Intelligence-Led Threat Protection for SaaS-Mobile Workforce — FireEye Detection With CipherCloud
When organizations turn to cloud apps to support the remote workforce and maintain business continuity, bad actors will follow. Employees working from home can expect any kind of attack, including advanced social engineering on collaboration apps such as Office 365 and Slack.
IT teams have it particularly rough—they are scrambling to deal with the new norm of supporting a remote workforce with employees connecting direct-to-cloud apps and bypassing traditional on-premises security. Keeping track of these employees, along with gaining visibility into the data they share in the cloud, can consume even the largest team’s resources and can often feel impossible.
At FireEye, we want to expand detection and response into our customers’ cloud and SaaS usage. By combining FireEye Detection On Demand and CipherCloud CASB+, this joint solution analyzes content in real-time across SaaS applications and cloud repositories. The combination is designed to deliver high fidelity results as to whether or not an object shared via SaaS and Cloud applications is malicious. Should evil be detected, the content is blocked by CipherCloud in real time, helping to protect employees, partners and customers.
Who is CipherCloud?
CipherCloud is a leader in cloud security helping the world’s largest organizations take full advantage of the cloud and web without sacrificing security. Their recognized data protection expertise forms the foundation for the industry’s only zero-trust CASB solution, providing seamless zero-trust security across all clouds with unified policies, trusted data protection, and automatic compliance for the cloud-mobile era. CipherCloud CASB+ provides deep levels of data protection and real-time data access control to provide an immediate solution for challenging cloud security and compliance problems.
How Does the Integration Work?
It’s simple: CipherCloud has built a connection to FireEye Detection On Demand that allows any content encountered across a SaaS/cloud application to be submitted for review. Customers have the ability to customize this for their business needs, allowing them to choose what content is chosen and from what user groups, and how they want to deal with the malicious content (i.e. block, allow, send alerts, etc.). The following chart highlights how our technology works together.
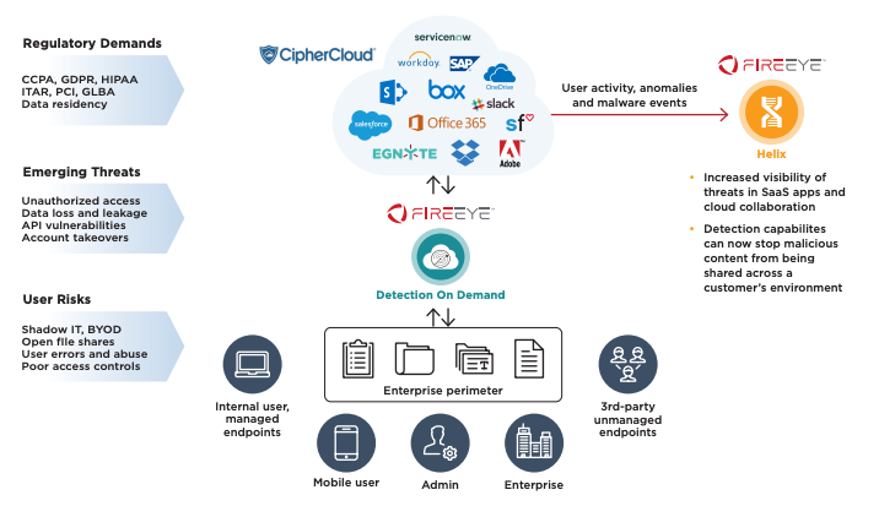
Existing customers of FireEye Helix and CipherCloud can also start leveraging the integration to ingest all of CipherCloud logs into FireEye Helix, in mere minutes. By utilizing FireEye Helix Connect, customers only need to select the CipherCloud tile and enter their API key and CipherCloud domain. Customers will then have access to all CipherCloud activity, violations and anomaly data that is generated through their CASB, enriched with Mandiant Threat Intelligence.
FireEye has created seven custom alert rules, which is part of a CipherCloud Rule Pack that automatically assigns a risk level to each alert that CipherCloud generates. These rules work out of the box today and can also be modified to prioritize alerts that are most relevant. Additionally, FireEye Helix has the ability to help customers visualize data and alerts through dashboards. The following CipherCloud dashboard has been created and is available for use in Helix, and customers can also modify it to reflect the data that they want to review.
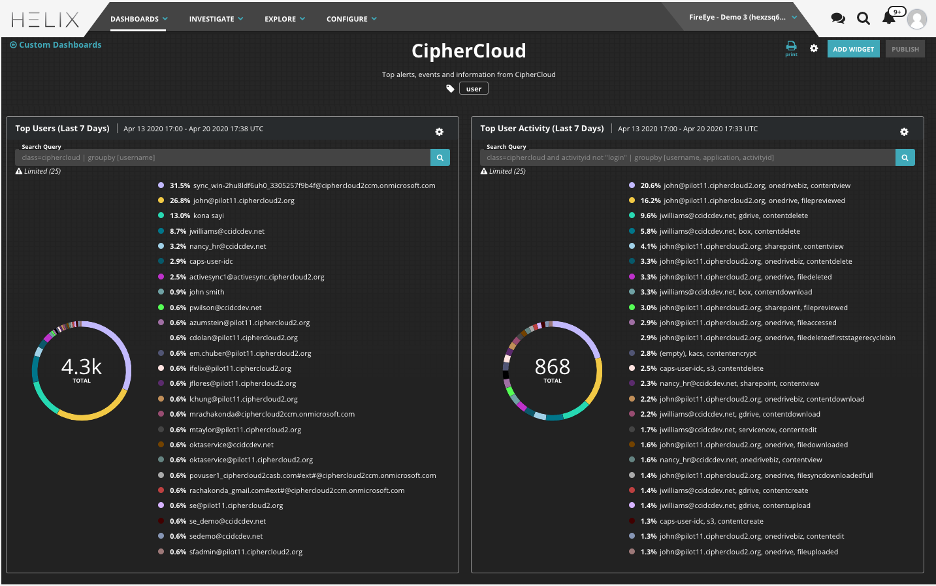
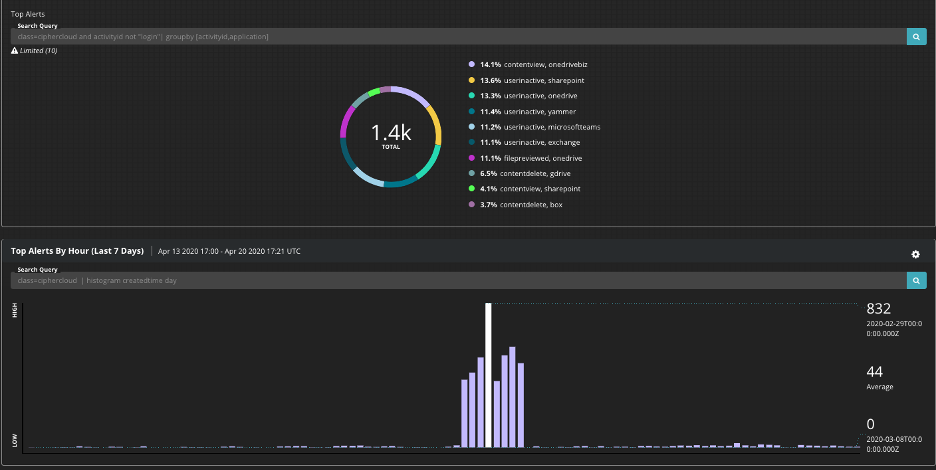
More Information
This integration is already being used by Fortune 1000 companies and top medical universities to gain valuable insight into their cloud security. Their security analysts have instant access to what is happening across their cloud services by using FireEye Helix. To learn more about this integration visit the FireEye Market and enable it now on FireEye Helix Connect. You can also view our recent webinar.
This post was first first published on
‘s website by Christopher Unick. You can view it by clicking here

