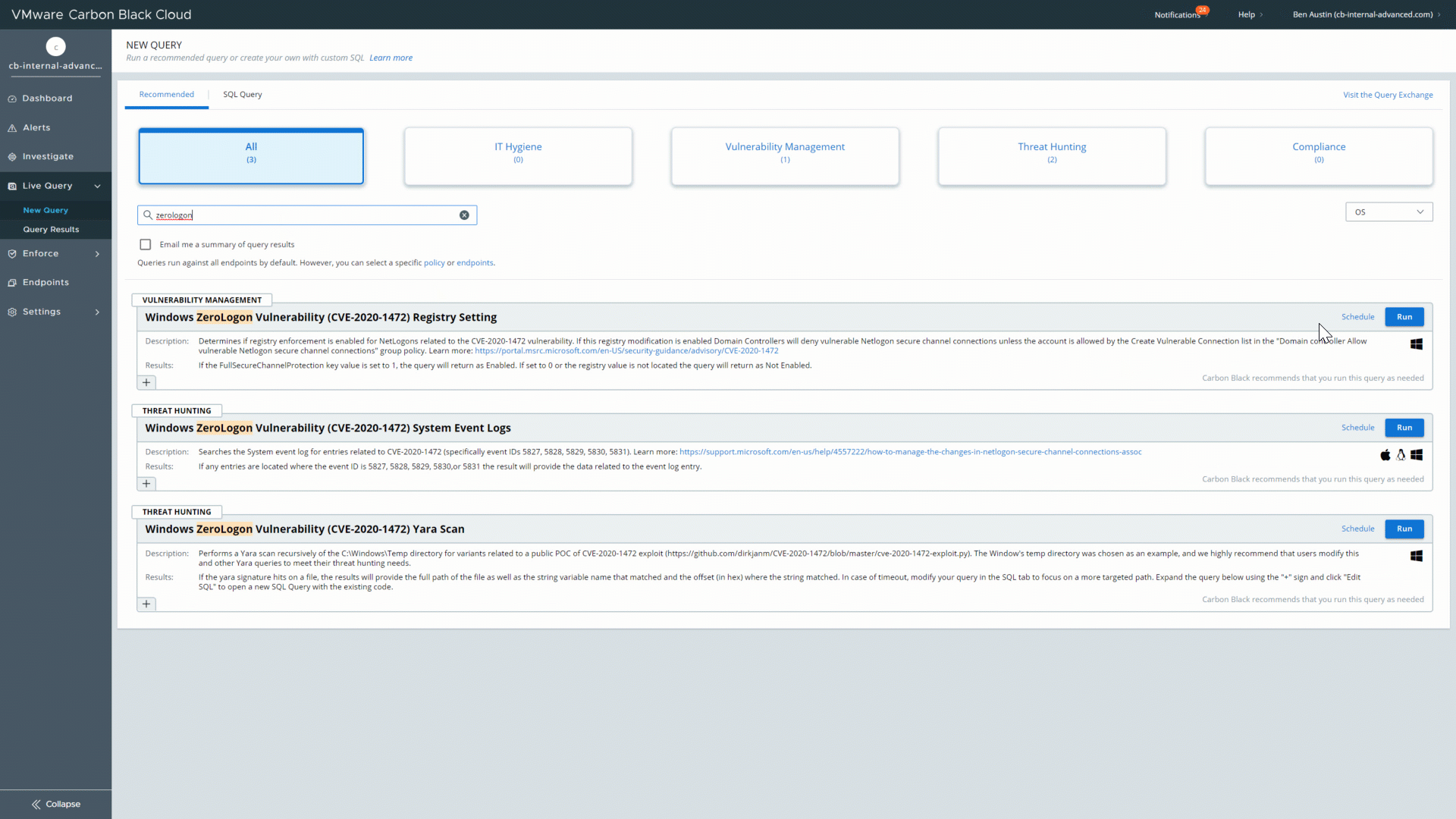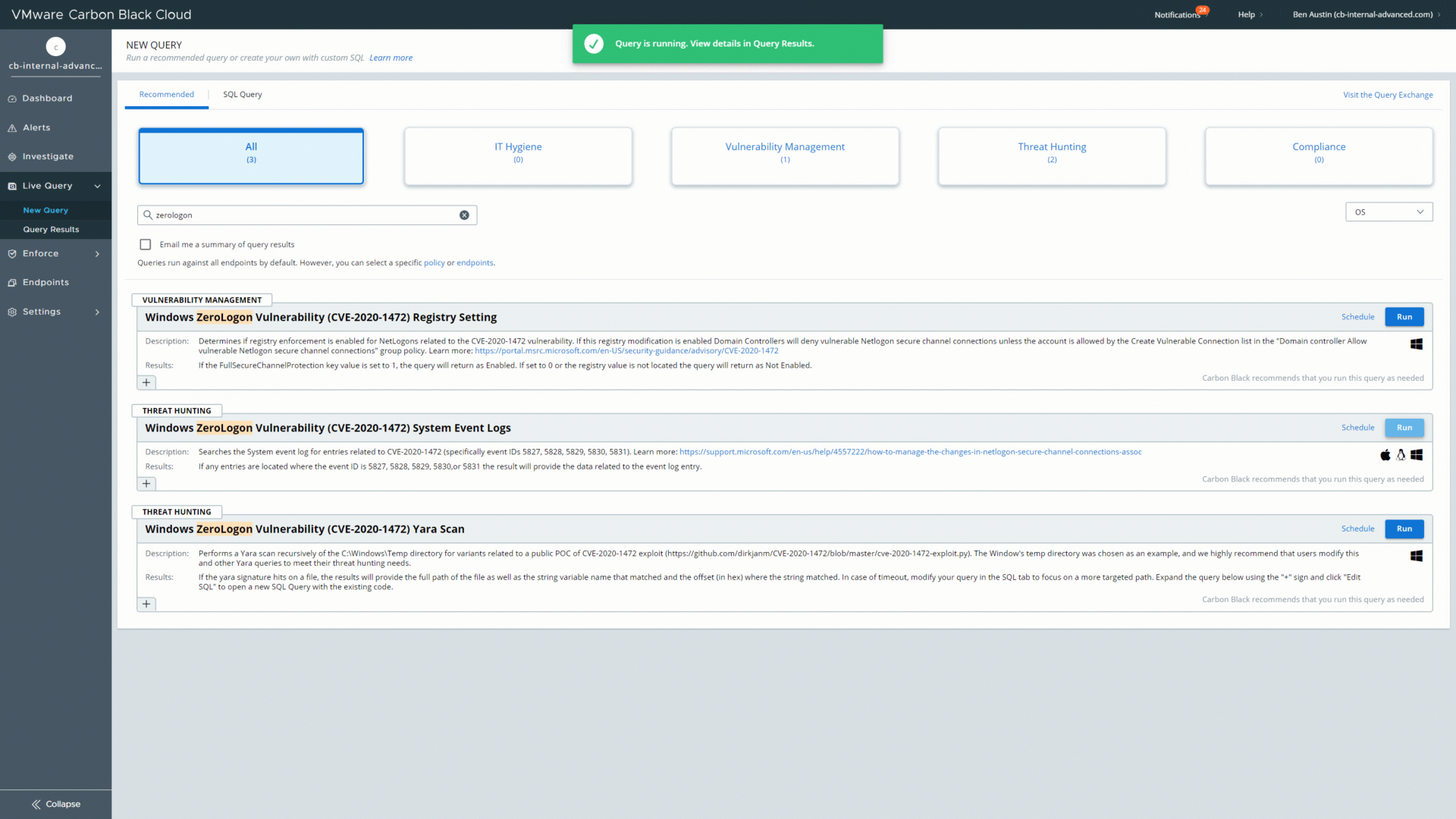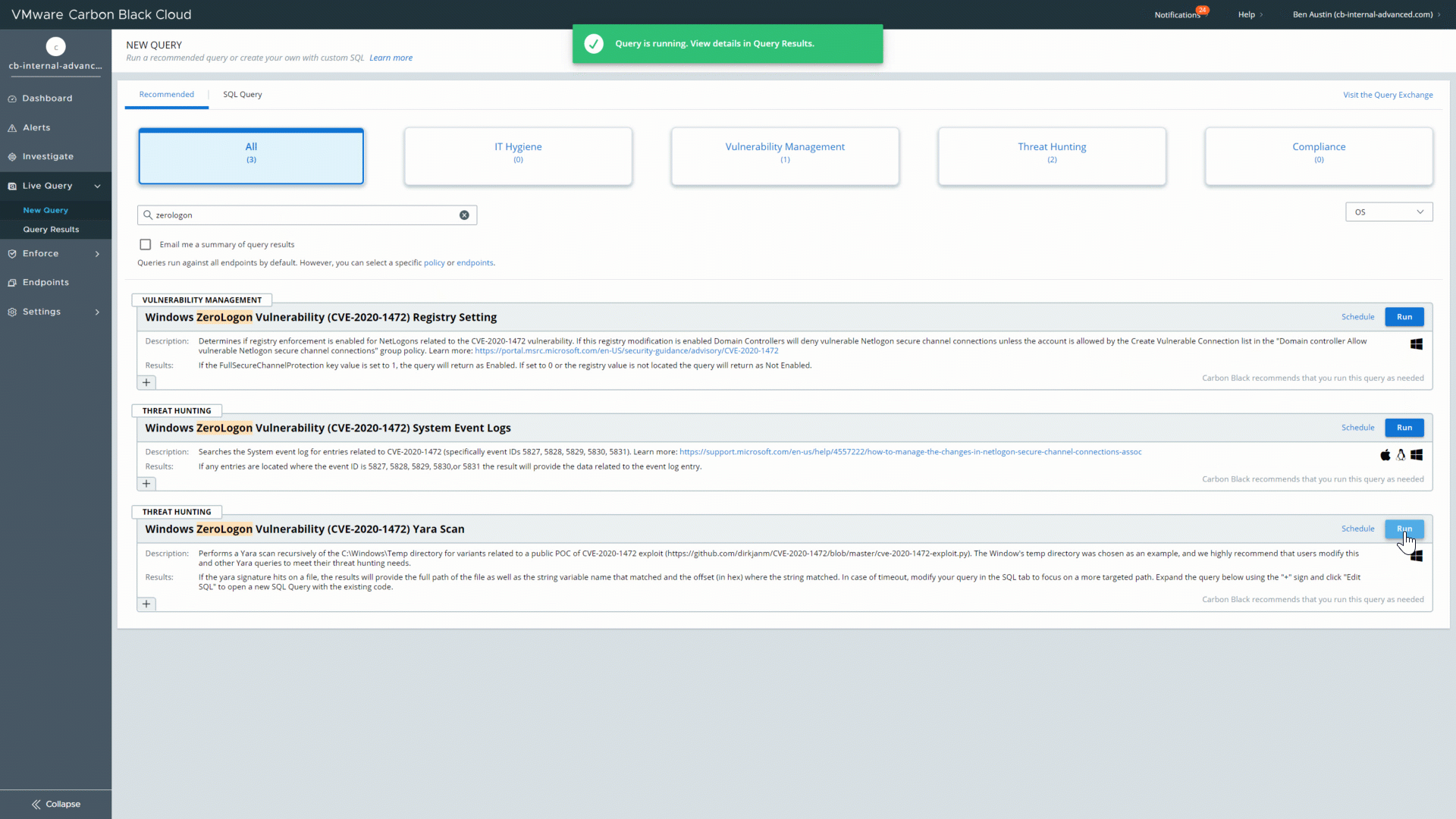
Previously, the TAU team published a live query that helped users uncover the Windows CryptoAPI Spoofing vulnerability that was originally announced in January. Now, as part of the Carbon Black Cloud’s most recent update, we have added three queries that help users hunt for indicators of the Windows ZeroLogon vulnerability (CVE 2020-1472).
About ZeroLogon (CVE 2020-1472)
This vulnerability, which was originally announced by Microsoft in August with a “critical” severity rating, could allow an unauthenticated attacker to gain admin access to a Windows domain controller. The vulnerability impacts the Netlogon Remote Protocol in the majority of supported Windows server versions ranging from Server 2008 to Server 2019.
In September, as reported by Krebs on Security, the U.S. Department of Homeland Security released an emergency directive stating that they were believed there were active exploits in the wild and instructing all federal agencies (and strongly recommending state and local governments) to patch the vulnerability within a matter of days.
Even with a vulnerability this severe, the reality is that many organizations still will not have found the time to prioritize assessing where this vulnerability could exist in their networks and deploying the patch. This is why our TAU team took the time to develop three separate ways for users to query their Windows servers to audit their systems for configurations and indicators associated with this vulnerability. And while the queries described below are only available in the Carbon Black Cloud console, your team could also follow the same discovery techniques manually or through a separate query tool deployed in your environment.
Registry Setting
The first of these queries reach out directly to your organization’s Windows servers to determine if the Microsoft-recommended registry setting has been enabled on the target system. This registry key is used as an indicator to help you confirm whether the necessary update has been applied to enable enforcement mode. The results from this query will clearly show whether each server has it “Enabled” or “Not Enabled.”
System Event Logs
This query takes us a little bit away from vulnerability management and more toward threat hunting for indicators of compromise (IOCs) associated with the vulnerability by searching the system event log for entries related to ZeroLogon. The specific event IDs that the query searches for are listed in this Microsoft support document. If any event log entries match those event IDs, the query results will provide you with the necessary context related to the entry.
Yara Scan
This final query, which is also hunting for IOCs, automatically performs a Yara scan of the servers to look for variants related to a public ZeroLogon exploit. This query specifically scans the C:WindowsTemp directory, but it is recommended that users modify the query to scan other directories based on their own threat hunting needs.
Running these three queries in your environment provides both Security and IT teams with information about which machines may currently be vulnerable, as well as a look back to uncover any indicators that your organization has already been attacked using this vulnerability. This means that, with only a few minutes of work, you could confidently report to the leadership within your organization about the status of this critical Microsoft vulnerability across your entire environment.
See also:
Querying Windows Event Logs for Faster Investigation and Response
Using Live Query to Audit Your Environment for the Windows CryptoAPI Spoofing Vulnerability
How Live Query Helps with Vulnerability Assessment
The post 3 Ways to Hunt for the ZeroLogon Vulnerability on Your Windows Servers appeared first on VMware Carbon Black.

