Why Ransomware Targets No Longer Need to Wind Up as Ransomware Victims
But being a target doesn’t mean you’re fated to become a victim. With the deployment of complete and proactive security software, organizations can still defend their data in the face of a veritable epidemic of attacks against their endpoints. At McAfee, this is one of our core strengths.
It was every administrator’s worst nightmare. A small district hospital in western Colorado lost access to 5 years’ worth of patient records after ransomware attackers exploited holes in an aging infrastructure to strike. But it was also an increasingly familiar story as ransomware attackers escalate their attacks and go after targets across all sectors of the economy.
MVISION Insights would help SOC teams know whether their defenses were in shape to protect against an attack. If not, it would offer prescriptive advice about what measures to take before the threat or campaign ever got launched. That is phase number one. Check out MVISION Insights in action.
The best defense starts with prevention. As we like to say, being informed is halfway to being prepared. With MVISION Insights, for instance, customers receive advance notice whenever there are ransomware attacks happening in their sector or region. Take the example of an attack against hospital attack. MVISION Insights will notice an uptick in ransomware attacks against other healthcare organizations and share that intelligence so other hospitals could get ahead of the potential threat and review the state of their own defenses.
McAfee leverages an integrated technology stack that includes machine learning, exploit prevention, behavioral blocking and dynamic application containment. That works to stop not just traditional portable executable files but also file-less attacks.
As an organization goes about the work of hardening its environment, suppose that an APT group then uncovers a loophole. When you have thousands of endpoints, it’s always the case that some endpoint is going to be misconfigured. But before the bad guys can launch an attack, our prevention technology comes into play to prevent ransomware from infecting the endpoint in question.
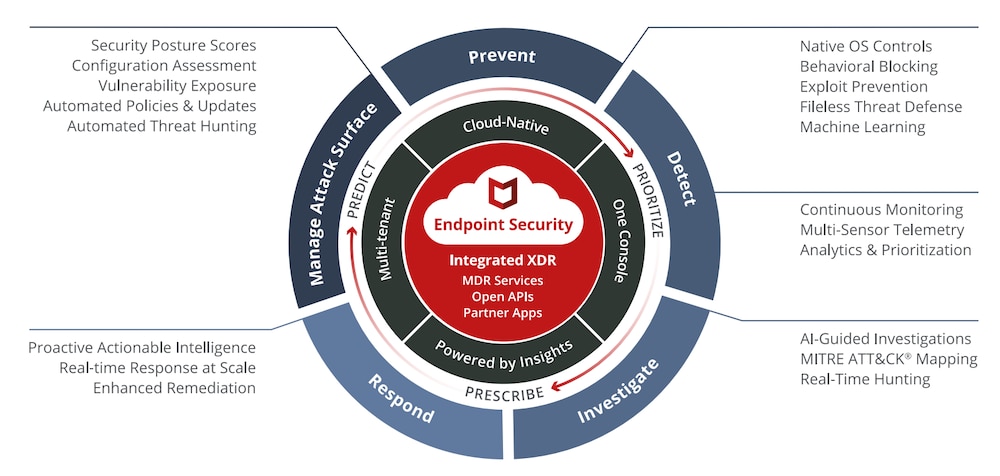
Fig: Intelligent and Proactive Endpoint Security
The Power of Big Data
McAfee’s advanced AI capabilities also pay other security dividends in terms of prevention. Suppose that someone creates a new piece of ransomware with the contents of the file obscured. We are able to then apply dynamic machine learning which examines the actual behavior of the process. Malicious malware behaves, well, maliciously and ransomware acts in very specific patterns. On our end, we’ll run all of those behaviors through a machine learning engine to figure out whether to remediate the activities of a questionable process.
What’s more, McAfee’s global intelligence capabilities tap into over 1 billion sensors around the world and deploys static machine learning to identify newer types of endpoint attacks. Instead of relying on a signature, we can examine a file’s attributes and calculate a score based on multiple vectors that helps determine whether the file in question exceeds a certain security threshold and whether to flag it as potentially malicious.
Let’s consider a case where a ransomware attack actually manages to infect an endpoint and the malware began to move laterally within the network.
This is the unique power of combined intelligence.
Typically, customers have had only two courses of action after a ransomware attack. If they were fortunate to have made backups, they can choose to reimage their machines. But that’s also a laborious process that takes time and can be quite expensive. Or they can surrender to the attacker’s demands and pay the ransom to unlock their information.
Here’s where McAfee’s host-based intrusion prevention technology helps to stop ransomware’s lateral movement, so it doesn’t spread and infect the rest of your endpoints. EDR will detect and prioritize alerts of anomalous behavior for further investigation so SOCs can respond to these threats – such as isolating or quarantining particular end points.
But McAfee’s endpoint solution includes a unique feature that allows customers to actually roll back the effects of a ransomware attack with enhanced remediation technology that can even restore encrypted data. This is a brilliant technical innovation that further sets our solution apart from the rest of the industry. Organizations can save on average $500 per node in labor and productivity costs by eliminating the need to reimage machines with Rollback Remediation. Watch the video below to see Rollback Remediation in action.
Human-Machine Teaming
After collecting telemetry from a vast data lake, our threat researchers apply AI to extract insights that translate into actionable intelligence for our customers. This process of “human machine teaming” is a powerful combination that generates proactive intelligence, so organizations remain ahead of the gathering threats on the horizon. SOC teams can view real-time updates as they drill down to learn about new threats in their environments based on geography and industry.
Dynamic application containment (DAC) is another technology that McAfee has developed to further protect endpoints. DAC both reduces ability of greyware to make malicious changes to the system while minimizing end-user impact as it does not use or require heavy sandbox or app virtualization. This works either online or offline and protects endpoints without compromising business continuity.
Our endpoint security platform alerts defenders about any devices in their network that may lack sufficient protection. They can then go ahead and isolate any devices at risk of getting breached or take any remediation actions to protect the organization. When all is said and done, the system is fully protected.
All too often, security defenders find themselves in a mad scramble trying to separate out false positives from an overwhelming number of alerts flooding their screens. All the while, the bad guys are plying their trade. But McAfee takes the guesswork out of that process so they can get a complete and realistic look at the attack landscape.
For more information, visit McAfee Endpoint Security.
For organizations increasingly in the crosshairs of ransomware attacks, these tools will make all the difference. It’s the future of intelligent endpoint security.
This post was first first published on Enterprise – McAfee Blogs’s website by Naveen Palavalli. You can view it by clicking here



