Security Without Barriers, Part One: A New Cyber Security Narrative
Information security professionals often use defense-in-depth
analogies to describe their security goals. For example, it’s common
to conjure an image of a castle and moat to explain cyber security
strategy to stakeholders. These visualizations are often accompanied
by an explanation that if an attacker gets past one layer, the next
layer will stop them.
One problem with defense-in-depth analogies is that the traditional
perimeter—i.e. the moat—is mostly gone today. Digital transformation
projects, adoption of cloud computing solutions, and the growing use
of mobile and remote computing devices have dramatically changed how
technology is deployed and used. Perimeter security solutions, such as
firewalls and VPNs, cannot be relied upon to protect digital assets.
A more fundamental problem with using defense-in-depth analogies to
explain your security strategy is they describe security success in
absolutes: Prevent an attacker from getting in.
Unfortunately, security teams face an asymmetric threat where
inexpensive attacks can, and often do, evade organizations’ expensive
cyber defenses. This reality can be summed up with two assumptions:
- No technical solution can prevent all attacks all the
time. - There will always be bad actors looking to exploit this
security gap.
Because of this unbalanced threat landscape, many security leaders
have adopted cyber resilience strategies. They balance investments
that protect against attacks with other investments that mitigate the
damage caused by attacks that get through the defenses.
We’ll explore the components of cyber resilience more in the next
blog post of this series. First, let’s think about how to describe
cyber resilience to stakeholders.
Changing the Security Narrative
Describing a cyber resilience strategy requires a vastly different
mental image than describing defense-in-depth strategies. Rather than
explaining how a castle’s defensive layers keep attackers out,
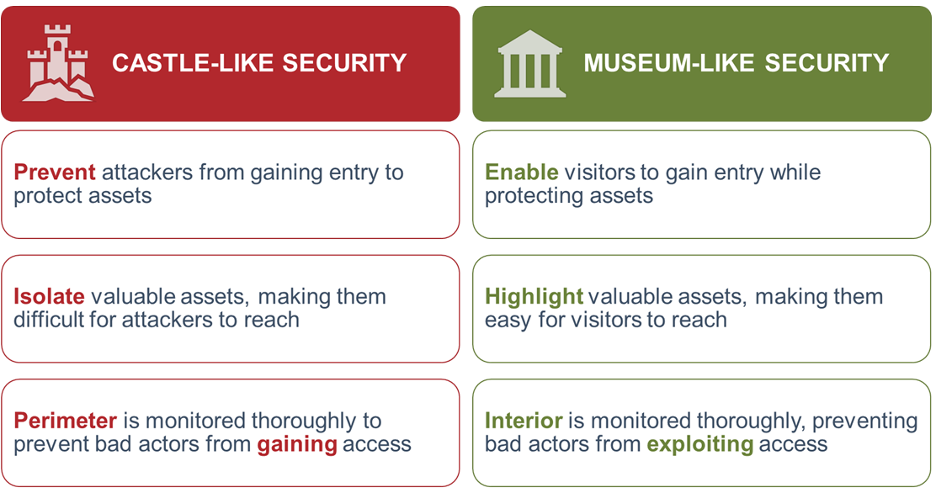
think instead about how a museum protects its assets.
The core principle is the same: Protect valuable assets. However,
the methods and strategies used to achieve this goal are very different.
Instead of hardening the perimeter to keep attackers out, a museum
must create an open and welcoming environment. They need to draw
visitors in, often allowing them within inches of their most valuable
displays and exhibits. As a result, museums assume bad actors can
easily get inside the perimeter. Their strategy shifts from
preventing access to preventing exploitation of access.
There are other differences between describing a “castle-like”
defense-in-depth cyber security strategy versus a “museum-like” cyber
resilience strategy.
At first glance, describing your cyber security strategy as a museum
seems odd. However, if you think about how most IT organizations
define success, they’re more like a museum than a fortress. IT leaders
design solutions that are welcoming to visitors, that are easy to use,
and that still protect critical assets from theft or misuse. Adopting
similar language and goals to describe your security strategy helps
align cyber security messaging with other IT leaders’ goals.
Heading Toward Cyber Resiliency
Security leaders need a new narrative to describe their security
strategies. By adopting cyber resilience strategies instead of
prevention-focused defense-in-depth strategies, you also help your
organization better prepare for the asymmetric threat posed by cyber attackers.
The next post in this series will explore steps organizations can
take to build strong cyber resilience. We’ll build on the analogy of
how a museum protects assets and show concrete steps for implementing
cyber resilience within your organization.

