FireEye Success Story: Solutions and Strategies for Elections Part Four — Post-Election Improvement
Never has Benjamin Franklin’s words been more relevant. One of the greatest minds of the Founding Fathers of the United States was not only a great inventor, he was a significant contributor towards revolutionizing civil servant duties. His efforts to raise public awareness about the need to improve firefighting techniques resulted in a very famous quote:
“An ounce of prevention is worth a pound of cure.”
When this quote is applied towards the ever evolving and dangerous world of cyber security, it suggests that it’s easier to take responsible efforts towards stopping or preventing something nefarious from happening in the first place than to repair the damage caused by successful cyber criminal and state-sponsored adversaries during an election cycle.
In this final post in our four-part blog series on cyber defense of elections, we address the importance of post-election vigilance centering on the practice of good cyber hygiene as well as strengthening and securing of safeguards that impact the overall cyber security posture of the environment. The end of an election is not the time to let our guard down, rather a time for self-assessment and self-improvement. But first, if you haven’t already, check out the first three posts in this series on solutions and strategies, pre-election preparedness and the War Room.
Rinse & Repeat
Pre-election preparedness and the War Room are often very chaotic. After the election, it is advisable to have a post-mortem report that highlights investigations, threats and tangible operational risks observed during that phase. FireEye Mandiant has created reports that review activities performed so remediation efforts can be prioritized in advance of the next election cycle. Developing that roadmap is critical because we all know that any given year could be sprinkled with special elections and primaries, shortening the windows of opportunity to implement efficiencies.
The lack of standardized response towards threat events has often been observed in state and local boards of elections. Just ask yourself, what would you do if your website was hacked and you no longer had control of what was being communicated to the public? Worse yet, what if malware spread that impacted the integrity of voting data?
One way to bridge that gap is to expand awareness. Mandiant Cyber Security Training courses can build technical skillsets, such as Windows Enterprise Incident Response. Another way to reduce the risk of cyber security events would be to define a clear plan of communication along with an incident response plan. Sharpening these operational proficiencies not only improves response time, it can help identify technical weakness that are in need of fine-tuning. Mandiant Cyber Defense Center Development, one of our proactive services, assesses essential competencies and core capabilities of a cyber security program. Other proactive services such as Response Readiness Assessments or Cloud Assessments can be utilized to evaluate technical controls and will result in strengthening safeguards for cyber defense.
Expand Oversight & Monitoring
Boards of elections often have limited or overstretched security teams, and that presents a challenge when trying to keep up with an ever-evolving threat landscape. Mandiant has provided security experts in an executive advisory role for the CISO, assisting with implementation of the security roadmap. Executive support benefits boards of elections because their expertise will coordinate and prioritize the execution of initiatives that result in maturing the overall security program.
It is well known that preparation for the next election cycle takes significant effort. Bringing systems back online, whether reimaged or through a vulnerability and patch management processes, takes up valuable time. When assessing environments, it is recommended that new tools be explored to improve environmental oversight.
In previous posts we explained how FireEye technologies (Endpoint Security, Email Security, and Network Security) combined with FireEye Managed Defense are deployed to actively monitor and hunt for threats in the environment. This is an excellent first step. It now allows those security teams to expand environmental oversight by considering other security technologies. One such tool is Mandiant Security Validation (formerly Verodin). It will automate the assessment of an organization’s security posture, allowing for the exposure of adversarial attacks to be quantified. Exposing these types of vulnerabilities is very valuable because they are proactive measures that allow the organization to optimize controls involving security technologies.
Everything Considered
Benjamin Franklin’s article to the “The Pennsylvania Gazette” pleaded with citizens to take care of the coals that they move from one room to the next. It takes just one dormant coal falling through the holes of your wooden floors to spark at midnight, “you may be forced, as I once was, to leap out of your windows.” The same sentiment holds true for cyber criminal and state-sponsored adversaries.
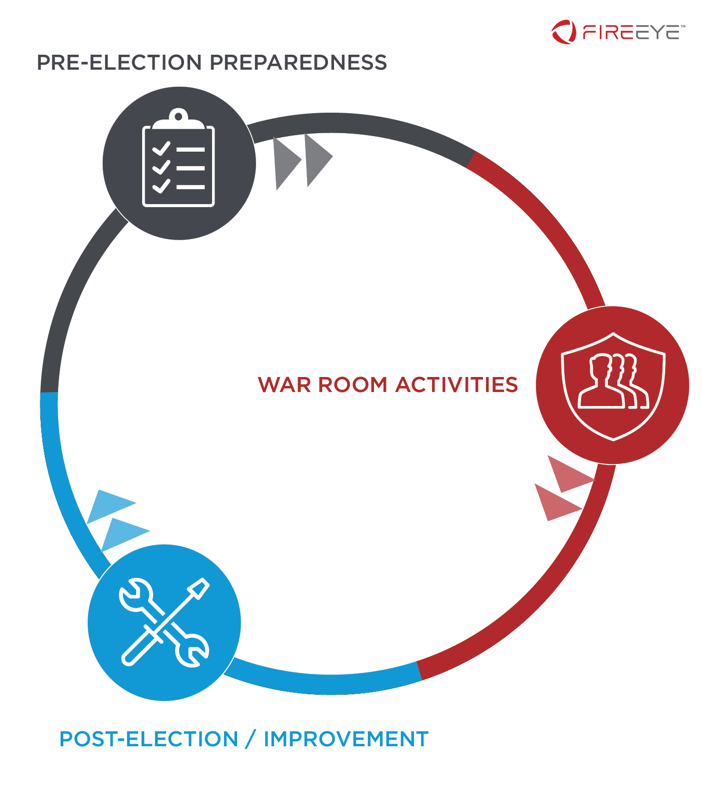 Protecting and securing the upcoming election has never been more important. Adversaries from all over the world have the potential to harm and disrupt our electoral process for self-interest or nefarious reasons. This blog series discusses a defined lifecycle relating to the defense of our citizens’ voice and the integrity of our elections. Mandiant’s three-phase cyclical process (pre-election preparedness, War Room support and post-election improvements) of implementing comprehensive cyber security protection is flexible, has multiple program models at different entry points, and therefore can provide support at the county, city or state level.
Protecting and securing the upcoming election has never been more important. Adversaries from all over the world have the potential to harm and disrupt our electoral process for self-interest or nefarious reasons. This blog series discusses a defined lifecycle relating to the defense of our citizens’ voice and the integrity of our elections. Mandiant’s three-phase cyclical process (pre-election preparedness, War Room support and post-election improvements) of implementing comprehensive cyber security protection is flexible, has multiple program models at different entry points, and therefore can provide support at the county, city or state level.
Check out our election security page for more.
This post was first first published on
‘s website by Chris Pocoroba. You can view it by clicking here

