Security Awareness: Choosing Methods and Content that Work
Last week we examined the importance of setting a strategy and goals for your security awareness program.
Part 2 in our 4-part series in support of National Cybersecurity Awareness Month. You can read part 1 here.
We live a fast-paced world of information overload. You have seconds to get your message across to engage your users. You need to choose proven learning methods and focus your educational content on the behaviors that matter most. More than anything, your training must be simple and to the point.
Now that you’ve selected the user behaviors you want to address, the next step is to think about methods and content to nudge users to the correct behaviors.
Simulations Are the Best Way to Teach the Right Behaviors
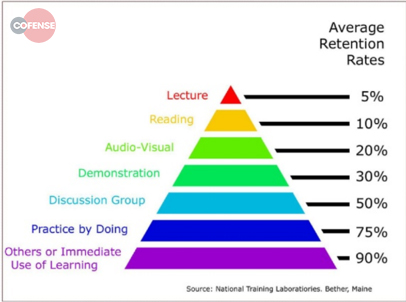
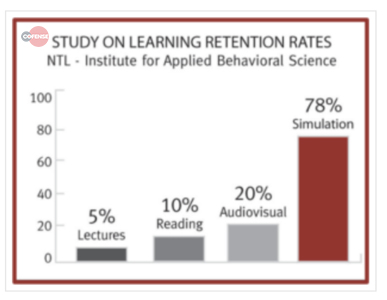
Everyone has a different style of learning and consuming information – video, newsletters, blogs, computer based training modules (CBT), etc. According to the National Training Laboratories (see charts below) people retain more information from simulations than any other method.
Running a simulated phishing attack IS the learning moment. It is not the education presented during the campaign on the website or attachment. This is also supported by the data we see over the years of capturing how long the user stays on the page to read the education. They don’t – the largest segment of users falls in the 0-9 seconds range for “time spent on education.” Yet the data indicates a reduction in susceptibility rate and increase in reporting rate.
After years of enabling companies to run simulated phishing campaigns, we have a vast amount of data to support this method of learning. The experience of clicking and having that “Oh no, what just happened?” moment, is how the recipient learns.
Source: Phishing Report 2019
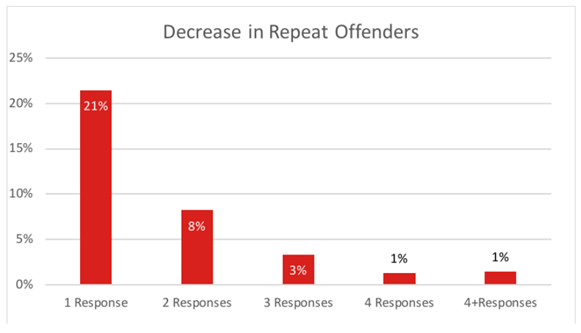
The data also supports the reduction in susceptibility as we look at the number of campaigns it takes to reduce that click rate. When you’re trying to address perpetual clickers, increase the number of campaigns while shortening the time between campaigns. When increasing the number of campaigns, focus on the active threats in order to reduce the risk faster. We first published the chart in our 2015 annual report. In 2019, we ran the numbers again to see if this trend was still the same. Sure enough, the graph still has the same curve.
You will never get to a zero click rate. Phishers are too smart. They craft their emails to look like they’re part of your normal business processes, especially financial transactions. They also constantly change techniques to avoid controls that block their messages.
Focus Your Training on Real Threats
As you start to condition users to report real phishing emails, not just simulated phishes, you’ll want to focus on malicious emails that are getting through the spam filters. In other words, base your simulations on the real attacks your company sees. This will help your users quickly spot the real thing. The goal is to build a resilient workforce that can identify and report potential malicious emails quickly. This drives down the risk to the organization, allowing the security team to mitigate the risk and avoid an incident.
Let’s take one more example of using content to nudge the user to the right path. It’s the example used in last week’s blog on program design—how to change users browsing behaviors. Presenting the user with a simple banner at the moment they’re exhibiting the wrong behavior, we can direct them to take the right action. You can adjust this banner as the behavior changes. Once you curb their habits to click through to unknown sites, your metrics may reveal a category that needs to be addressed – such as software downloads. 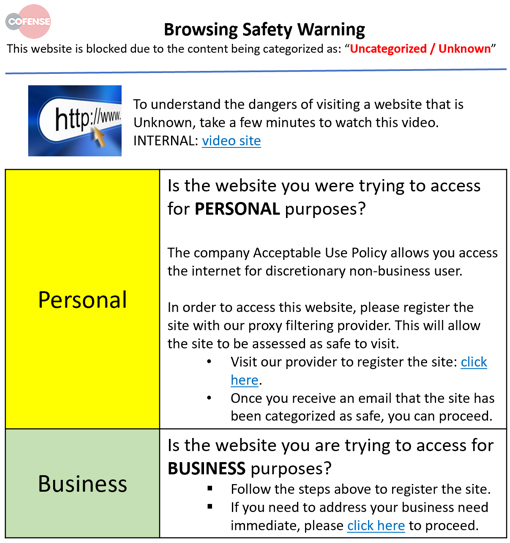
So, what does this all mean when we talk about educational content? If you’re focusing on behaviors that you’re looking to improve, you don’t want to hit users with content overload. Instead, create a plan for covering a theme to each quarter. Use this theme in your newsletters, videos, or learning modules. However, allow for flexibility to shift if a threat is now affecting your organization (HeartBleed, Meltdown, etc.).
In summary, keep your security awareness content simple with clear direction—and even better, fun and engaging—and you’ll soon be able to experience a shift in behavior!
Cofense recognizes that you have regulatory and compliance requirements to provide annual security awareness training to our organization. To help you focus your resources to elements of your program that actually make an impact, we provide a series of modules for FREE to any organization (even if you’re not a customer).
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
Recommended reading: If you’re looking to expand your knowledge on how to create content and simple messaging for your program, I suggest getting a copy of Made to Stick, Why Some Ideas Survive and Others Die, by Chip and Dan Heath.
This post was first first published on Cofense’s website by Tonia Dudley. You can view it by clicking here