It’s Time to Update Your Drupal Now!
Drupal just recently released two major versions, which piqued our researchers’ interest. Once the team got to work on the two latest versions of Drupal, they quickly found that both versions were vulnerable to being exploited. Later, it is was confirmed by Drupal that every maintained version of Drupal (7.x, 8.8.x, 8.9.x) were easily exploitable by the same techniques.
As part of our ongoing mission to help organizations develop and deploy more secure software and applications, and in light of Checkmarx’s expanded insight into the open source security landscape with its recently launched SCA solution, the Checkmarx Security Research Team analyzed including enterprise and government sites worldwide.
The Checkmarx Security Research Team identified a document object model-based cross-site scripting (DOM XSS for short) vulnerability in Drupal Core. This type of XSS attack is achievable if a web application enters data to the DOM without being appropriately sanitized. In this case, an attacker can manipulate their input data to include XSS content on the web page, for example, malicious JavaScript code, which in-turn would be consumed by Drupal Core itself.
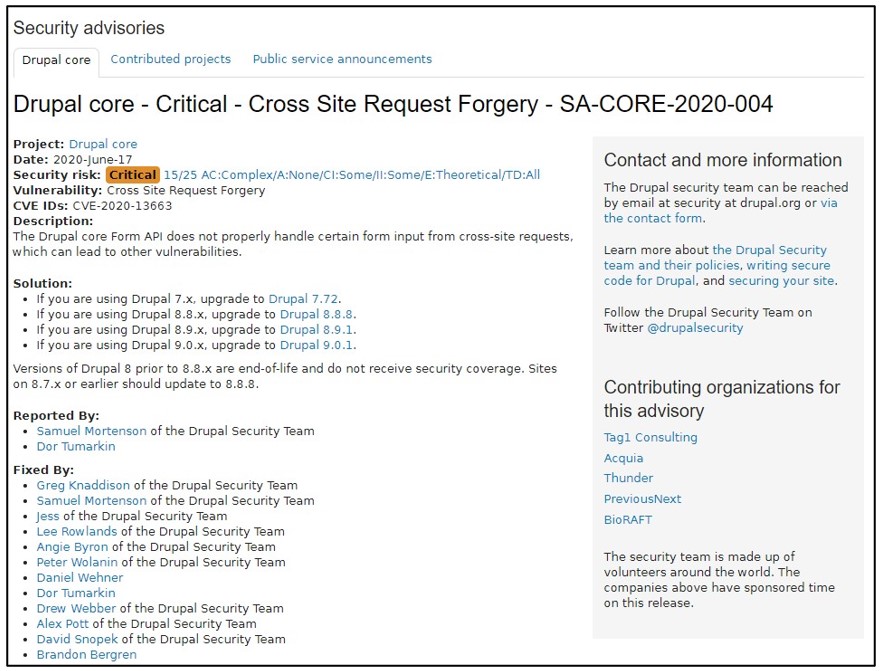
These issues were discovered by Dor Tumarkin of the Checkmarx Security Research Team. Drupal acknowledged and patched the vulnerability, assigning it CVE-2020-13663. More information can be found below and on their security advisories page.
Drupal labeled the Security Risk of this vulnerability our team discovered as follows:
An attacker abusing this vulnerability can take over the administrator role of a Drupal-based website and get full control that allows changing of content, creating malicious links, stealing sensitive or financial data, or whatever else comes to mind.
When the vulnerability was first discovered, the Checkmarx Security Research Team responsibly notified Drupal of its findings. Our team was asked to advise Drupal’s team after our disclosure, which we willingly did.
- Risk: Critical
- Access Complexity: Complex
- Authentication: All/Anonymous Users
- Confidentiality Impact: Certain Non-Public Data is Released
- Integrity Impact: Some Data Can be Modified
- Exploit (Zero-day Impact): Theoretical or White-hat (no public exploit code or documentation on development exists)
- Target Distribution: All Module Configurations are Exploitable
In accordance with Drupal’s disclosure guidelines and to give its users adequate time to update their software, Checkmarx will refrain from publishing a more technical report showing an in-depth walkthrough and proof-of-concept of exploiting this vulnerability for 60 days. In the meantime, we strongly encourage Drupal users to take action on recommended updates.
After we disclosed the vulnerability, the Drupal team’s sense of urgency and professionalism was quite notable, and a fix was made available within a week of our disclosure.
Checkmarx customers using Checkmarx Software Composition Analysis (CxSCA) have already been automatically notified to update Drupal while running a scan of their code base.
At this time, Checkmarx highly recommends that anyone using Drupal update the version in use immediately to the latest release, which contains a fix for this vulnerability.
For more information or to speak to an expert about how to detect, prioritize, and remediate open source risks in your code, contact us.
This type of research activity is part of the Checkmarx Security Research Team’s ongoing efforts to drive the necessary changes in software security practices among all organizations in an effort to improve security for everyone. Checkmarx is committed to analyzing the most prominent open source packages to help development teams ship more secure software and improve their software security risk posture. Our database of open source libraries and vulnerabilities is cultivated by the Checkmarx Security Research Team, empowering CxSCA with risk details, remediation guidance, and exclusive vulnerabilities that go beyond the NVD.