Ransomware Recon — Before the Breach
No one wants to see a repeat of last year’s string of ransomware attacks on municipalities where government services were offline for days, weeks and even months. These attacks cost cities millions in direct costs plus downtime and lost revenue. Ransomware continues to dominate the news and has, in many ways, gone from a nuisance to a business risk.
Part of the reason lies in ransomware actors becoming more sophisticated. Whereas previously they would use an opportunistic or shotgun approach that involved sending myriad lures to non-specific targets, today we are seeing them perform lengthy reconnaissance. This is being done to not only improve their chances of success, but also to determine what they stand to gain by being successful—that is, whether the endeavor is worth it.
Currently, the average time from the first evidence of malicious activity to deployment of ransomware is three days. Meanwhile, the global average time from compromise to discovery (a statistic known as dwell time) is 56 days. This shows that the actors behind these extortions are spending quite a bit of time in an organization’s network, likely gleaning key network topology information (e.g., ingress and egress points such as compromised web servers), backup sources and destinations, crown jewel assets, administration (e.g., KRBTGT, ADFS, Microsoft 365), and other targets for follow-on activity.
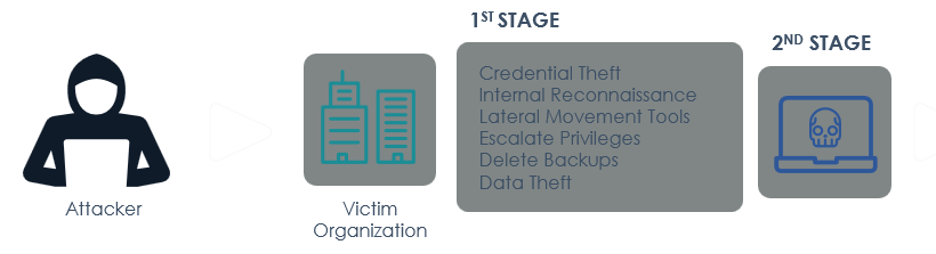
Targeted ransomware lifecycle
Performing reconnaissance leads directly to the next way that ransomware actors are becoming more sophisticated. In years past we would typically see attackers use ransomware to simply encrypt an operating system and network files, but now we’re seeing them exfiltrate key data and destroy backups before the encryption takes place. This makes the threat that much more impactful and increases the likelihood that an organization will pay the ransom.
It also enables ransomware actors to attempt to extort the victim twice—first by requesting payment for decryption capabilities, and again by requesting payment to return or destroy the stolen data. And if a victim wavers about paying the extortion fee, attackers publicly release excerpts of the exfiltrated data to pressure payment. As a result, FireEye has observed a greater amount of extortion attempts and more victims paying the ransom, as well as multiple ransomware attacks taking place concurrently from potentially different actors.
In the next post in this series, we’ll take a closer look at how organizations should be thinking about ransomware protection, with some simple steps to consider on that journey.
FireEye remains committed to helping government leaders stay informed on today’s cyber threats. Learn more about protecting important assets from ransomware attacks, and what can be done in the event of experiencing one, by registering for this September 29 webinar.
This post was first first published on
‘s website by Jon Ford. You can view it by clicking here

