Privilege Escalation on Meetup.com Enabled Redirection of Payments
As a result of our investigations, which are further detailed in this technical report, we found several “more-common” API security issues like Lack of Resources & Rate Limiting and Excessive Data Exposure, as well as serious cross-site scripting (XSS) and cross-site request forgery (CSRF) vulnerabilities on Meetup.com that could put users at risk. For those unfamiliar with XSS or CSRF vulnerabilities or want to refresh their memory, you can find more information here and here, respectively.
The Checkmarx Security Research Team recently audited the security of several high-profile websites, including Meetup.com. For those who are not familiar with Meetup.com, it allows users to create an event where people with similar interests gather. Events can be in person, and in light of the ongoing pandemic, many of them have moved to virtual settings. Some Meetup events are free, while others cost visitors various amounts of money to register and participate.
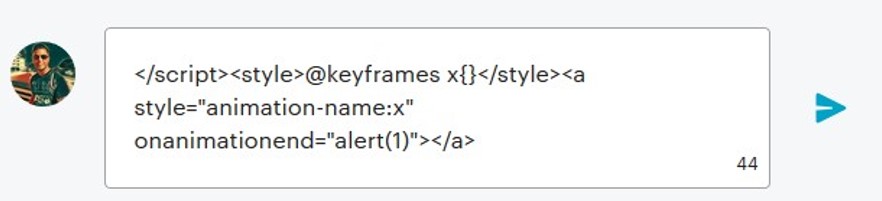
With our research of Meetup.com, we demonstrated how we could execute an XSS attack, since their website was discovered to be vulnerable. The discussion capabilities are being enabled by default in all Meetups, so a user could post a script (such as the one shown below) into the discussion area of a certain Meetup. This script can be completely hidden from the viewer.
Once this vulnerability was discovered, we continued digging further, finding that the Meetup website was also vulnerable to CSRF attacks. The next step for a hacker after finding a combination of XSS and CSRF is to try chaining them together, aiming for a much more severe exploit. We thought that escalating our own privilege from a regular user to co-organizer would be of more interest. By chaining the XSS and CSRF vulnerabilities together as demonstrated in this proof of concept (PoC) video, we were able to escalate ourselves from a regular Meetup user, to a co-organizer of a Meetup event, without any authorization or permission.
The short script above reflected from the server to the web browser, and ran a JavaScript popup on the user’s computer as soon as they visited the Meetup page. In this case, a user would see a popup on their computer with the number “1” in it. Attackers have many ways of exploiting this vulnerability, since it allows them to execute any JavaScript (assuming it is enabled) within any user’s browser that is visiting this certain Meetup page.
To demonstrate an attack scenario where managing money is abused, as can be seen in the PoC video, the team decided to try and “steal” some money. Using the same technique of chaining two vulnerabilities together, as often done by attackers, we next developed a script to change the Meetup’s email address that’s tied to the organizer’s PayPal account. Meaning that once the email address stored in Meetup -> Manage Money was changed to an attacker’s email, all future charges for attending an event associated with this Meetup would be directed to our “malicious” email address without the organizer noticing, since they receive no indication that the email address was changed. Adding to the concern, we could also take advantage of these same vulnerabilities, which could allow us to change every email address of every Meetup to whatever we wanted.
As a result of the malicious script injected and hidden in the groups’ discussion area, once the script was executed by the organizer (by just visiting the Meetup page), it unknowingly took advantage of the CSRF vulnerability and changed our role to “co-organizer,” and by that, granted us access to the group functions (e.g., contact all members, edit group settings, manage money, create events, etc.).
Meetup’s Response
“Meetup takes reports about its data security very seriously, and appreciates Checkmarx’s work in bringing these issues to our attention for investigation and follow up. There is no evidence of any exploitation of these now-resolved vulnerabilities; there was no impact on Meetup’s users’ accounts or privacy.”
- Take over any Meetup group by role escalation
- Access all group functions and assets (members’ details, edit group settings, fake event creation, etc.)
- Redirect all payments to any PayPal account
After discovering and validating the vulnerabilities, we notified Meetup of our findings and worked with them throughout the remediation process until they informed us everything was appropriately patched.
This post was first first published on Blog – Checkmarx’s website by Erez Yalon. You can view it by clicking here