Humans and Machines – Phishing Mitigation Automation SOARing to New Heights
Cofense and Palo Alto Networks Cortex XSOAR integrate to counter phishing threats that evade secure email gateways (SEGs). Human-verified phishing indicators and automation squelch attackers. Cofense Intelligence, Cofense Triage and Cortex XSOAR combine to support SOCs in the fight against phish.
By Mike Saurbaugh
Cofense Intelligence: What is Human-Verified Phishing Intelligence and Why Should I Care?
Conditioning employees to detect and report suspicious email is a strategy security leaders have adopted to protect the business and empower employees to become a defensive asset. As phishing emails evade secure email gateways (SEG), employees are the last line of defense and can be the difference between detection and response or an incident that leads to a breach. Cofense Triage ingests employee-reported suspicious email, allowing security teams to quickly assess and respond to threats. Cofense Intelligence is human-verified phishing intelligence powering security teams to respond to credible phishing threats.
A major impact-rating URL that was vetted by a seasoned security professional tells the customer that this URL is indeed malicious and should not be accessed. Knowing this information allows the security team to implement a block rule in the firewall to prevent employees from accessing a harmful link. Likewise, a suspicious domain may be an alert event. The point is that security professionals can more quickly implement rules with automation given the rigor that human vetting requires.
Cofense Intelligence is phishing-specific threat intelligence. Human-verified means that the Cofense intelligence and labs teams have vetted the indicators prior to consumption by customers. This ensures high-fidelity upon ingestion. Domains, URLs, IPs and hashes all have a corresponding impact rating that follows STIX. Major, moderate, minor and none ratings are applied to phishing indicators. This means that each indicator provided carries an impact rating so security teams can make educated decisions on what action to take.
Cofense Intelligence provides context for analysts. Not just what’s bad, but what’s bad and why.
Machine-Readable and Human-Readable Phishing Intelligence
The end result is a cadence of polling machine-readable indicators to be leveraged in security solutions with the context to understand the phishing threat and its potential impact to the business.
Integrations drive Cofense Intelligence via JSON, STIX or CEF, allowing SOARs, threat intelligence platforms (TIPs) and SIEMs to ingest updates on polling intervals because Cofense releases updates as soon as they’ve been vetted.
The following provides key fields to use in threat lookup validation, security solution integrations and threat hunting.
Actionable Machine-Readable Intelligence
Figure 1: Machine-readable JSON output
{
“success” : true,
“data” : {
“id” : 39377,
“relatedSearchTags” : [ ],
“feeds” : [ {
“id” : 23,
“permissions” : {
“WRITE” : false,
“READ” : true,
“OWNER” : false
},
“displayName” : “Cofense”
} ],
“blockSet” : [ {
“malwareFamily” : {
“familyName” : “NetWire Remote Access Trojan”,
“description” : “The Netwire RAT is used to take control of a user’s system, it has many capabilities including the ability to use a victimu0027s computer as a proxy and keylogging functionality that extends to peripheral devices such as USB card readers.”
},
“impact” : “Major”,
“blockType” : “URL”,
“role” : “C2”,
“roleDescription” : “Command and control location used by malware”,
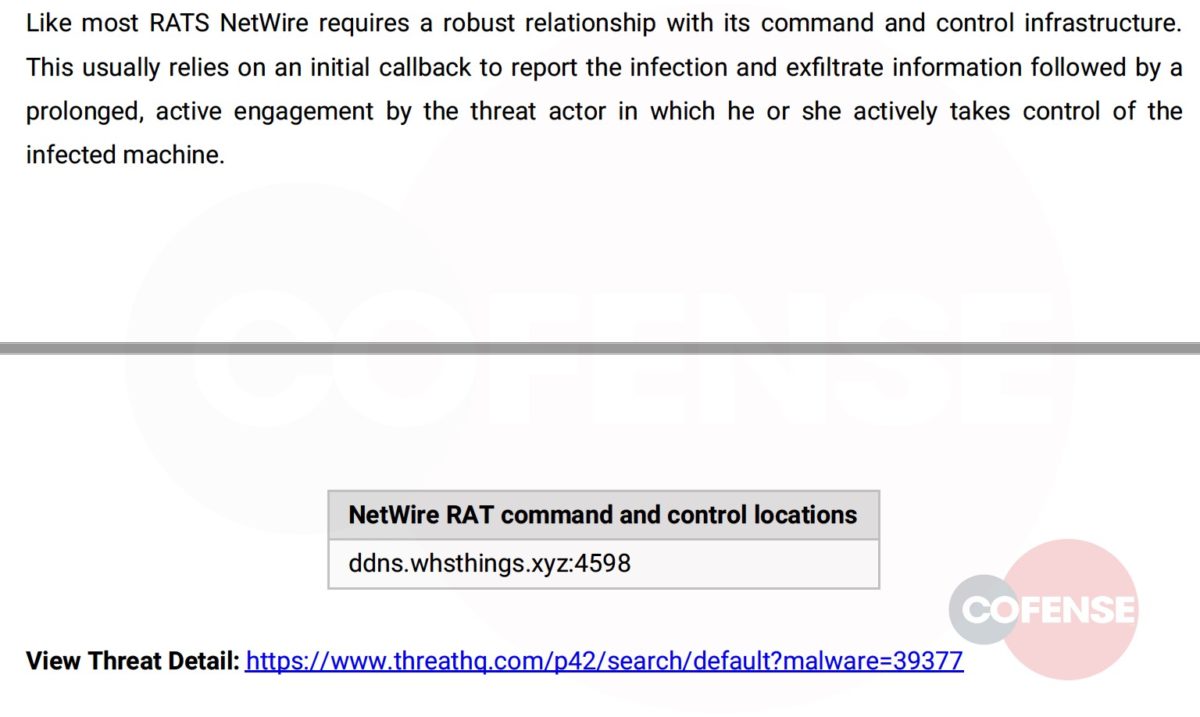
“data” : “hxxp://ddns[.]whsthings[.]xyz:4598”,
“data_1” : {
“url” : “hxxp://ddns[.]whsthings[.]xyz:4598”,
“domain” : “whsthings[.]xyz”,
“path” : “”,
“protocol” : “http”,
“host” : “ddns[.]whsthings[.]xyz”
}
}, {
“deliveryMechanism” : {
“mechanismName” : “CVE-2017-11882”,
“description” : “Microsoft Office exploit taking advantage of flaw in Microsoft Equation Editor
allowing for arbitrary code execution”
},
“impact” : “Major”,
“blockType” : “URL”,
“role” : “InfURL”,
“roleDescription” : “URL provided in email as means for infection”,
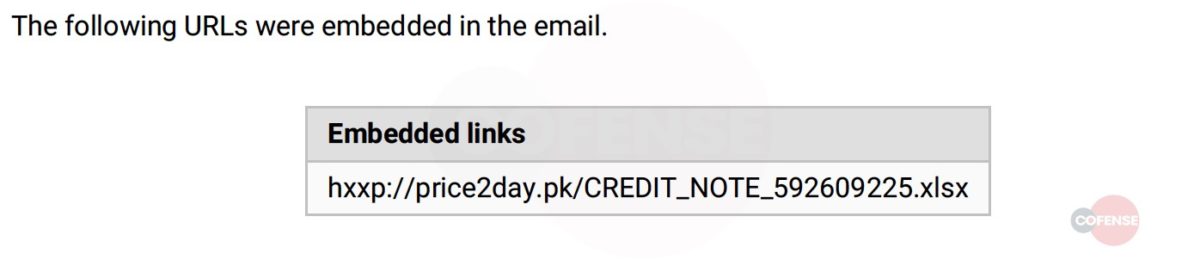
“data” : “hxxp://price2day[.]pk/CREDIT_NOTE_592609225.xlsx”,
“data_1” : {
“url” : “hxxp://price2day[.]pk/CREDIT_NOTE_592609225.xlsx”,
“domain” : “price2day.pk”,
“path” : “/CREDIT_NOTE_592609225.xlsx”,
“protocol” : “http”,
“host” : “price2day[.]pk”
}
}, {
“malwareFamily” : {
“familyName” : “NetWire Remote Access Trojan”,
“description” : “The Netwire RAT is used to take control of a user’s system, it has many capabilities including the ability to use a victimu0027s computer as a proxy and keylogging functionality that extends to peripheral devices such as USB card readers.”
},
“impact” : “Major”,
“blockType” : “Domain Name”,
“role” : “C2”,
“roleDescription” : “Command and control location used by malware”,
“data” : “ddns[.]whsthings[.]xyz”,
“data_1” : “ddns[.]whsthings[.]xyz”
Figure 2: Executive Summary from Cofense Intelligence Active Threat Report
Contextual Human-Readable Intelligence
When understanding the phishing threat and its severity are critical, Cofense’s portal and reports provide insight.
Figure 4: Description of Command and Control Malware with a Link to WebUI
Figure 3: One of Many URLs Involved in the Threat Report
Cortex XSOAR takes a new approach with native threat intelligence management, unifying aggregation, scoring, and sharing of threat intelligence with playbook-driven automation. With Cortex XSOAR, analysts eliminate manual tasks with automated playbooks to aggregate, parse, deduplicate, and manage millions of daily indicators across dozens of supported sources. From here, analysts take charge of their threat intelligence with playbook-based indicator lifecycle management and transparent scoring that can be extended and customized with ease.
Cortex XSOAR Threat Intel Management Supercharges SOCs
Reputable sources of intelligence enable automated action to shut down threats across more than 450 third-party products with purpose-built playbooks based on proven SOAR capabilities.
With analysts potentially spread across the globe, Cortex XSOAR boosts collaboration to reveal critical threats by layering third-party threat intelligence with internal incidents to prioritize alerts for smarter response decisions.
Leveraging Cofense Intelligence in Cortex XSOAR
Additionally, analysts can save time by executing intel-based playbooks to expedite threat hunting across disparate security tools. In this way, security teams can identify, gain context for, and prioritize alerts to advanced and relevant threats.
From the JSON output shown earlier, analysts in Cortex XSOAR can enable the Cofense feed, provided they have a valid Cofense Intelligence license.
Human-verified Cofense Intelligence complements Cortex XSOAR’s threat intelligence management module. Analysts can automatically block phishing threats by aggregating, deduplicating and syndicating protection from indicators sourced from Cofense Intelligence and other feeds.
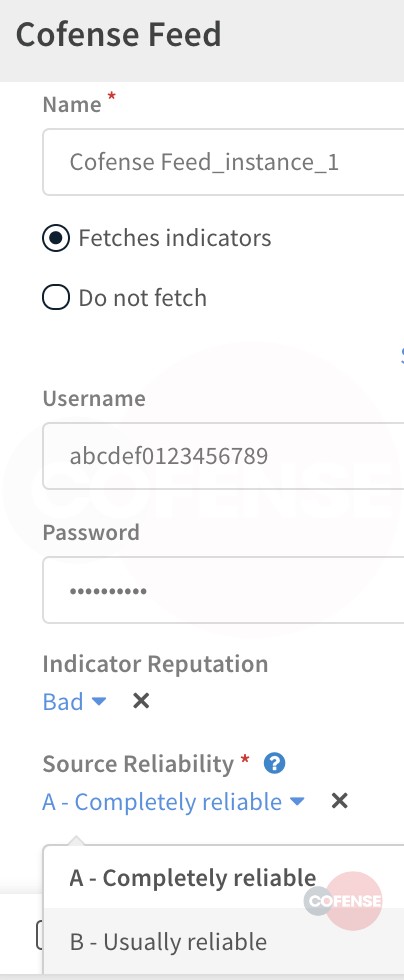
Within configuration settings, and because the intelligence feed is human-verified by Cofense, analysts can opt to set reliability to “completely reliable” and an indicator reputation as “bad.”
Figure 5: Cofense Feed Integration Application in Available in Cortex XSOAR
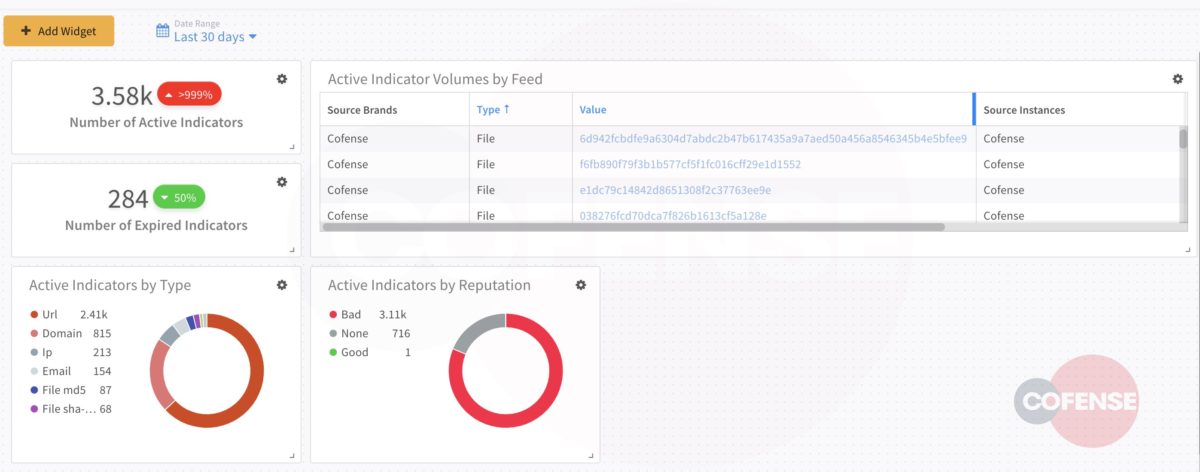
Cortex XSOAR’s dashboard is a quick and easy way to visualize Cofense Intelligence indicators.
Figure 6: Cofense Intelligence Feed Configuration Settings
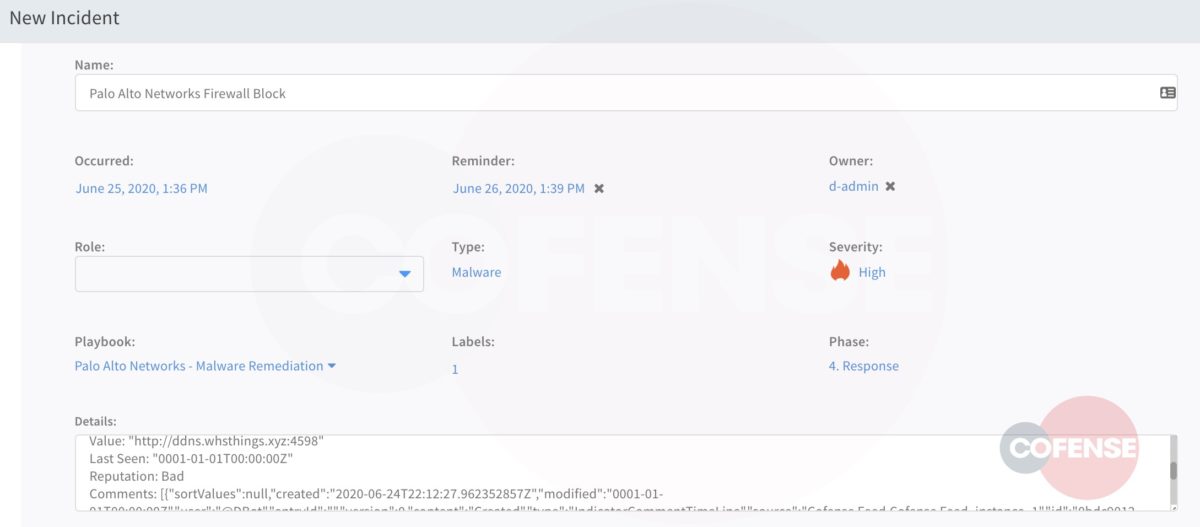
The URLs in this case can be assigned to an incident and attached to a playbook. In this way, as an example, one or more URLs within the Palo Alto Networks Next-Generation Firewall can be blocked.
Figure 7: Cortex XSOAR Threat Intelligence Management Dashboard – Cofense Intelligence Indicators
Cofense Triage: Automating Analysis of Employee-Reported Phish
Figure 8: URL Incident Remediation
Cofense pioneered phishing simulation to help organizations educate and condition employees to spot phish. Phishing simulation has been adopted by organizations worldwide and continues to be a staple of security programs.
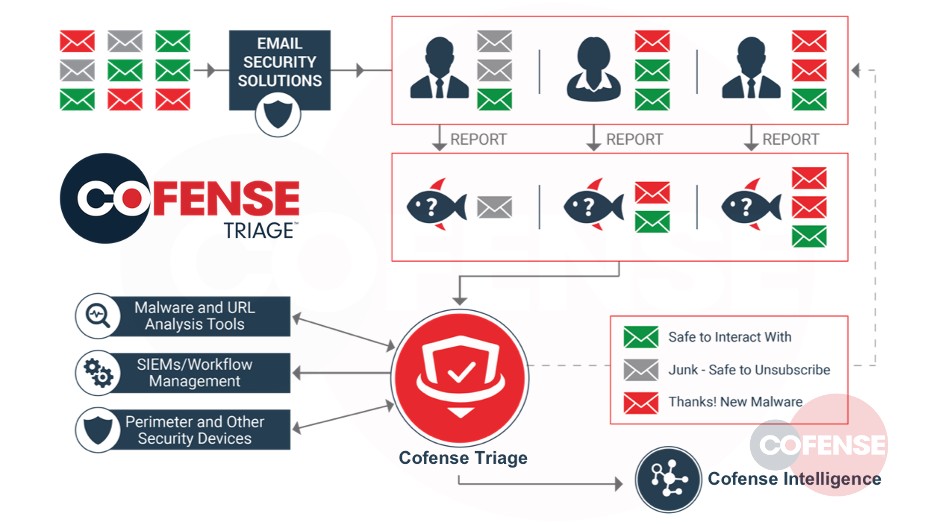
Security teams do their best to keep phish from making it to the employee’s mailbox. However, attackers are skilled at evading secure email gateways and other defenses. Cofense Triage ingests employee-reported phish to automatically uncover the latest attacks plaguing the enterprise.
Cofense Triage ingests and analyzes the reported emails, highlights real phish and removes benign messages mistakenly reported by employees. Cofense Triage benefits from Cofense Intelligence and several integrations, including Palo Alto Networks WildFire™.
Cofense Reporter empowers employees to report suspicious phish to the SOC so that they can analyze and respond to evasive perimeter phishing threats. A simple one-click feature in the email client is all that’s needed for employees to provide security teams with an additional source of intelligence.
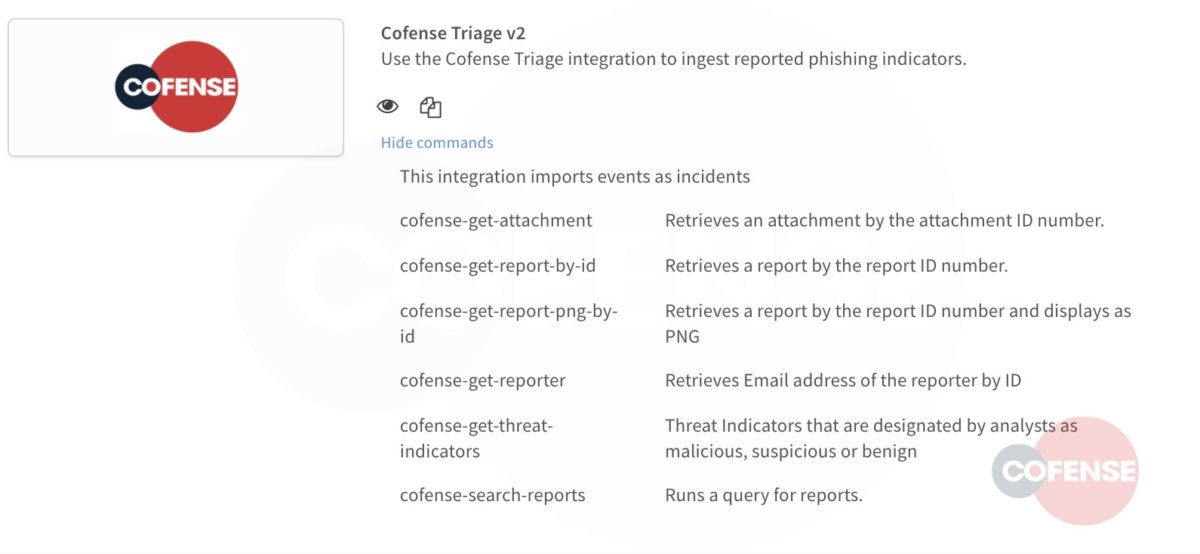
Cofense Triage – An Enabler for Cortex XSOAR Playbooks
Figure 9: Cofense Triage Infographic Workflow
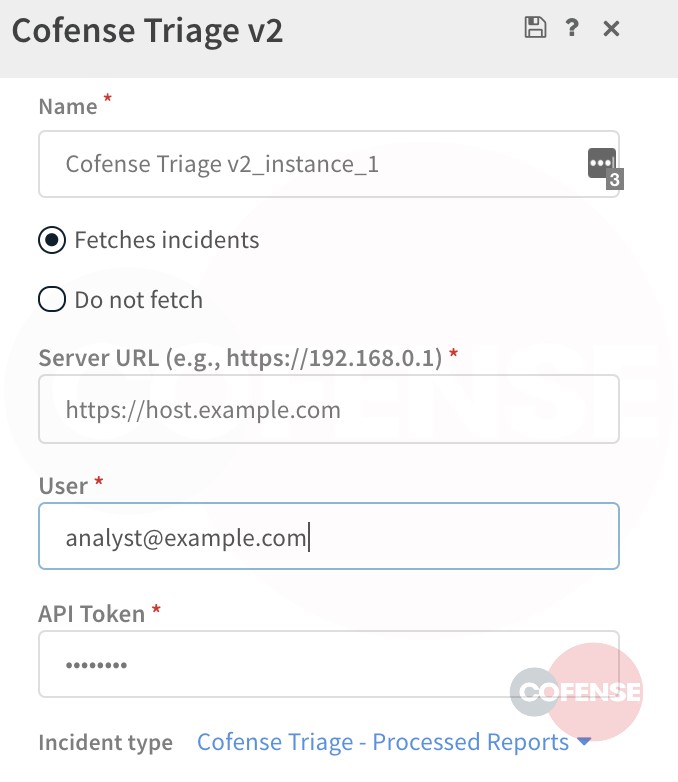
Analysts configure their app in Cortex XSOAR and ingest processed reports with designated threat indicators.
Cofense Triage APIs are accessible to Cortex XSOAR with an integration app to ingest processed phishing reports. This means that Cofense Triage and Cortex XSOAR customers can poll APIs from the application and assign to playbooks just as with Cofense Intelligence.
Figure 11: Cofense Triage Configuration – Assigning Incidents at Ingestion
Figure 10: Cofense Triage Application in Cortex XSOAR
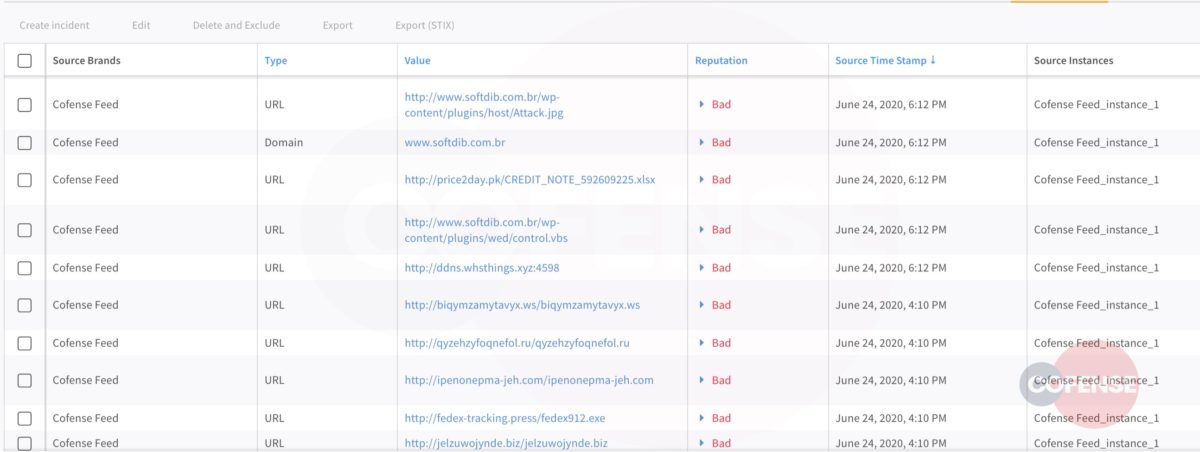
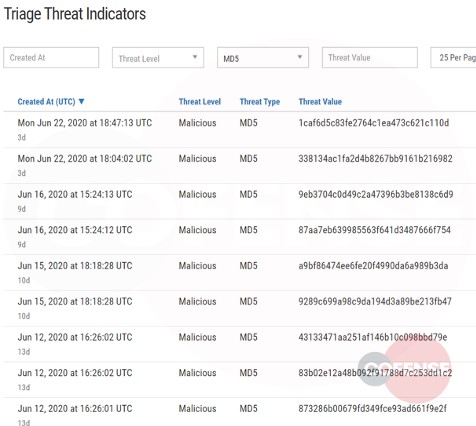
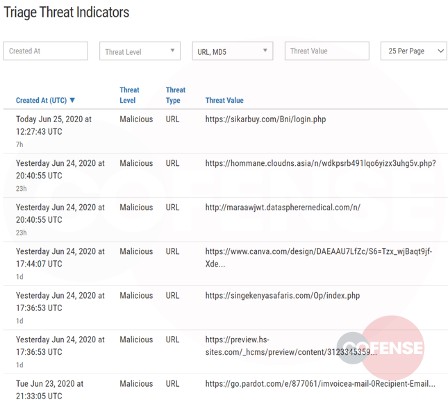
When employees report, security teams benefit. Take a look at malicious URLs and hashes as reported by conditioned employees who received phish and knew to report with Cofense Reporter.
Malicious Indicators Evading Secure Email Gateway
Cortex XSOAR Ingesting Threat Indicators from Cofense Triage
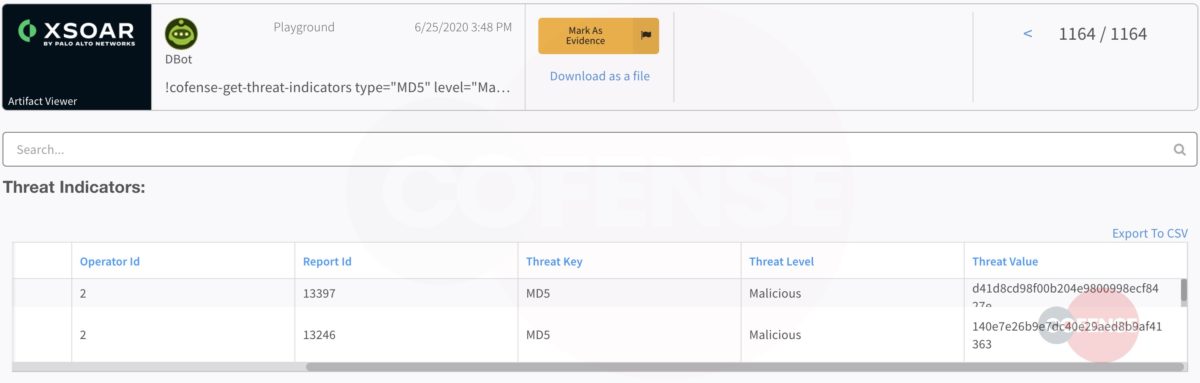
Figure 12: Malicious Indicators in Cofense Triage
Figure 13: Ingested Malicious Hashes from Cofense Triage
When a security analyst designates a file, URL or domain as malicious, they have vetted the threat as would Cofense’s Intelligence team. Knowing this, security professionals can ingest the indicators and allow them to run through a playbook for next step actions.
Multiple Sources of Intelligence in One View
Figure 14: Playbook Execution of Malicious File Attachment Reported by Employee
Figure 15: Dashboard View of Cofense Triage Feed
Cortex XSOAR allows analysts to manipulate widgets to view all sources of intelligence or get more granular and investigate one source.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
Secure email gateways and other security solutions are not impermeable. If your SOC is feeling the pain and is in need of some relief, Cofense and Cortex XSOAR bring that relief in seconds rather than days. When employee-reported and human-vetted sources of intelligence align, security teams can be more confident in their remedial actions. Whether it is endpoint or network-based remediation, or conducting a threat lookup to help make additional decisions, Cofense solutions complement the capabilities Cortex XSOAR offers to help customers centralize the security operation.
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here