How Much Visibility is Enough?
To a truck driver, visibility depends on awareness of both obstacles directly in their path or tangential to their proximity. Like a pilot, truck drivers also prioritize safety, both theirs and that of other people on the road. Beyond that, their priority focuses on hitting tight delivery schedules that allow the hauling company to maximize profitability.
To an airline pilot, visibility requires unobstructed views for miles, across the horizon, to avoid any sudden reactions that would degrade the comfort and safety of passengers and crew members onboard. When visibility is compromised (or when an acceptable level of visibility can’t be achieved), pilots make adjustments to ensure minimal risk.
So, what does this have to do with cybersecurity? Security professionals also make adjustments based on the level of visibility they have. Technology, as it converges at an accelerated pace, plays a key role as well. Here at Forcepoint, we often refer to visibility across networks. We also refer to visibility in terms of protecting users and data.
Both pilots and truck drivers have to deal with external factors (bad weather, snow, fog etc.) outside their control that lead to increased risks against their objectives. Technology plays an increasingly important role in helping both of them make appropriate adjustments along the way.
There’s a multitude of ways network, data and user visibility can be achieved or instrumented. With the security center-of-gravity shifting to the cloud for companies across industries, it is more critical than ever that companies have impactful, actionable, and meaningful visibility across all vectors of communication.
Does that mean collecting every minute detail at every endpoint where a user interacts with company data? Does it mean installing technology that collects every packet coming across the wire? Does it mean filling up numerous disparate databases with a hodgepodge of structured and unstructured data? No, it does not.
Navigating a rapidly changing borderless security environment is challenging. Basic visibility isn’t good enough. Organizations should strive to achieve meaningful visibility. Getting there may require a re-examination of your organizations’ data and user protection strategies to gain this level of visibility.
Work to achieve meaningful visibility
- Visibility to how users interact with an organizations’ data and intellectual property (IP)
- Continuous evaluation of user interaction with data and devices/applications.
- Leveraging behavioral intelligence with meaningful data to identify and mitigate risks.
These core elements enable companies to gain deep visibility on the interaction between users, data, and applications to improve their data protection and compliance strategies. Most companies have a certain degree of network visibility. Even so, every company can improve.
Core elements of a robust strategy includes:
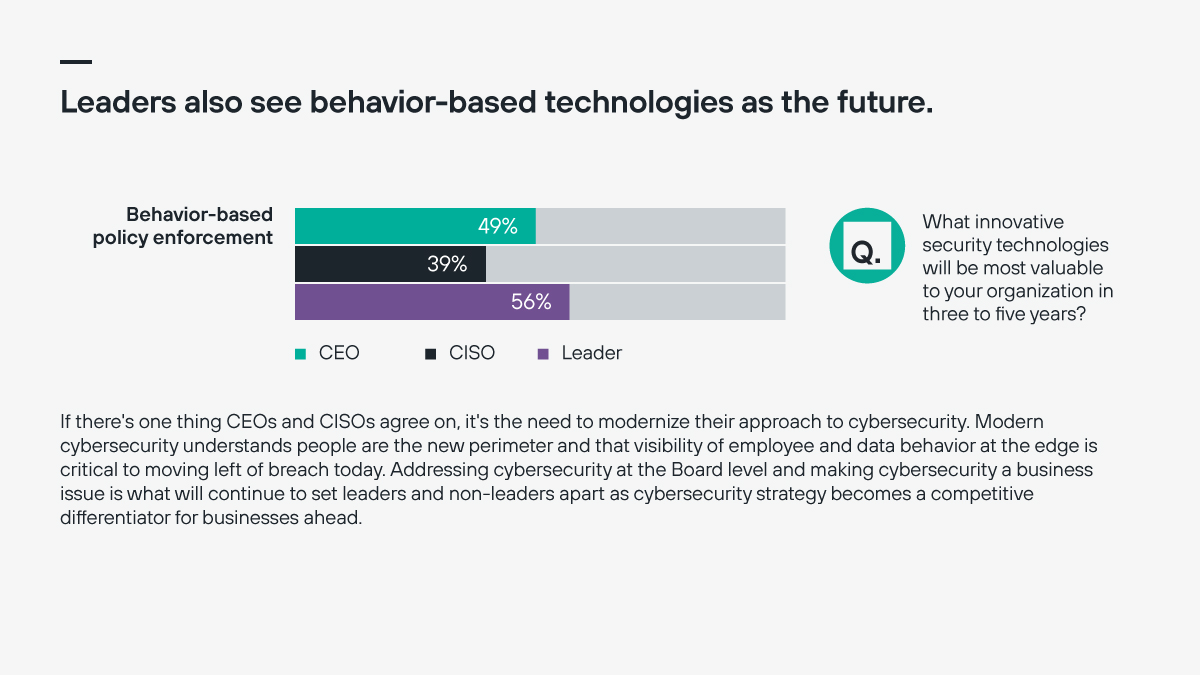
Understanding behaviors, especially in terms of how users interact with data across networks and devices is starting to emerge as a piece of the puzzle. That’s a big reason why more CEOs and CISOs are beginning to see behavior-based technologies as the future of cybersecurity.
Achieving meaningful visibility is even more important as organizations become increasingly reliant on cloud applications to go beyond maintaining business continuity and work to support large remote workforces as the new normal. This level of visibility provides the foundation for aligning processes, procedures, and technology to address the new era of digital transformation.
Security teams can achieve meaningful visibility by leveraging technology to shift our visibility from simply seeing what’s ahead of us to understanding how what we’re seeing can contribute to organizational risk, and proactively mitigating that risk.
If you’re interested in digging into how CEOs and CISOs see the future of cybersecurity, click on the previous link Read the Report button on the right to download the report conducted by WSJ Intelligence.
This post was first first published on Forcepoint website by Michael Crouse. You can view it by clicking here

