Security Without Barriers, Part Two: Planning for Cyber Resilience
The network perimeter was a key component for defense-in-depth cyber security strategies, separating the internal “trusted” environment from the external “untrusted” world. For many organizations, recent world events have accelerated their adoption of cloud computing and increased their reliance on remote workers. This shift continues a trend where the traditional network perimeter has largely disappeared.
Information security strategies must enable authorized users to work productively from anywhere while still protecting critical assets. In the previous post from this series, we explored how security leaders can describe cyber resilience to stakeholders using a museum analogy rather than using a castle analogy to describe defense-in-depth.
Museums welcome visitors while still protecting assets from theft or damage. Their security focus shifts from preventing access to preventing exploitation of access. These same concepts can apply when building cyber resilience into an organization.
Getting Started With Cyber Resilience
Many organizations have used cyber resilience to protect their technology environments. A successful strategy should address a few main goals:
- Prevent: Identify threats early to stop attacks before they cause damage
- Mitigate: Minimize damage by disrupting and recovering from attacks that get through
- Sustain: Maximize efficiency and effectiveness of security processes and controls
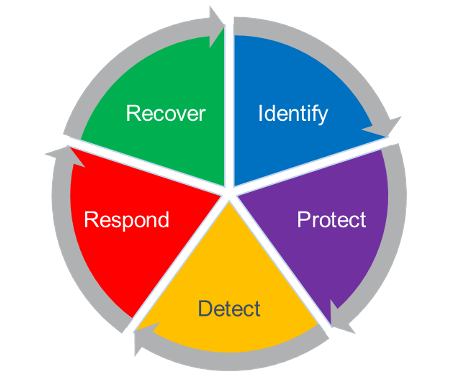 While these goals are relatively straightforward, building a detailed plan to achieve them can be daunting. Frameworks such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework can be used to map out and communicate an approach to stakeholders. The NIST framework offers a holistic model that has been widely adopted around the world.
While these goals are relatively straightforward, building a detailed plan to achieve them can be daunting. Frameworks such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework can be used to map out and communicate an approach to stakeholders. The NIST framework offers a holistic model that has been widely adopted around the world.
Another benefit to the NIST framework is that non-technical stakeholders often find the five functions (Identify, Protect, Detect, Respond, and Recover) more relatable than other security frameworks that list numerous control categories.
Building Blocks for Success
Here are some elements to prioritize when developing a cyber resilience program, along with examples of how museums approach each of the five NIST Framework functions.
Identify
Museums maintain an accurate inventory of assets, they check in visitors as they arrive, and they conduct employee background checks. Here are some key considerations for a cyber resilience plan:
- Maintain an accurate inventory of data assets rather than just physical devices.
- Map applicable regulations to data assets.
- Identify cloud services being used and responsibilities for securing data in the cloud.
Protect
Museums strive to make visits enjoyable and seamless, but they don’t neglect preventative controls. They install physical barriers around high value assets, and they may require additional checks before entering some exhibits. Cyber resilience plans should also include proactive controls:
- Operationalize security so every individual understands their role and incorporates security into their daily processes.
- Continuously train stakeholders so they have the skills needed to secure the assets entrusted to them.
- Maintain good technology hygiene, including regular patching, using supported operating systems, and implementing malware prevention tools.
- Strengthen technology architecture with risk-based segmentation.
- Strengthen authentication with multi-factor authentication, credential and privilege management tools, and device authentication.
Detect
Museums deploy pervasive monitoring tools such as security cameras and motion sensors to detect potential threats. Organizations should adopt similar threat detection capabilities in their cyber infrastructure:
- Implement protection and detection tools between different architecture segments.
- Ensure tools cover all major attack vectors (network, email, endpoint and cloud) and that teams can correlate attack information across vectors.
- Consolidate and protect logs from on-premises and cloud environments, authentication systems and security tools.
Respond
To minimize risk, museums empower guards to respond when preventative controls fail, they deploy on-demand barriers, and they install fire suppression systems. To minimize damage from attackers who bypass preventative controls:
- Strengthen detection and response capabilities (people, process and tools) to limit the time attackers can be active inside an environment.
- Practice regularly using tabletop exercises and red team engagements. Include non-security stakeholders such as marketing, finance and legal executives in these exercises.
Recover
Museums use processes and tools, including insurance policies and law enforcement, to recover from damaging events. Include recovery capabilities in a cyber resilience plan:
- Engage with leadership before a crisis occurs to identify recovery goals, implement appropriate tools and processes, and put the right contracts and policies in place.
- Evaluate and understand the benefits provided by cyber insurance policies.
- Implement proactive incident response retainers so help is available when needed.
- Regularly test backup and recovery tools and processes.
Defining Cyber Resilience Success
While these examples are not exhaustive, they provide an overview of the most important elements needed in an effective cyber resilience strategy.
How do you report on whether your strategy is working? Stakeholders often just want to know, “Are we secure?” The next post in this blog series will explore how to provide metrics about a security program, including pitfalls to avoid and suggestions for measuring the effectiveness of efforts.
This post was first first published on
‘s website by Christian Schreiber. You can view it by clicking here

