Mandatory Internal Company Communications: The Best Time to Phish
Companies are awash with numerous corporate communications: open enrollment notifications, new policies and so forth. With this crush of mandatory emails being sent out, threat actors are given the right amount of noise in a user’s inbox to slide their own attacks in without being heavily scrutinized. They are received as “just another HR email” that users may be hasty to quickly read, sign and be done with. The Cofense Phishing Defense Center (PDC) has observed a new phishing campaign that aims to harvest Office365 (O365) credentials by disguising as an HR document that must be signed.
By Ashley Tran, Cofense Phishing Defense Center
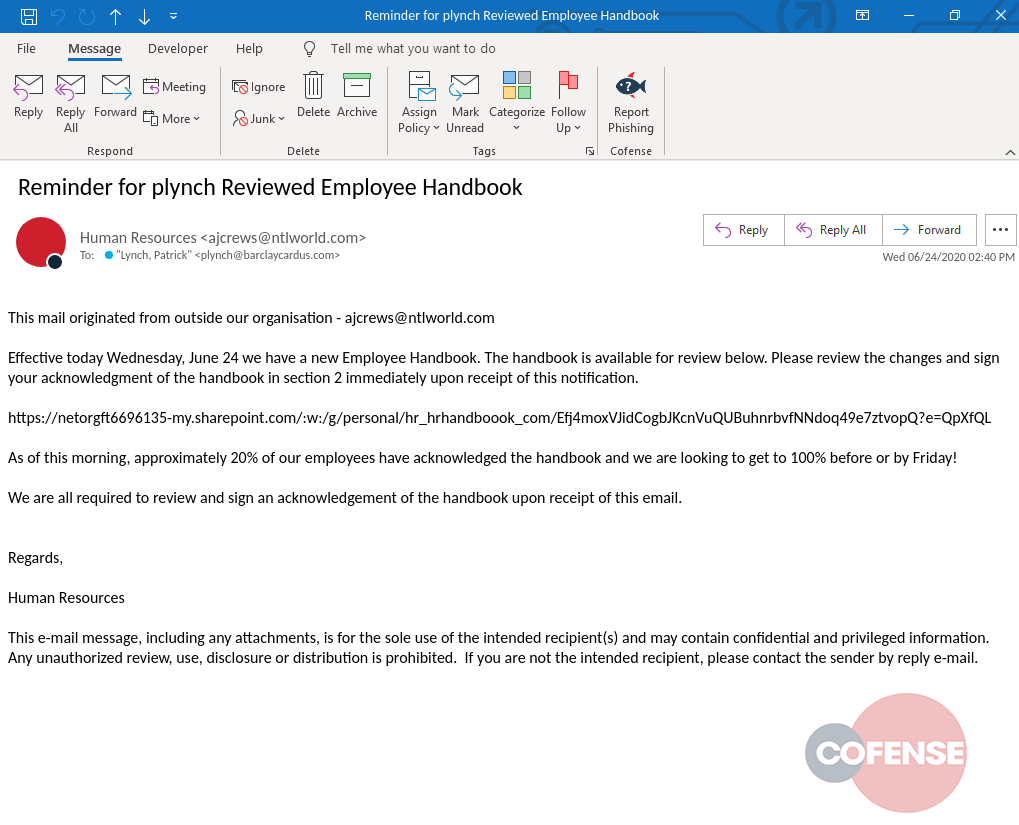
The threat actor has attempted to manipulate the “from” fields in the headers of emails for this campaign. As seen in Figure 1, the threat actor has changed the “sender name” field of the headers to appear as though this email was sent from “Human Resources” when in reality the real sender’s email can be viewed in the field next to it: [REDACTED]@ntlworld.com. Every email for this campaign originated from a unique sender from this domain, which suggests that the threat actor utilized compromised accounts to send out this attack.
Figure 1: Email Body
Within the body of the email, the threat actor has noticeably failed to disguise the URL. In fact, it is clear this supposed handbook is hosted on SharePoint in some way.
The subject for this campaign generally had a theme of “Reminder for [User’s Name] Reviewed Employee Handbook” with the user’s organization email ID being replaced into the subject each time. The context of this email is simple: there is a new employee handbook, everyone must review and sign the acknowledgement of this handbook upon receipt of this email. Interestingly enough, this phishing email was sent out well past the intended due date which simply adds to the urgency of the request – or the threat actor overlooked a variable that needed an update for their template.
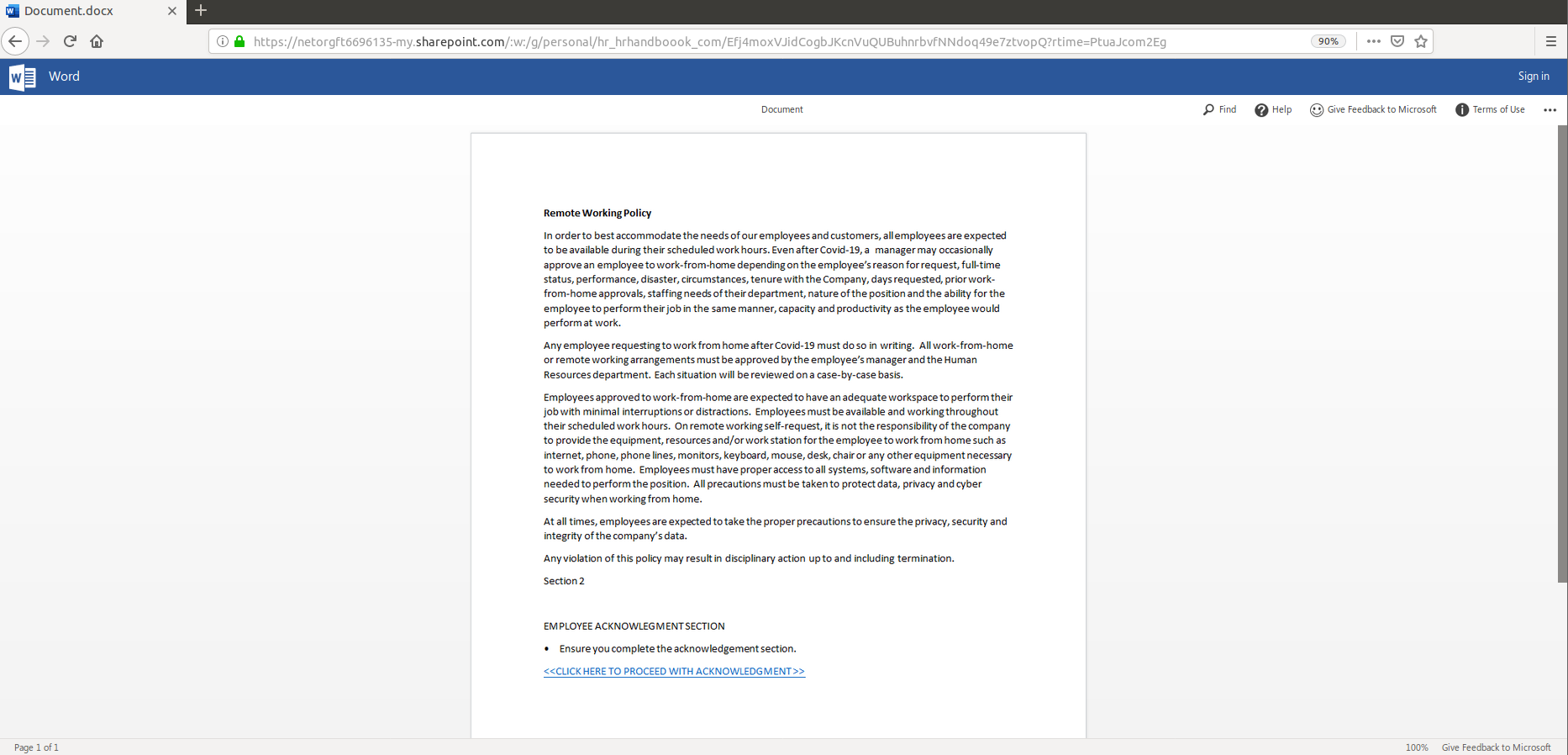
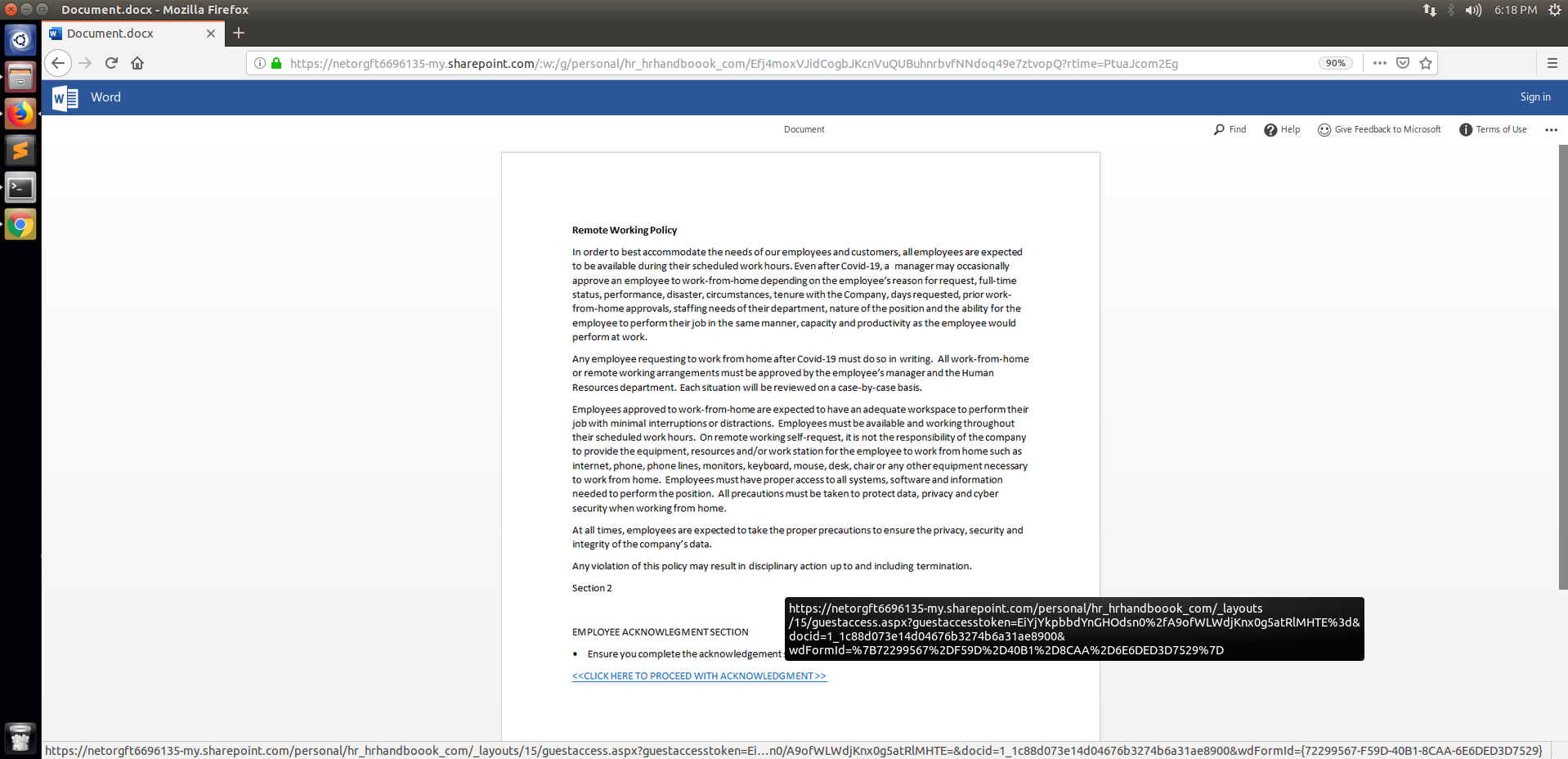
Figure 2-3: Phishing Page
The first step of this attack takes place on a SharePoint hosted document that users are redirected to from the email itself. This document, as seen in Figure 2, looks similar to any page one may see in an HR handbook except this one appears to outline the “Remote Working Policy” for the user’s organization. At the end of the described policy there’s a hyperlink to “proceed with acknowledgement” which, if you hover over it as shown in Figure 3, is simply another redirect to the same SharePoint. Except, this time, it directs to a survey hosted on it.
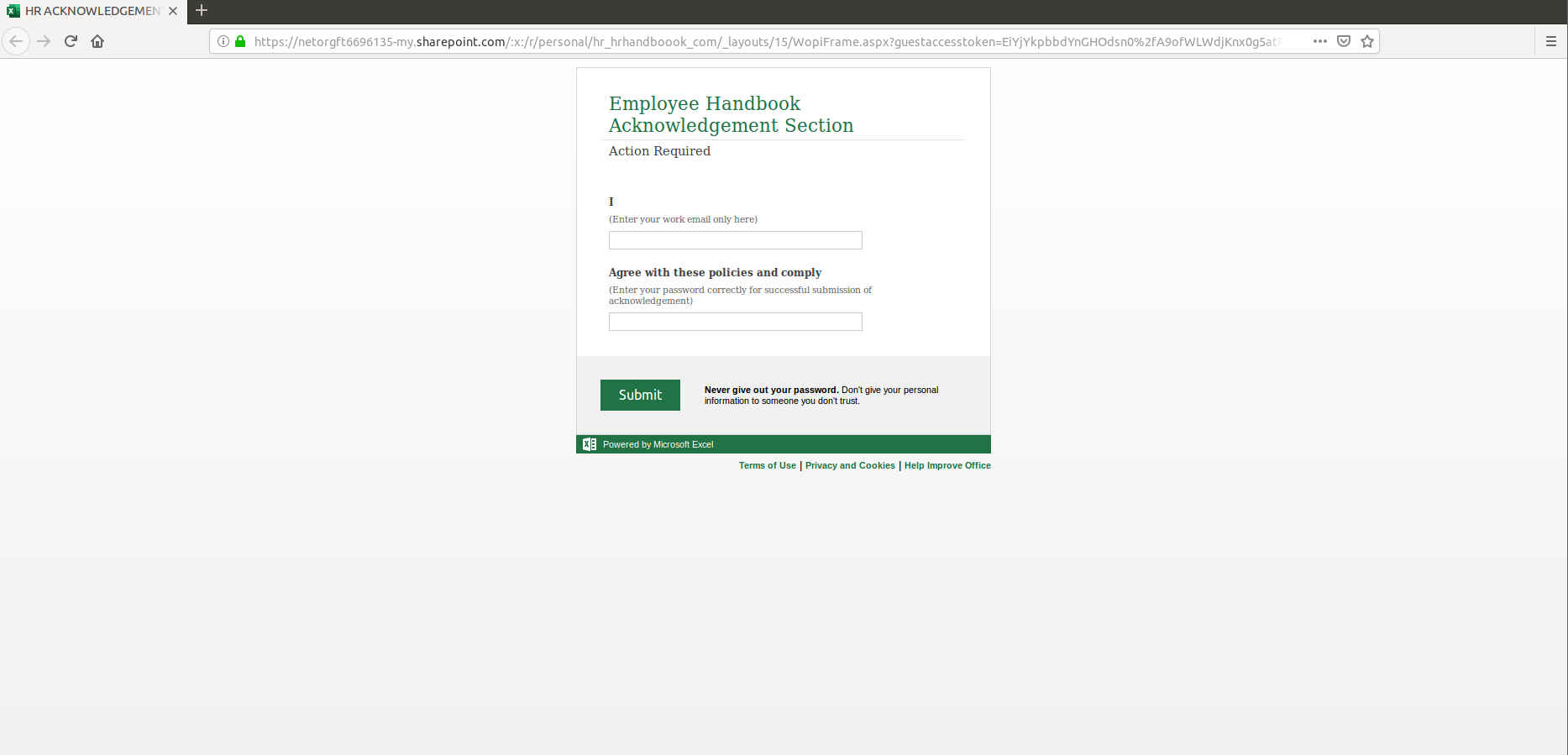
Once users click on the link to presumably acknowledge this new policy, they are redirected to an “Acknowledgement Section” seen in Figure 4. On this page, users are prompted to enter their Microsoft credentials as a way to identify themselves, and “for successful submission of acknowledgement.” The threat actor in this case has utilized the Microsoft Excel web app to create and host a survey to harvest credentials, but this is far from uncommon. In fact, a lot of phish tend to utilize this method, exploiting the fact that these Excel surveys are hosted on SharePoint and leverage the trust most users place in the domain SharePoint.com as a whole.
| Network IOC | IP |
| hXXps://netorgft6696135-my[.]sharepoint[.]com/:w:/g/personal/hr_hrhandboook_com/Efj4moxVJidCogbJKcnVuQUBuhnrbvfNNdoq49e7ztvopQ?e=QpXfQL | 104[.]146[.]136[.]48 |
| hXXps://netorgft6696135-my[.]sharepoint[.]com/:x:/r/personal/hr_hrhandboook_com/_layouts/15/WopiFrame.aspx?guestaccesstoken=EiYjYkpbbdYnGHOdsn0%2fA9ofWLWdjKnx0g5atRlMHTE%3d&docid=1_1c88d073e14d04676b3274b6a31ae8900&wdFormId=%7B72299567%2DF59D%2D40B1%2D8CAA%2D6E6DED3D7529%7D&action=formsubmit | 104[.]146[.]136[.]48 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
Figure 4: Phishing Page
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here