Tips for Securing Remote Work from Homes to Corporate Networks
On a recent webinar, Ryan Murphy, a founding team member of VMware Carbon Black, interviewed Cybersecurity Strategists, Tom Kellerman and Rick McElroy on how to work remotely, yet securely. What resulted were some fantastic tips on how to secure remote work access from their homes to the corporate network. This article summarizes the highlights, but definitely listen in to the recorded webinar for a deeper dive into this important topic.
Three Challenges to Securing Remote Workers
Challenge #1: Rapid Increase in Distributed Endpoints
With the lockdown from Covid-19, many companies had to quickly purchase and distribute laptops to enable workers to work from home. In fact, endpoints have increased by more than 70 percent since the lockdowns. Some of these are personal devices.
This is causing security teams to try to find ways to push security updates to these new and sometimes personal remote devices. Every team has seen a huge surge in traffic from unknown networks and it is incredibly difficult to find a balance between remote access and security.
Challenge #2: Rapid Increase in Attack Volume
Instead of being slowed down by the pandemic, attackers are more active than ever with opportunistic attacks. As shown in recent data analysis from VMware Carbon Black, there have been huge spikes in attacks since Covid-19 including a 148 percent increase in ransomware attacks and a 667 percent increase in phishing attacks. Adversaries are fully aware that we are weaker in our remote offices and that the attack surface is greater. They are fully taking advantage of this to attempt to steal credentials and infiltrate targeted networks.
Nation States attackers are also taking advantage of COVID-19 fears. Emergencies previous to this were regional. This is the first on a global scale where opportunity abounds for attackers. And unfortunately, Healthcare and Government State, Local and Education organizations are particularly vulnerable as they are attempting to handle the pandemic changes and enable remote work using legacy systems.
Challenge #3: Shift in Security Workflows
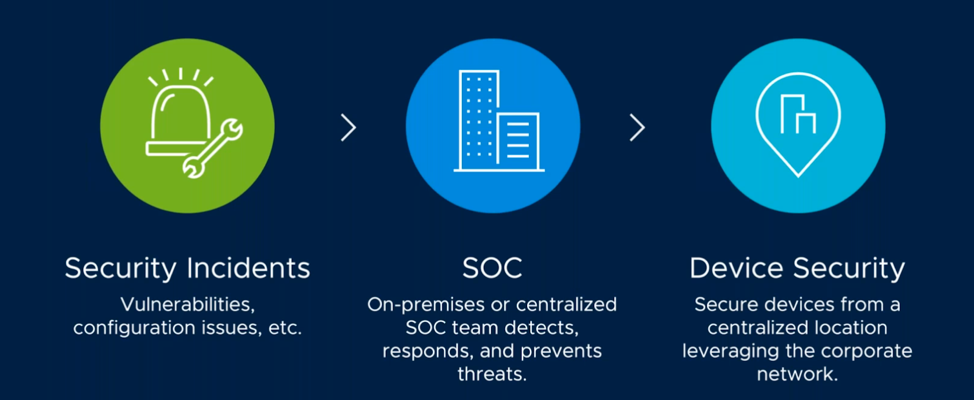
In the traditional security workflow, security incidents flow to a centralized SOC that analyzes and responds to the threat. The team also works to prevent new threats and utilizes security solutions and processes based on securing devices in a centralized location running off the corporate network. While there is some remote work in the traditional model, most security programs are built around the concept of workers centralized in offices.
Traditional Security Workflow Pre-Covid
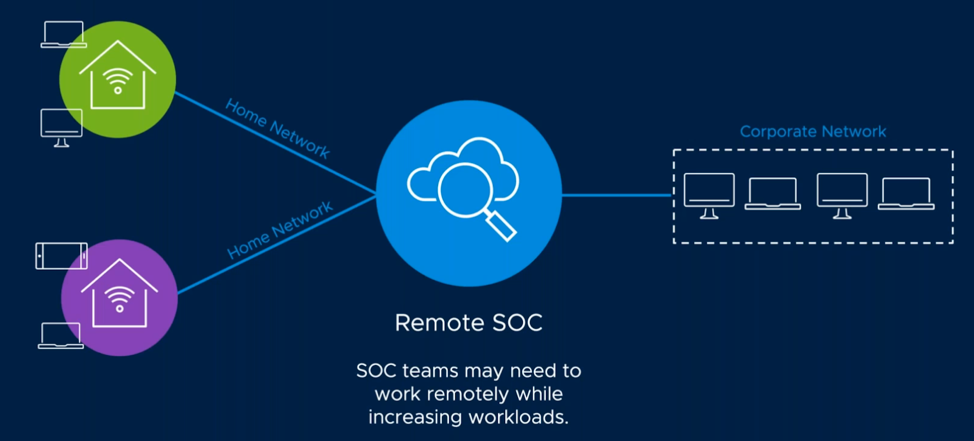
That workflow was suddenly changed on March 6th. Now home networks are monitored by a remote SOC team. From there, users gain access into the corporate network. The SOC team used to have visibility at the endpoints with EDR solutions. In this new workflow, there is no visibility into home routers, which is a huge challenge.
Sudden New Security Workflow
Tips for Securing the Remote Endpoint
Home networks are polluted. There are often multiple family members on the same network using a variety of insecure devices. Here are some basic tips to help secure these remote endpoints:
- Get two home networks – Put the family on one network and the corporate device on the other.
- Limit privileges – Just-in-time administration should be the approach during this time for both allowing access within a home and to the corporate network.
- Make devices follow social distancing – Users need to ensure mobile devices follow social distancing rules by keeping them six feet apart. Ideally users should isolate their work computer in a room with no other smart devices.
- Make sure devices are updated – Most home routers were not made with mass management in mind. Communicate to home users about keeping firmware updated and patched. Education and training will be needed here. Make Tuesday nights security nights as that’s when the updates come out. Of course, this might be a good time to change your policy on auto-updating and turn it on for users. It is easier to roll back a bad update than it is to hunt an attacker on your network.
- Consider MFA – Multi-factor authentication on work devices and mobile devices is the simplest way to make it more difficult for opportunistic attackers.
- Consider extra measures for Executives – Your security jobs have expanded to the homes of your executives. Things like secure voice communications may be needed to ensure confidential information is not accessed.
Tips for Securing Collaboration Applications
Along with dealing with home networks comes the challenge of keeping users secure while using virtual meeting software. There has been a huge increase in virtual meetings and a huge increase in attacks focused on this medium. To keep meeting information secure, rollout these tips for users and the security team:
- User tip: Set a password and use a VPN. Have them set a new password before every meeting. Additionally, take advantage of the waiting room feature so you can control attendees in your meeting.
- User tip: Be smart with meeting names. Make sure users avoid labeling sensitive meetings as “top secret” or “2020 Strategy” that would make them clearly of interest to adversaries.
- SOC tip: Utilize Threat Hunter and Live Query. Use Threat Hunter to detect and respond to issues and Live Query to block unknown binaries with application control/whitelisting.
- SOC tip: Set preventative rules. Use application control to set preventative application rules that separate home and work networks.
Tips for CISOs to be Proactive
The reality of having unplanned remote workers is that those users will be compromised. What CISOs need to be worried about is when they leapfrog into your corporate network, will they be able to island hop to attack your constituency? They could do this using watering hole or network-based attacks, or reverse business email compromise pushing out fileless malware payloads against your partners, board members, customers, etc.
The worst case scenario is no longer loss of data. It is rather that your digital transformation efforts will be used against you to attack your constituency. And this scenario is made more likely as CISOs are challenged with reduced visibility, SOC burnout, workload management and having to sacrifice security for business continuity.
Here are a few tips for CISOs to mitigate these risks:
- Be a figurehead for positive change – CISOs should be leaders in training employees. Drive positive change and behavior like Multi-Factor Authentication (MFA) versus scaring them with threats. One idea is to put out one-minute videos each week with simple things that employees can do to help the company get more secure.
- Aggressively build in resiliency – We can learn a lot about business continuity from the energy industry. After the 2003 blackout in the Northeast, energy companies expanded their attack surfaces by creating a lot more remote usage, accessibility, overlaying wireless on top of fiber, etc.. Basically building in resiliency. The rest of the industries now need to do the same.
- Expand threat hunting to remote devices – Being able to securely remote access needs to go beyond an overreliance on encryption and VPNs. Security teams need to harden these machines and expand threat hunting to remote users—even the personal devices of executives.
- Make security cloud-native – Now and likely into the future your SOC teams will need to keep employees connected from anywhere. Pick a cloud-native security stack to enable this.
- Add layered prevention – Stop never-before-seen attacks with machine learning and behavioral analytics
Security teams had an existing set of projects, both strategic and tactical, that they were working before COVID-19. CISOs need to re-evaluate those lists and change the priorities. Focus should be given to resiliency projects and cloud-native security solutions that can enable SOC teams to work in this new normal while preventing attackers from doing irreparable damage to the brand.
The post Tips for Securing Remote Work from Homes to Corporate Networks appeared first on VMware Carbon Black.