Threat Found: Integrating With FireEye Detection On Demand
Threats can and do come from everywhere, and every organization approaches security differently based on their needs, industry and environment. But the one thing organizations all have in common is a need for intelligence-backed, validated threat detection capability with enough contextual analysis to act on.
With FireEye Detection On Demand, any company can integrate with FireEye’s award-winning detection and intelligence to protect against today’s threats, whether they exploit Microsoft Windows, Linux or Apple OS X operating systems, or application vulnerabilities.
FireEye offers a blend of integrations through its technical partnerships. Customers can integrate their own custom solutions by leveraging the Detection On Demand API with examples and sample code from the FireEye Developer Hub. Security companies interested in adding detection capabilities can also work with us in two ways: OEM solutions tailored to your needs or integrations that allow mutual customers to bring their own license keys to utilize FireEye detection capabilities. Either is available today for file and URL analysis—contact [email protected] to get started.
How Does Detection On Demand Work
FireEye Detection On Demand is a cloud-native threat detection service that rapidly scans submitted content to identify resident malware. It compares submissions to the latest known tactics and signatures of threat actors using static analysis, artificial intelligence and machine learning. FireEye also determines the possibility of secondary or combinatory effects across multiple phases of the attack lifecycle to discover never-before-seen exploits and malware.
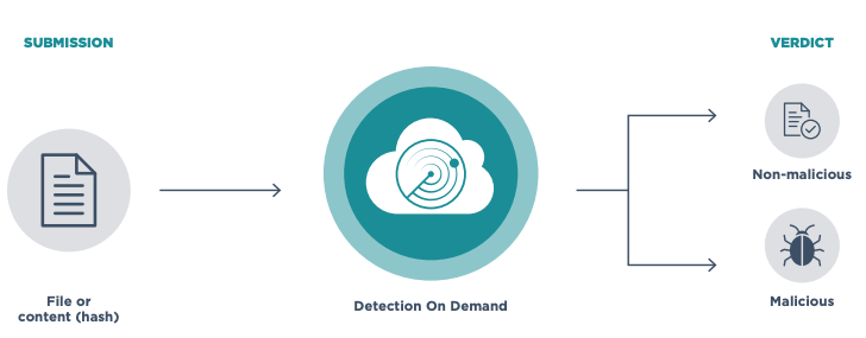
FireEye Report Result
Every malicious file/URL will be returned with a FireEye branded result that can easily be linked from any security tool. Depending on the type of alert, teams will see what that malicious object does upon execution, MITRE ATT&CK mapping, and key information that FireEye knows about the malicious file/URL, including file changes, registry changes, mutexes, process behavior, network traffic and more. Figure 1 and Figure 2 show sample reports.
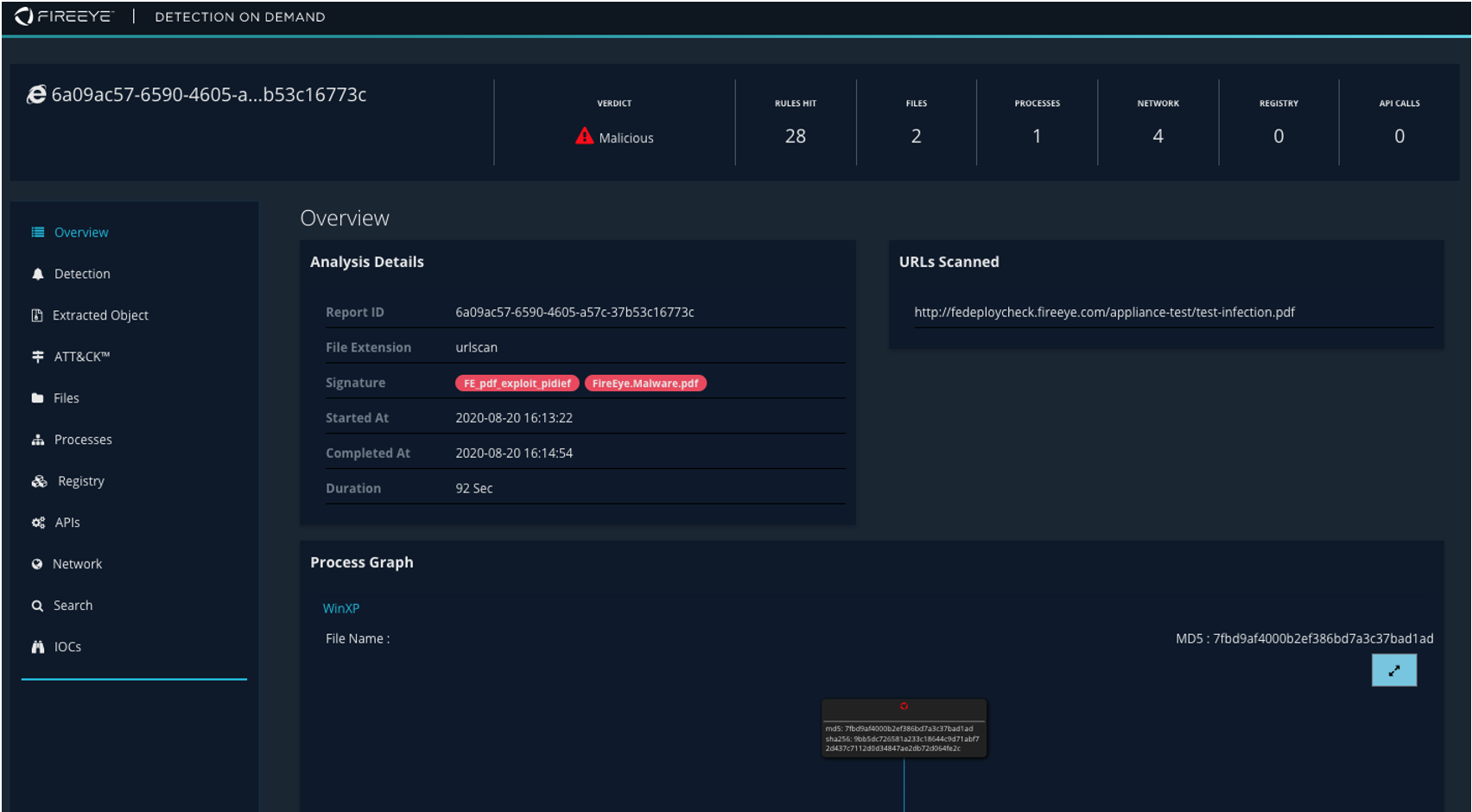
Figure 1: Sample HTML report that can be linked from an application
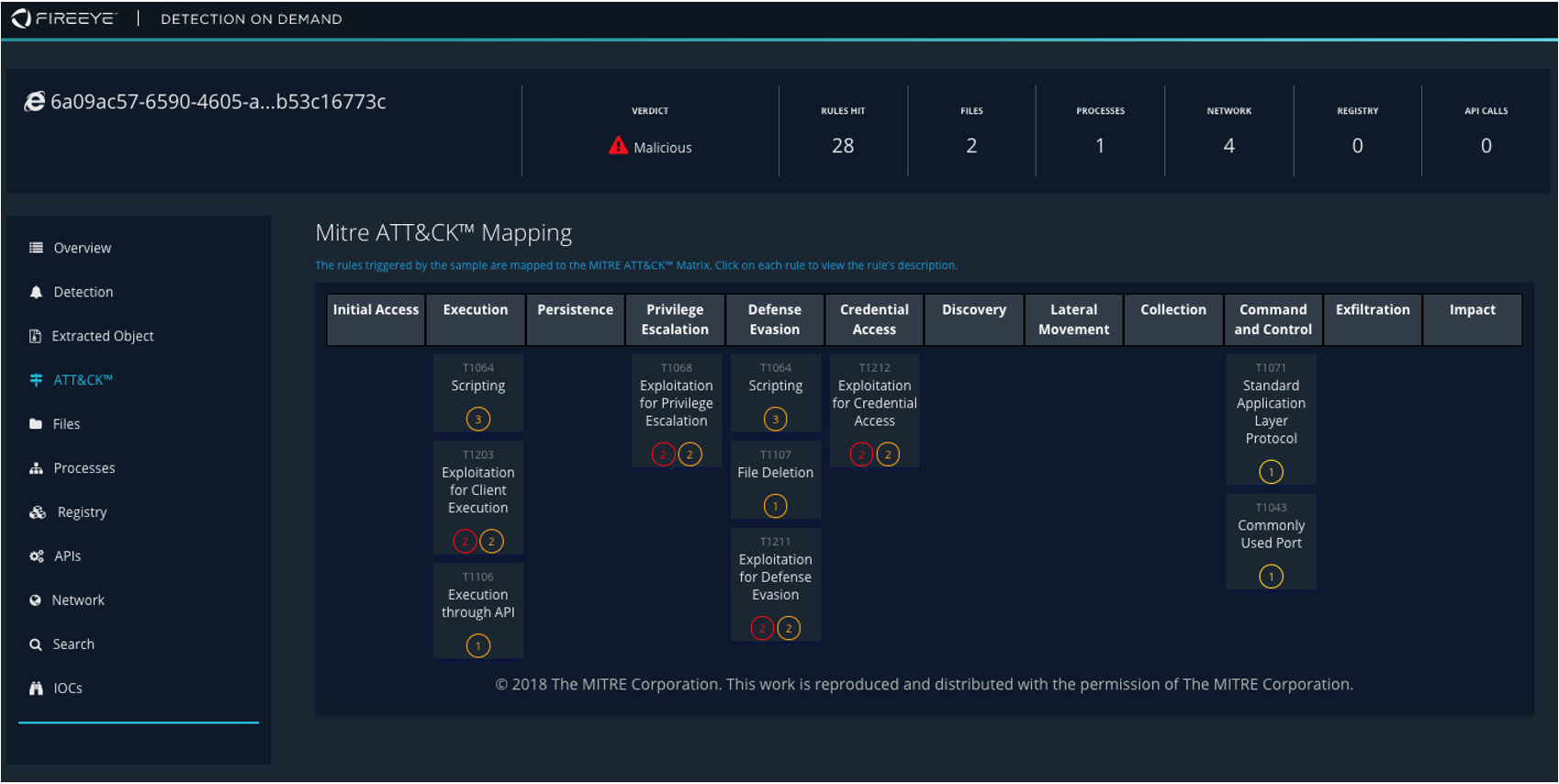
Figure 2: Sample MITRE ATT&CK framework report from a malicious object
How Companies Are Using Detection On Demand Today
Network
Network companies can extract objects from the wire and send them to the FireEye Detection On Demand API. If FireEye detects an object as malicious, the partner can perform various activities such as blocking and notifying the SOC. In addition, IOCs and payloads can be provided to security operation teams with FireEye Mandiant Threat Intelligence baked in.
Cloud Storage
Cloud storage products can scan files and content with the FireEye Detection On Demand API. Malicious files can be blocked or quarantined so that they do not reach the intended recipient. SOC teams can then investigate the incident and respond to the threat.
SOAR/SIEM
Any SOAR/SIEM can benefit from validating alerts with the FireEye Detection On Demand service. A few simple checks can verify if an alert is truly malicious and help SOC teams focus on the biggest threats. The FireEye Detection On Demand service enhances detection and delivers actionable results for prioritization.
Threat Intelligence Platforms
FireEye Detection On Demand nicely integrates into threat intelligence platforms. The FireEye Detection On Demand generates additional IOCs and payload data, which give “context” for domains, IPs, file names and hashes. Security teams using a threat intelligence platform greatly benefit from additional behavior data about threats.
Enhancing Security Tools
Security tools such as virtual browsing sessions, augmented reality for SOC teams and more can be enhanced with FireEye Detection on Demand. Ensuring that all files and URLs are verified by FireEye will help SOC teams focus on the incidents that matter.
CASB and SASE
CASB and SASE solutions can scan all files and URLs in the cloud with FireEye Detection On Demand. On detection, the partner solution is notified of a threat and a customer can select specific logic to handle the threat (i.e. Allow, Block, etc).
Getting Started With FireEye Detection on Demand
- Visit the FireEye Developer Hub for code samples and guides
- Contact [email protected] to discuss OEM or joint integration efforts
- White label or cobranding options available
- Specialized Developer Advocate team to accelerate integration
- Highly competitive pricing to meet unique needs
This post was first first published on
‘s website by Christopher Unick. You can view it by clicking here

