Sizing Up: How Mandiant Evaluates Ransomware Defense
Organizations across various regions, industries, and sectors have identified ransomware as a significant risk and wonder if they are positioned to successfully detect and prevent a ransomware attack. At FireEye Mandiant, we use a methodology that determines our client’s susceptibility to ransomware and evaluates their ability to detect and respond to a ransomware attack.
What is Ransomware?
Ransomware attacks are a commonly used by attackers for financial gain. The attack is meant to disrupt business operations by taking critical data and/or systems offline. If the organization wishes to resume business operations, they need to have backup data available and the ability to restore that data in a timely manner, pay the threat actor for decryption tools, or accept the loss of systems and data and rebuild their environment. Organizations often struggle with quickly restoring systems and data given the large scope of systems that were impacted. However, organizations that have been able to successfully restore their data were able to reduce the ransomware’s impact to business operations. Ransomware operators are aware that if an organization can promptly restore its data, the likelihood of ransom payment is low. Therefore, some ransomware operators will steal an organization’s sensitive data prior to encryption and publish it on a website. These reasons are why organizations are so concerned about ransomware and have sought our assistance to help with this problem.
What is a Ransomware Defense Assessment?
The FireEye Mandiant Ransomware Defense Assessment evaluates an organization’s ability to detect, contain and remediate ransomware within their environment. This is performed via multiple techniques, which involve reviewing documentation, conducting interactive ransomware focused workshops, and performing ransomware simulation activities. The ransomware simulation activities use the same techniques as seen on the front lines of Mandiant’s incident response engagements and from Mandiant Threat Intelligence by ransomware-focused threat actors. This assessment is constantly updated to reflect the most recent and relevant ransomware operators and families, in order to deliver maximum value to our clients.
This will assess the impact a ransomware attack could have on your internal network, discover what data could be jeopardized or lost, and test the ability of your security controls to detect, contain and respond to a ransomware attack. The benefits of this assessment are:
- Identifying specific assets that ransomware operators and encryptors can reach
- Realizing security weaknesses that can be exploited by ransomware operators and encryptors
- Determining opportunities for reducing an organization’s attack surface
- Recognizing operational deficiencies in the management of ransomware-related tasks
Ransomware Defense Assessment
Mandiant evaluates the impact that a ransomware attack can have on our clients through five competencies:
- Governance
- Security Architecture
- Response
- Communications
- Recovery
Mandiant reviews client documentation and facilitates workshops to discuss how they prepare for and respond to ransomware attacks. Additionally, Mandiant performs ransomware and ransomware operator simulation activities for the relevant focus area. The goal is to identify opportunities to bolster cyber defenses prior to a ransomware attack that has the potential to disrupt business operations and impact brand and reputation.
Governance
Governance oversees the people, process and technology facilitated by risk management, and promotes informed decisions based on intelligence and awareness of security threats, including ransomware that threatens normal business operations. This governance function provides the strategy and direction for the organization.
Mandiant reviews client’s policies and processes designed to reduce the likelihood and impact of a successful ransomware incident. This includes those for identifying critical assets, vulnerability and patch management, configuration hardening and minimum-security baselines, as well as those related to security awareness training. Mandiant also looks for those organizational and command structures in place for clear and effective decision making during an incident.
Host Discovery and Vulnerability Exploitation
Mandiant performs ransomware operator and encryptor simulation activities to validate the client’s vulnerability and patch management policies. For example, Mandiant will discover live Windows hosts on the internal network running services that can be used by ransomware operators or encryptors for ransomware deployment or propagation, such as Server Message Block (SMB), Remote Desktop Protocol (RDP) and Windows Remote Management (WinRM). Mandiant will then scan for hosts that are vulnerable to Windows remote code execution (RCE) vulnerabilities used by ransomware and ransomware operators to propagate. An example of an RCE vulnerability is MS17-010 (“ETERNALBLUE”), as shown in Figure 1.
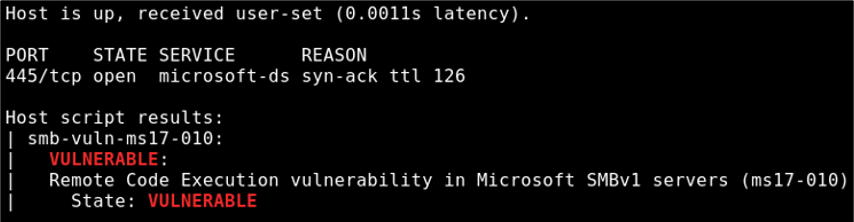
Figure 1: Scanning for ETERNALBLUE
Mandiant will perform exploitation of the vulnerable hosts to demonstrate impact and see how far a ransomware operator or encryptor could spread using those vulnerabilities, as shown in Figure 2, where the ETERNALBLUE exploit was used.
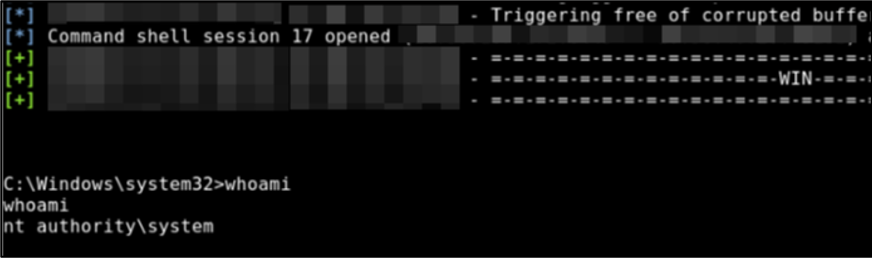
Figure 2: Exploiting ETERNALBLUE
Security Architecture
A ransomware defensible architecture consists of the systems, tools and processes to prevent and detect ransomware. This includes ensuring visibility across the environment to detect activity that may represent an ongoing compromise and having proper network segmentation to reduce ransomware spread.
Automated and manual methods are used to spread ransomware across a network. Endpoint and network vulnerabilities are abused to automate the spread of worm-like ransomware variants. Additionally, manual deployment methods are also used by ransomware operators that create and enable malicious Active Directory Group Policy Objects (GPOs).
Often, ransomware is also spread across the environment using local accounts. Mature account management is necessary to reduce the likelihood of ransomware targeting these accounts. Tools can be used to randomize passwords for local accounts. Additionally, jump servers and privileged access workstations should be used when a privileged account is required to perform administrative tasks. Organizations should monitor for workstation-to-workstation communications and the abnormal use of privileged accounts.
Mandiant will review these and other key architectural items and provide recommendations for how to make improvements directly related to mitigating risks associated with ransomware.
Mandiant performs the following ransomware and ransomware operator simulation activities for this focus area in order to validate the technologies, processes and procedures in place to detect, prevent and contain ransomware:
- Ransomware Encryption Simulation
- File Share Discovery and Enumeration
- Privilege Escalation and Lateral Movement
- Network Segmentation Testing
Ransomware Encryption Simulation
Mandiant will perform a ransomware encryption simulation using a custom internal toolkit, which simulates the encryption of a large number of ransomware variants, including notable variants such as Ryuk and WannaCry. The encryption simulation tool will encrypt plaintext files and rename the encrypted files to the appropriate extension, as shown in Figure 3. Additionally, the toolkit has the capability to drop ransomware notes used by real ransomware malware, change the desktop wallpaper, and delete volume shadow copies.
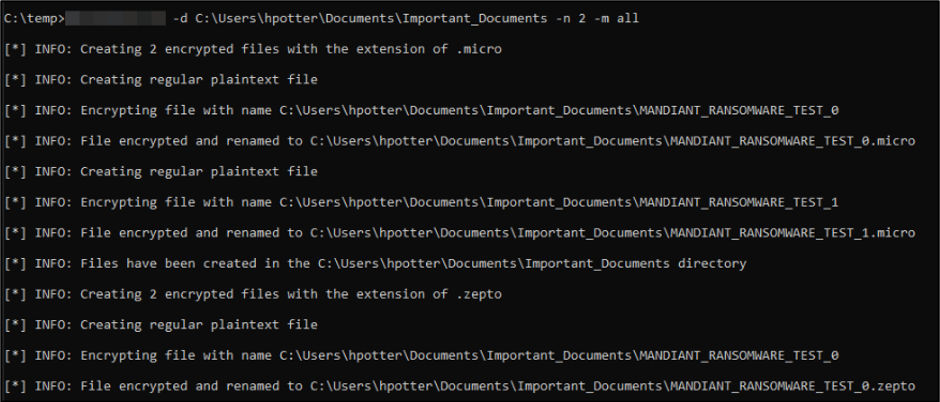
Figure 3: Performing ransomware encryption simulation
An example of the plaintext and encrypted file is shown in Figure 4 with a file that was simulated to have been encrypted by the Ryuk ransomware variant.
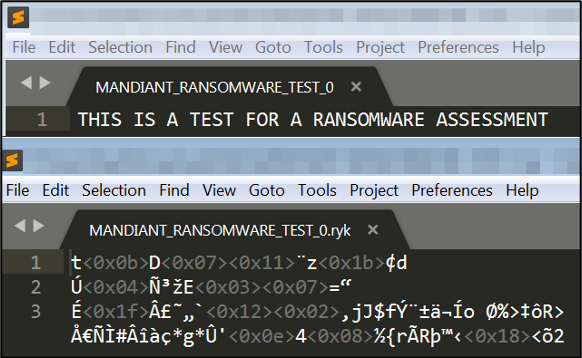
Figure 4: Showing plaintext and encrypted file
File Share Discovery and Enumeration
Mandiant performs file share discovery and enumeration from the context of an unprivileged domain user to see which file shares are writable that ransomware could affect. This is performed using open source and custom tools. An example of validating write access to a file share is shown in Figure 5.
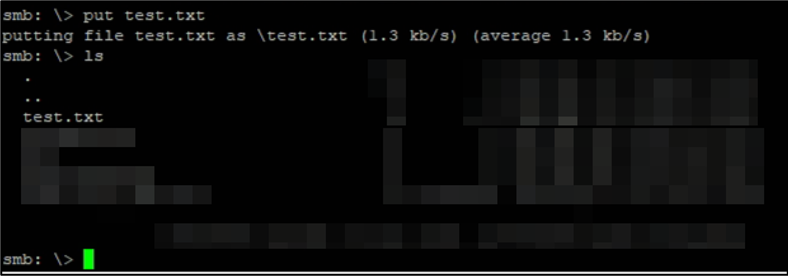
Figure 5: Validating write access to file share
Privilege Escalation and Lateral Movement
Mandiant also performs credential harvesting on compromised hosts using Mimikatz, as shown in Figure 6. Credential harvesting can be performed both by automated ransomware and ransomware-focused threat actors.
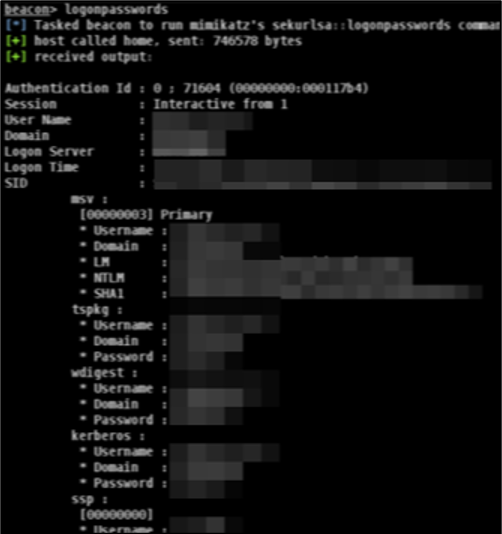
Figure 6: Dumping cleartext credentials with Mimikatz
Mandiant will perform credential spraying of harvested credentials using a Mandiant developed tool, CredNinja, in this example. This is performed across discovered hosts to see which hosts ransomware or ransomware-focused threat actors could spread to with those credentials, as shown in Figure 7.
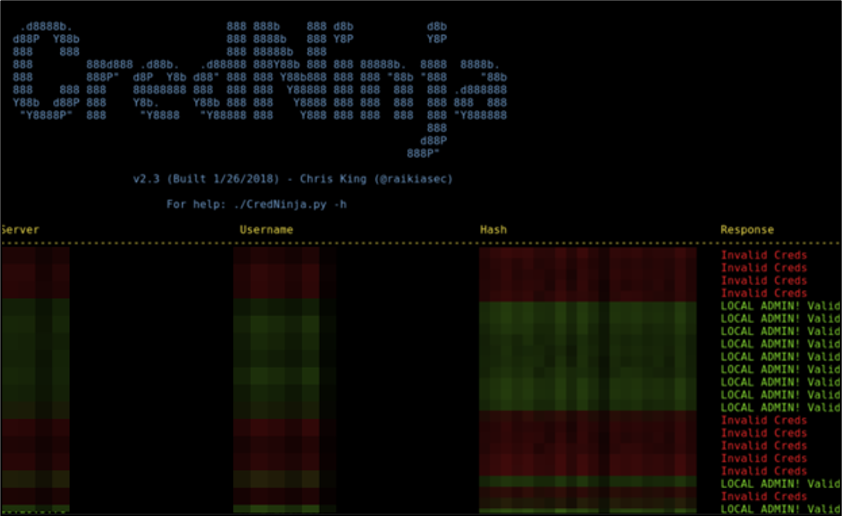
Figure 7: Credential spraying
Mandiant will also perform lateral movement using methods such as PsExec (Figure 8) that are used by ransomware and ransomware-focused threat actors and highlighted in our ransomware protection and containment strategies blog post.
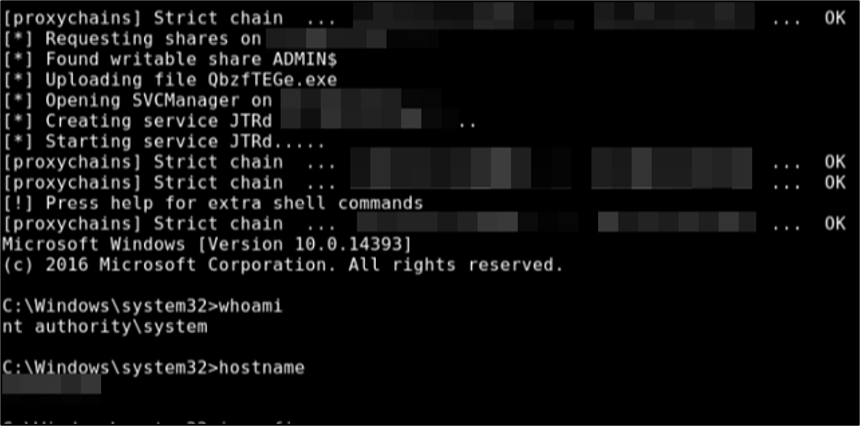
Figure 8: Lateral movement with PsExec
The process shown in Figure 9 is repeated by Mandiant to demonstrate the impact that ransomware could have on an environment and to see how far ransomware could spread.
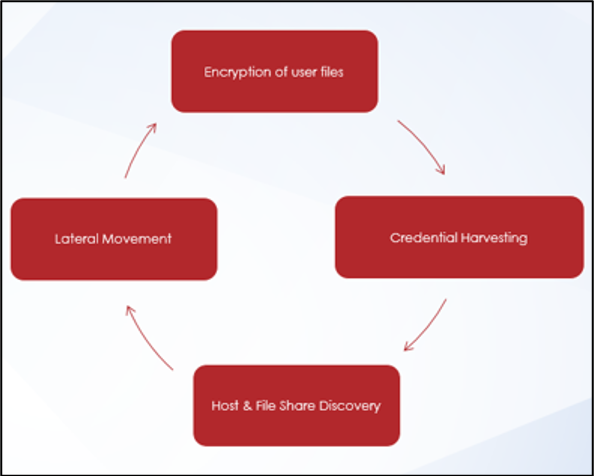
Figure 9: Process to demonstrate impact
Network Segmentation Testing
Mandiant also performs network segmentation testing using open source and custom tools to discover the Windows services that are available on sensitive networks. This is to understand the exposure that is present on networks that are sensitive and critical in nature. Mandiant will provide a summary of the services available in each of the sensitive networks, along with details on each host that has the affected service available.
Response
Incident Response is considered the last line of defense for organizations. If prevention capabilities fail, an organization must have the ability to detect malicious activity and respond accordingly.
Mandiant evaluates our client’s ability to respond to a ransomware attack, including processes to test and improve ransomware response. The organization should consider developing a ransomware specific playbook that incorporates the following:
- Processes to search across the network to identify ransomware specific indicators
- Actions necessary to promptly restrict network traffic between network segments to reduce ransomware spread
- Activities required to disable administrative shares to reduce ransomware spread
- A process to disable Windows Remote Management (WinRM) and PowerShell remoting on endpoints to reduce ransomware spread
- Procedures to promptly isolate a Domain Controller to facilitate later Active Directory database recovery
At times, ransomware response is not all technical. A successful ransomware compromise can be a business impacting event that requires leadership to make decisions that directly affect organizations survivability. Organizations should ask and ensure they have answers for the following questions:
- Is our executive team concerned about ransomware and the potential effects it can have on business operations?
- Did the threat actor steal materially sensitive data from our organization before deploying the encryptors?
- Does our cyber insurance carrier cover ransomware incidents?
- Who do we contact first, cyber insurance carrier, external legal counsel or digital forensics incident response specialists?
- Do we perform tabletop exercises that are specific to ransomware response?
Communications
An organized incident response process requires communication between responding groups to contain and recover from a ransomware attack. Groups can include technical and non-technical internal support personnel and groups outside of the organization that support the incident response process. Organizations that have a formal incident response Communications Plan tend to respond better to security incidents that impact business operations.
Mandiant reviews client’s communication processes and plans that should include methods to maintain communications during a ransomware attack. Communication plans should also document when it is pertinent for the organization to inform clients, employees, and the public media about a ransomware attack. Delivering a clear public message is important to protect brand and reputation. Additionally, internal incident response staff must be able to communicate in a secure manner and should formalize out-of-band communication processes to keep incident responders up to date on ransomware containment and remediation efforts.
Recovery
After the full scope of the incident is realized and containment efforts have successfully stopped the ransomware spread, it is time to restore systems and data, and get back to work. Getting back to normal business operations is usually top of mind. Executives and employees alike are wondering, “When will we be able to function normally and provide the services that our organization is known for?”
Backup strategies should be developed and continuously evaluated to ensure that the organization is able to promptly restore data that has been encrypted by ransomware. It is important to not only rely on online backups; offline storage should also be available to restore data. Threat actors are always looking for ways to improve ransomware and at times, will target online storage mechanisms. Offline storage data may be the only option to restore data; therefore, recovery point objectives and recovery time objectives should be understood when developing a backup strategy that supports bringing systems and data back online after a ransomware attack.
Mandiant discusses ransomware recovery strategies with clients. In order to recover from a ransomware incident, ransomware recovery strategies should be developed that incorporate procedures to restore access to systems and data. As an example, if Active Directory was targeted, processes to restore access to Active Directory environments should be developed and tested, such as using a previously isolated Domain Controller to restore the Active Directory database file.
In addition to developing procedures to recover systems, the organization should also consider the following:
- Do we pay the ransom to regain access to our data?
- If we do decide to pay, do we have access to cryptocurrency? Or the ability to obtain it?
- Do we have a relationship with another organization that can broker payment?
Decisions to pay a ransom in order to recover ransomware encrypted data should be considered prior to experiencing a ransomware attack. If the organization is open to paying a ransom to gain access to business-critical data, a ransom payment process should be incorporated into the ransomware recovery strategy.
Conclusion
Ransomware remains a concern as attackers continue to target organizations. Attacks and ransom demands are increasing; therefore, it is important to impede an attacker’s ability to perpetuate ransomware attacks. Our Mandiant Ransomware Defense Assessment can help organizations detect, respond to and reduce the impact of a ransomware attack.
Resources
For more information on ransomware, check out the below FireEye Virtual Summit sessions and webinars.
This post was first first published on
‘s website by Brett Hawkins. You can view it by clicking here

