Source Code Leak – What We Learned and How You Can Protect Your IP
The latest leak appears to stem primarily from a misconfiguration of SonarQube, an open-source tool for static code analysis, which allows developers to audit their code for bugs and vulnerabilities prior to deployment.
This week we learned about a leak of source code from 50 prominent companies, posted by a Swiss IT consultant. These come after another recent leak of source code from Nintendo, prompting us to comment on the issue of IP protection and secure development pipelines.
A search for SonarQube on the popular IoT search engine Shodan allows anyone to discover ports used by common software such as this. With this information so easily available, ports unintentionally left open can introduce a wide swath of intrusion attempts.
Our own assessment found that SonarQube communicates on port 9000, which was likely misconfigured to be open to the internet for the breached companies, allowing researchers to gain access and discover the data now exposed in the leak.
How You Can Protect Your IP
Mistakes like misconfiguration and accidental credential exposure will happen in the development process, which is where InfoSec teams need to step in. Auditing infrastructure code both prior to deployment and continuously in production is essential for companies practicing DevOps and CI/CD.
Several of the source code repositories also contained hard-coded credentials, which open the door to accessing other resources and expansion of the breach. It is a best practice to never commit code with hard-coded/plaintext credentials to your repositories.
Audit Cloud Accounts for Misconfiguration
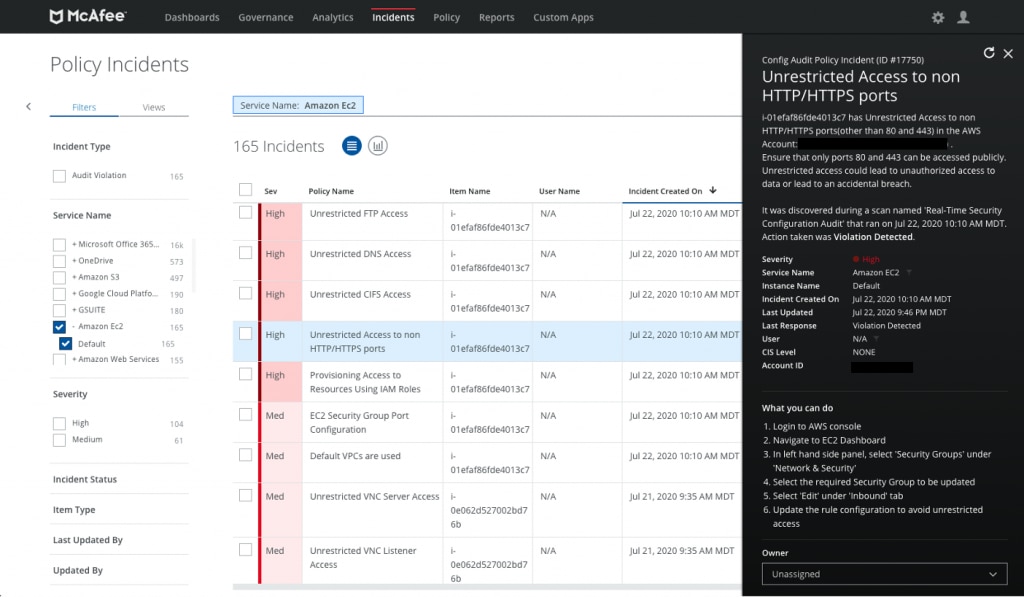
With MVISION Cloud InfoSec teams can monitor their company’s public cloud accounts, like AWS, Azure, or GCP, for configuration mistakes that may expose sensitive data. In the example below, MVISION Cloud discovered that a resource in AWS EC2 was configured with Unrestricted Access to ports other than 80/443, opening up potential breach scenarios like we saw with the source code leak.
Our solution to this problem is MVISION Cloud, the multi-cloud security platform for enterprises to protect their data, prevent threats, and maintain secure deployments for their cloud-native apps.
Scan Application Code for Vulnerabilities
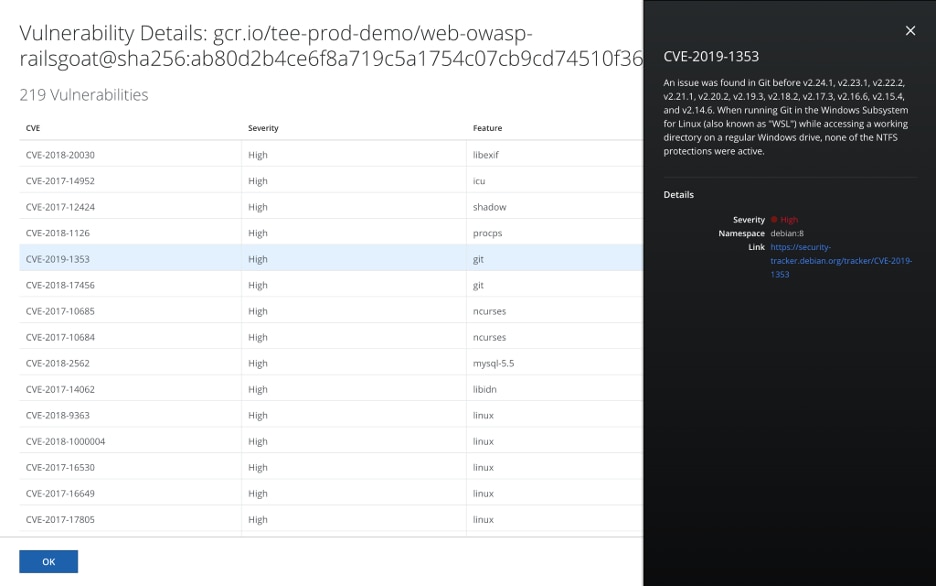
Companies with active container deployments should take this one step further, auditing not only for misconfigurations but also CVEs in their container images. In the example below, MVISION Cloud discovered that one container image contained 219 code vulnerabilities, many of which could be exploited in an attack.
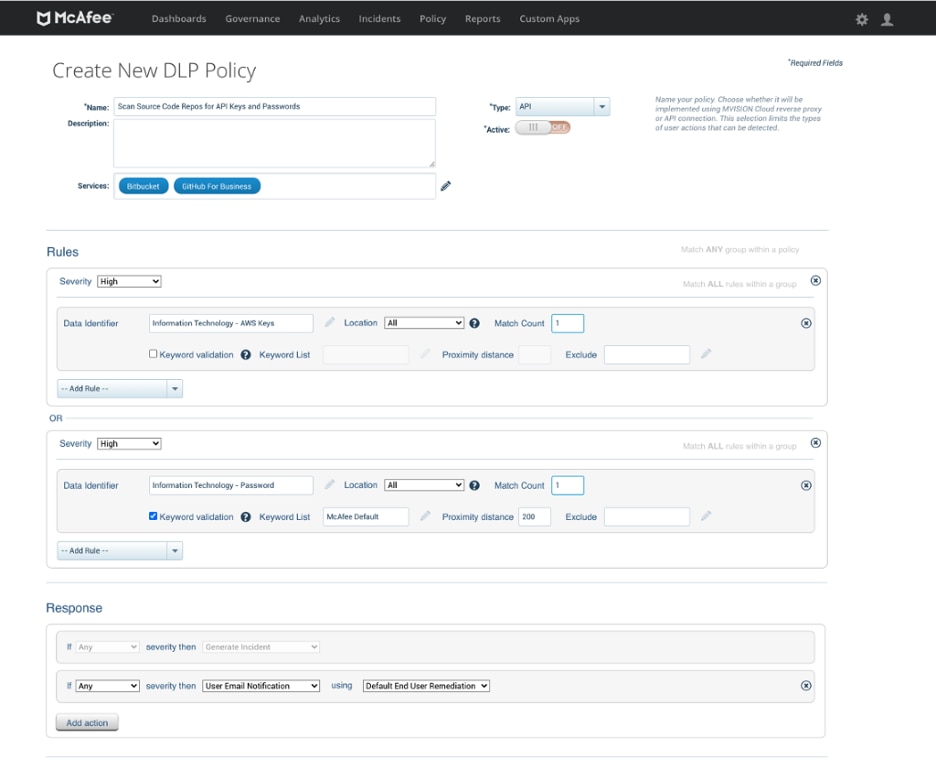
Scan Repositories for Hard-Coded Credentials and Secret Keys
To mitigate the risk of credential or secret key exposure, within MVISION Cloud you can easily scan your repositories for specific data types and take multiple levels of action. Below we’ve set up a policy to scan Bitbucket and Github with our Data Loss Prevention (DLP) data identifiers for AWS Keys and Passwords. With Passwords, we are using keyword validation, meaning we will only trigger an incident if a keyword like pwd, p, or password is nearby. We’ve chosen the least disruptive action here – notifying the end user to remediate themselves, however the option to delete the data is also available.
The speed of DevOps is allowing companies to innovate quickly, but without security audits built into the pipeline, misconfigurations and vulnerable code can go unnoticed and expose data in a breach. We strongly encourage the movement from DevOps to DevSecOps, building this audit process into the standard practice of application development.
For more on how MVISION Cloud can enable you to implement a DevSecOps practice, get in touch with us today.
This post was first first published on Enterprise – McAfee Blogs’s website by Sekhar Sarukkai. You can view it by clicking here


