Introducing MITRE ATT&CK in MVISION Cloud: Defend with Precision
Most enterprises use over 1,500 cloud services, generating millions of events, from login, to file share, to download and an infinite number of actions meant for productivity yet exploited by adversaries. Until now, hunting for adversary activity within that haystack has been an arduous effort, with so much noise that many data breaches have gone unnoticed until it is too late.
The latest innovation in MVISION Cloud, the multi-cloud security platform for enterprise, introduces MITRE ATT&CK into the workflow for SOC analysts to investigate cloud threats and security managers to defend against future attacks with precision.
First, the haystack of events is processed continuously against a baseline of known good behavior by User and Entity Behavior Analytics (UEBA) to identify the anomalies and actual threats in your environment, assessing behavior across multiple services and accounts.
MVISION Cloud takes a multi-layered approach to cloud threat investigation that can speed your time to detect adversary activity in your cloud services, identify gaps, and implement targeted changes to your policy and configuration.
Events processed by UEBA determined to be a compromised account
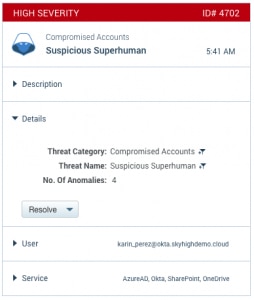
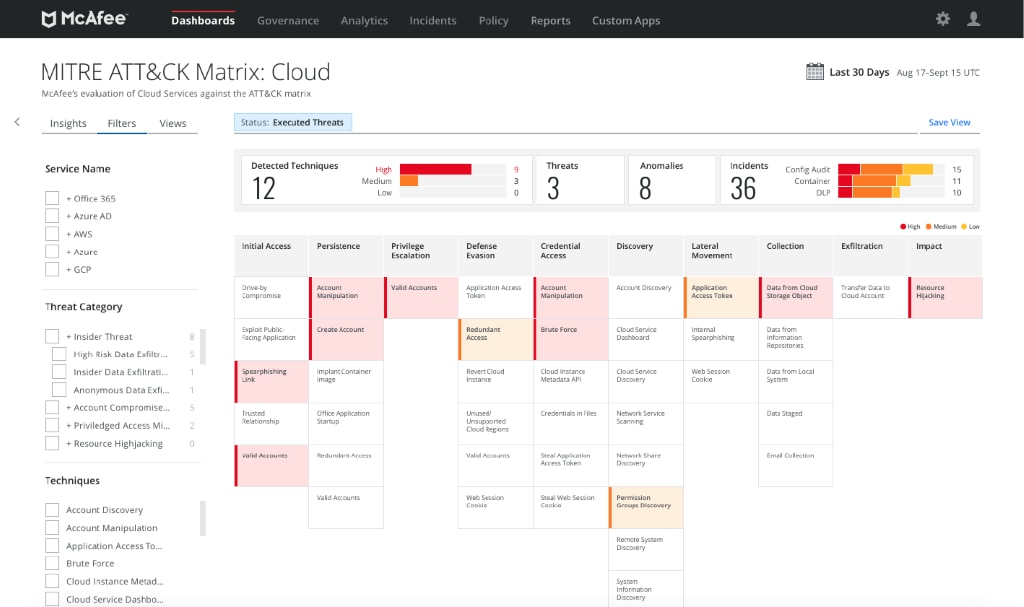
This takes your investigation process down to a manageable quantity of incidents. With this release, those incidents are now in the same language as the rest of the SOC – MITRE ATT&CK. Each cloud security incident is mapped to ATT&CK tactics and techniques, showing you adversary activity currently being executed in your environment.
You have three views within MVISION Cloud:
Multi-cloud MITRE ATT&CK view of adversary activity in MVISION Cloud
- SecOps Teams Advance from Reactive to Proactive: McAfee MVISION Cloud allows analysts to visualize not only executed threats in the ATT&CK framework, but also potential attacks they can stop across multiple Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS) and Infrastructure-as-a-Service (IaaS) environments
- SecOps Teams Break Silos: SecOps teams can now bring pre-filtered cloud security incidents into their Security Information Event Management (SIEM)/Security Orchestration, Automation and Response (SOAR) platforms via API, mapped to the same ATT&CK framework they use for endpoint and network threat investigation
- Security Managers Defend with Precision: McAfee MVISION Cloud now takes Cloud Security Posture Management (CSPM) to a new level, providing security managers with cloud service configuration recommendations for SaaS, PaaS and IaaS environments, which address specific ATT&CK adversary techniques
With McAfee, threat investigation isn’t just for one environment – it is for all of your environments, from cloud to endpoint and your analytics platforms. With McAfee MVISION Cloud, MVISION EDR, and MVISION Insights, your enterprise has an extended detection and response (XDR) platform for the heterogenous attacks you face today.
- Retrospective: viewing all adversary techniques that have already occurred in your environment
- Proactive: viewing attacks in progress, that you can take action to stop
- Full kill-chain: viewing a combination of incidents, anomalies, threats, and vulnerabilities into a holistic string of infractions.
Multiple teams in your organization benefit from this addition to MVISION Cloud:
This post was first first published on Enterprise – McAfee Blogs’s website by Thyaga Vasudevan. You can view it by clicking here



