Windows Event Streaming Using FireEye Endpoint and Helix
Gathering Microsoft Windows event logs is a critical function of most SOCs. The wealth of information available on endpoints makes ingesting logs into a SIEM a top priority. The legacy export model included using third-party tools such as NXLog to take logs and ship them off to the SIEM. This meant installing yet another agent on your endpoints and dealing with the ever present agent fatigue.
Here at FireEye, we knew there had to be a simpler way to get these valuable logs into the SIEM. Today we are pleased to introduce Event Streamer, a native event streaming functionality in our latest Endpoint Security agent that—working with Helix—allows teams to consume these valuable logs in a low friction way.
What Is the Event Streamer Module?
We introduced our Innovation Architecture in May to bring new functionality to the Endpoint Security suite without having to wait for major releases. This allows both FireEye internal teams and customers to build modules on top of the controller. The Event Streamer module integrates directly with FireEye Helix to provide a native way to export logs to Helix with little configuration.
The Event Streamer module is available right now on the FireEye Marketplace for download. Let’s take a look at how we can get it installed and start getting logs sent to Helix.
Downloading and Installing Event Streamer
To download the Event Streamer module, head over to the FireEye Market and select Endpoint Security. From there, select Event Streamer and proceed to download the module needed for installation on the Endpoint Security controller.
Once the module is downloaded, proceed to the Endpoint Security controller and navigate to the Modules menu, then head to the HX Module Administration sub-menu. Click on the Install Modules button and select the Event Streamer file that was just downloaded. When installed, the listing under the User Modules sections should show as enabled (Figure 1).

Figure 1: Event Streamer installed and enabled
Before data can be sent to a Helix instance, we need to fill in the token-server. To receive that information, please email [email protected], or reach out to a sales engineer. When the token-server is received, add it to the FireEye Endpoint controller after logging it via SSH using the following steps:
- enable
- co t
- hx server fe-token-service url <Token_Server_URL>
The Event Streamer module is now installed and ready to be applied to a policy. Let’s do that next.
Enabling Event Streaming in an Endpoint Security Policy
We just showed how to download and install the module, but what about actually getting logs to Helix? It’s pretty simple.
Navigate over to the Admin menu and then over to the Policies sub-menu. Choose the policy on which to enable Event Streamer and click Edit Policy. An option to forward Windows event logs to a FireEye Helix instance will be available (Figure 2), and turning it on will enable Event Streamer. Because we are using the native Helix integration, a syslog server or destination does not need to be specified for these logs.
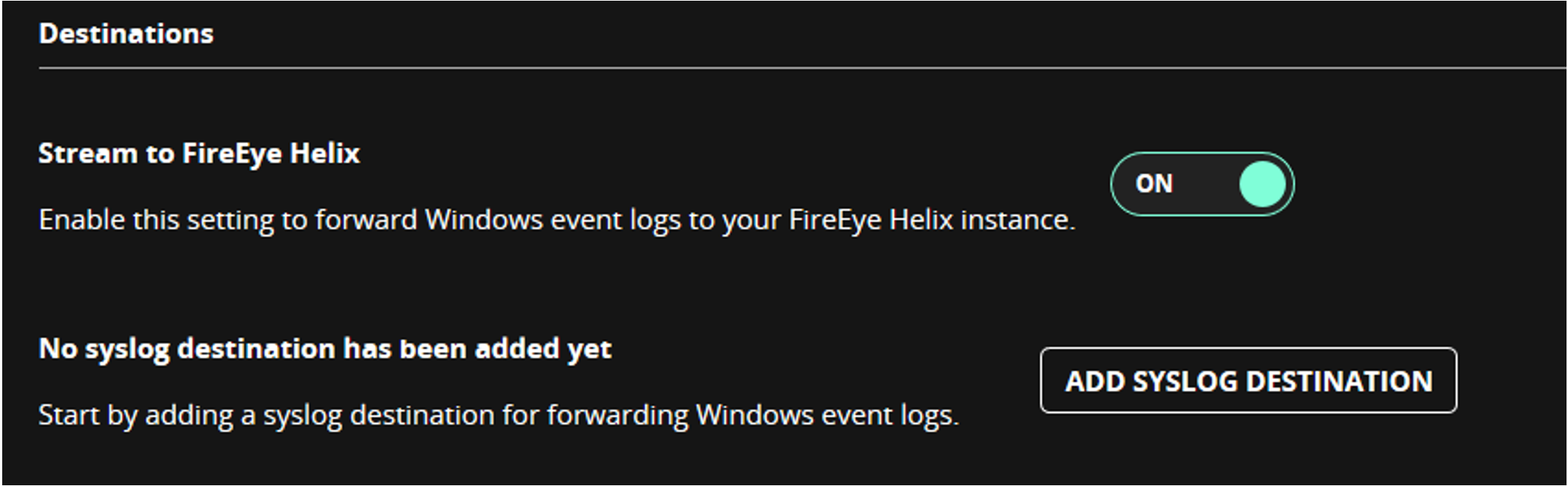
Figure 2: Event Streamer enabled on the agent default policy
Scroll down and you will notice the various slider buttons for event types that can be enabled and sent to Helix (Figure 3). Refer to the Event Streamer user guide for a detailed description of the types of event logs that are encompassed in the various options.
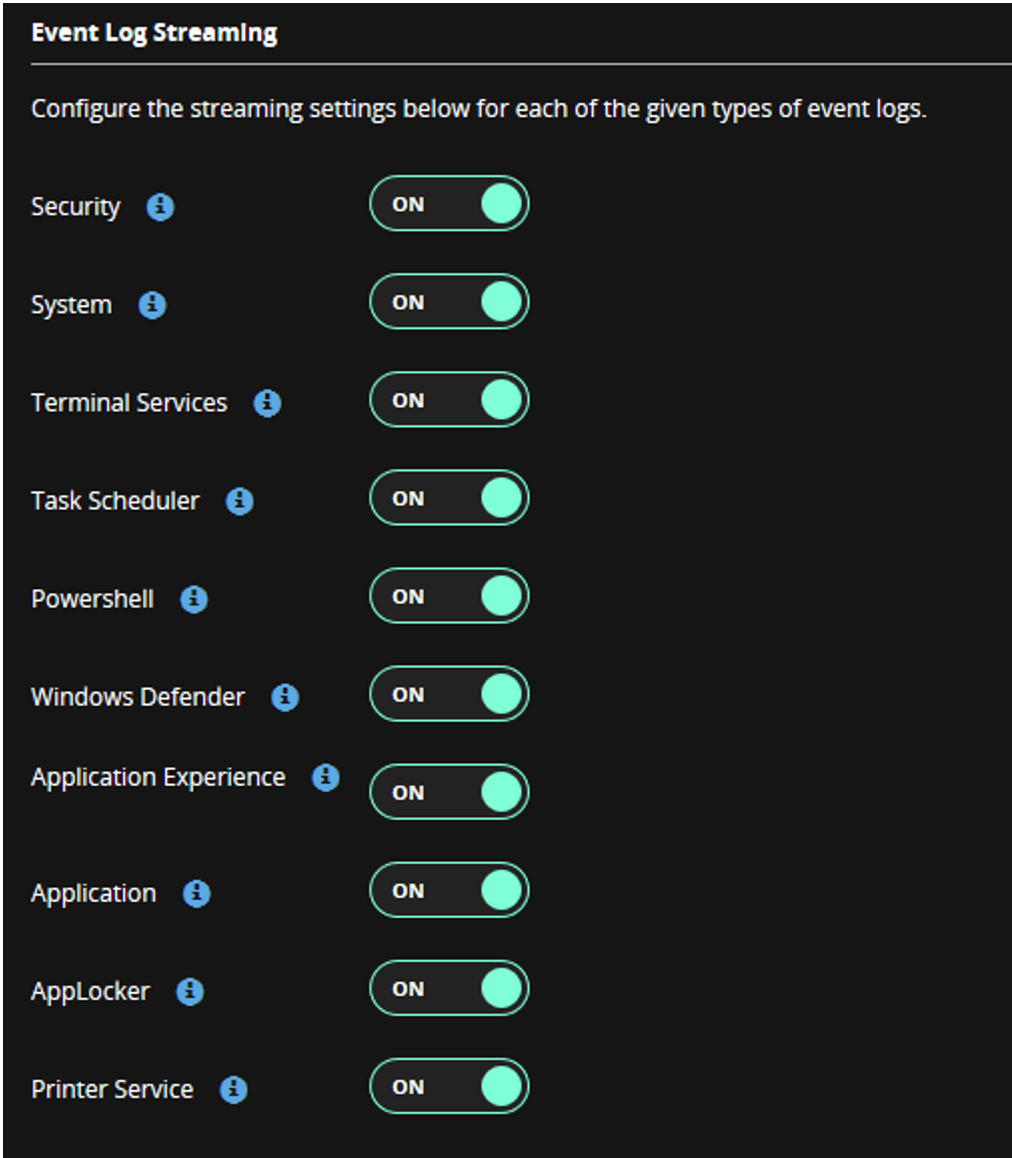
Figure 3: Event Log categories
Windows Event Logs in Helix
After logging into Helix, we will see the newly ingested Windows event at the bottom of the main summary dashboard. The logs are now flowing in, but how do we utilize them?
Helix provides a very rich Windows event log ruleset (currently 348 rules) right out of the box, which enables advanced threat detection. Some sample detections utilizing Windows event logs are shown in Figure 4.
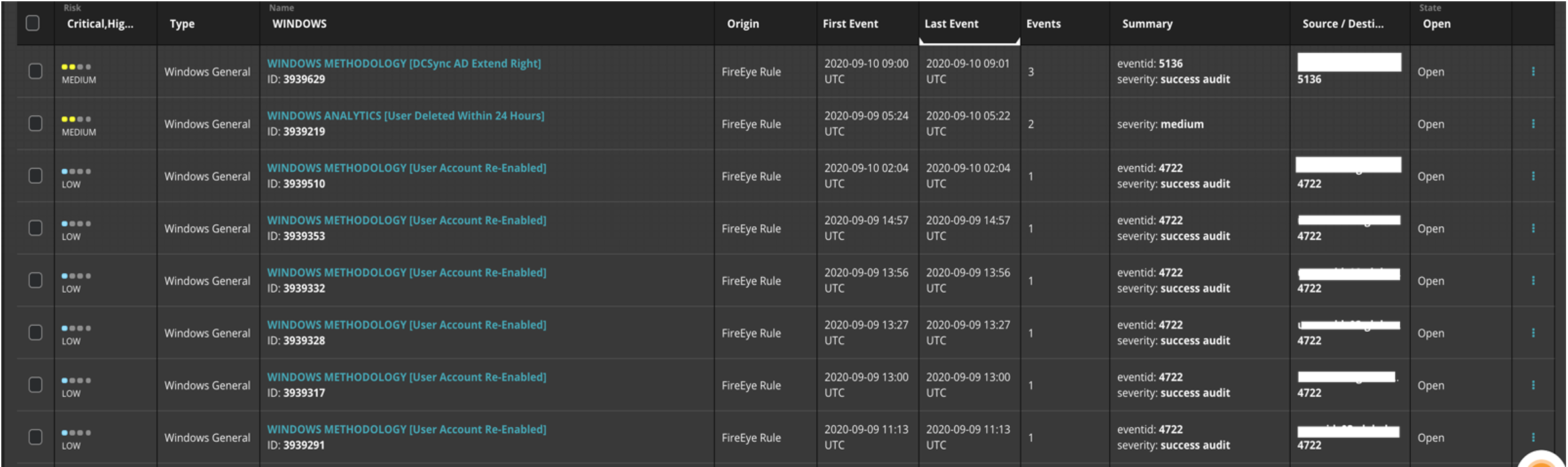
Figure 4: Windows event focused alerts
These alerts serve as a starting point for endpoint-based detection using Windows event logs. In addition to advanced detection, we can utilize the logs to perform some hunting exercises. Performing actions such as identifying endpoints and what domain they belong to with the following query in Figure 5.
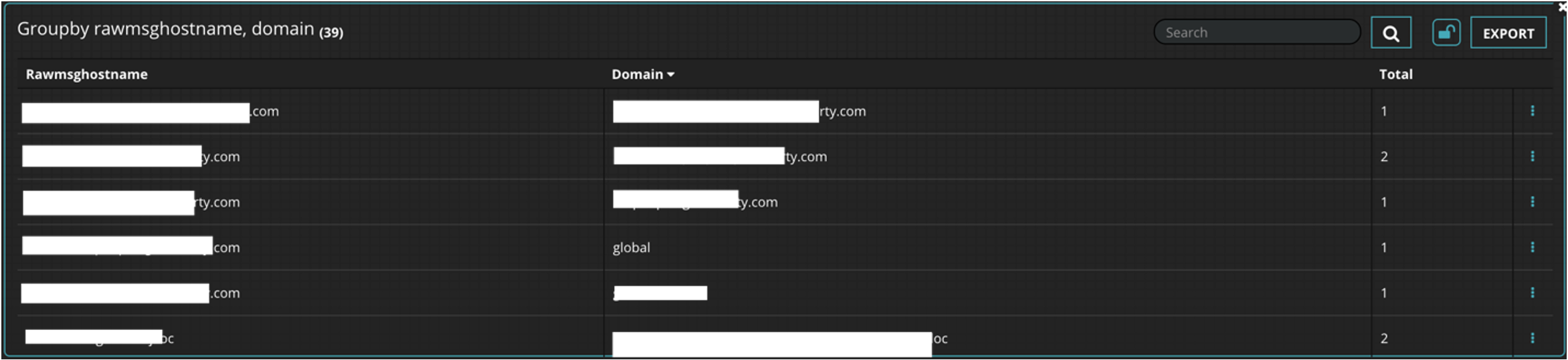
Figure 5: Endpoints with their respective domains
In addition to detection and hunting, reporting capabilities have been greatly expanded for Windows event logs. These prebuilt dashboards help roll up this information and provide graphical reports that suit the needs of everyone from the SOC analyst to the CISO. Custom dashboards can be created to fit the needs of an organization as well. An example dashboard is shown in Figure 6.
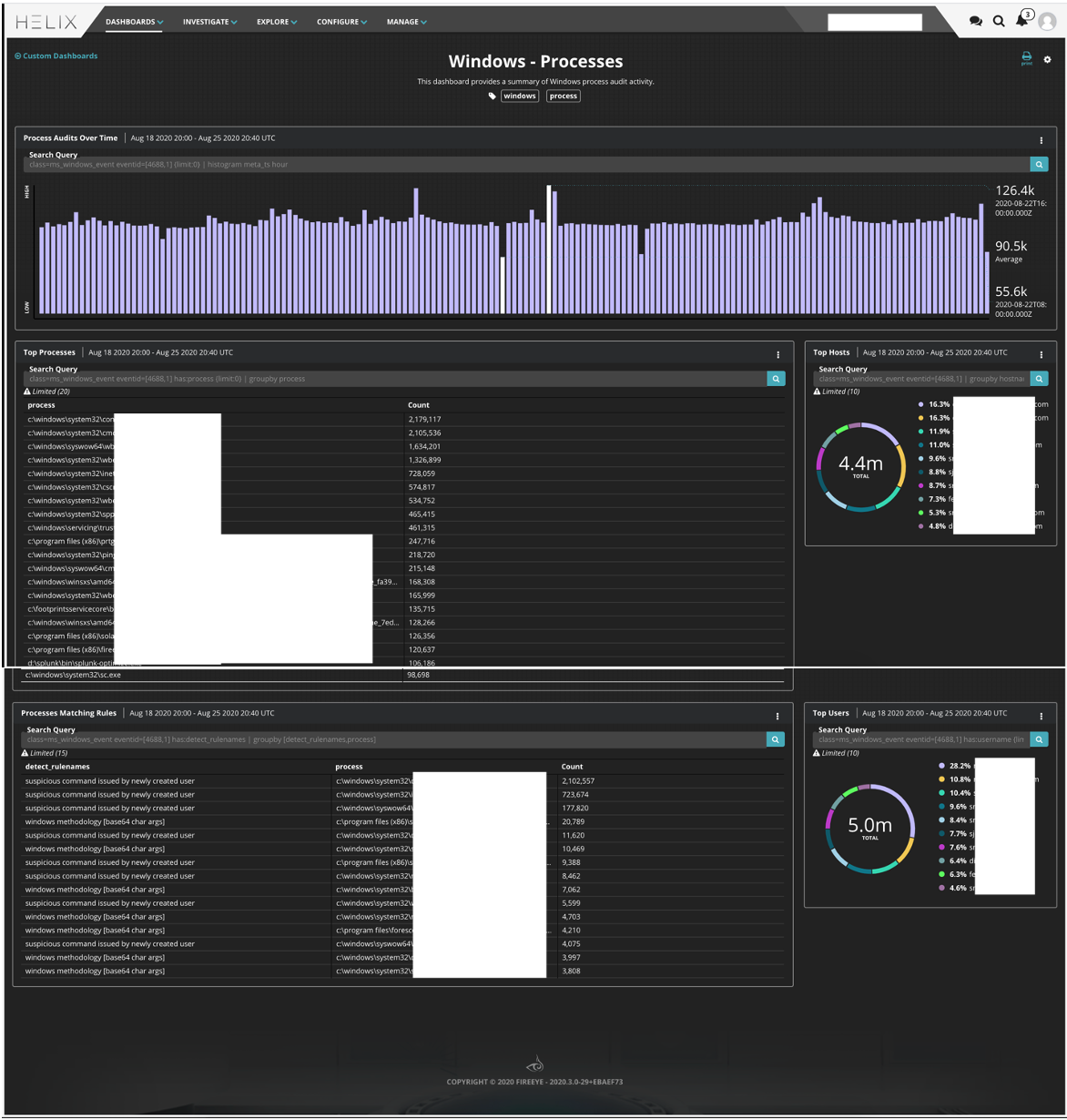
Figure 6: Windows endpoint specific dashboard
Conclusion
Windows Endpoint logs are very valuable when it comes to hunting across endpoints. Traditionally a third-party tool would be required to accomplish this goal, but with FireEye Endpoint Security Suite and Helix, this functionality is now entirely native.
Ready to get started? Connect with us today to see a demo or to learn more. Already using Helix and Endpoint Security, but not familiar with Event Streamer? Reach out to your sales engineer to get more information and a walkthrough of how we can help!
This post was first first published on
‘s website by Tom Los. You can view it by clicking here

