Think Fast: Time Between Disclosure, Patch Release and Vulnerability Exploitation — Intelligence for Vulnerability Management, Part Two
One of the critical strategic and tactical roles that cyber threat
intelligence (CTI) plays is in the tracking, analysis, and
prioritization of software vulnerabilities that could potentially
put an organization’s data, employees and customers at risk. In this
four-part blog series, FireEye
Mandiant Threat Intelligence highlights the value of CTI in
enabling vulnerability management, and unveils new research into the
latest threats, trends and recommendations. Check out our first post
on zero-day vulnerabilities.
Attackers are in a constant race to exploit newly discovered
vulnerabilities before defenders have a chance to respond. FireEye
Mandiant Threat Intelligence research into vulnerabilities exploited
in 2018 and 2019 suggests that the majority of exploitation in the
wild occurs before patch issuance or within a few days of a patch
becoming available.
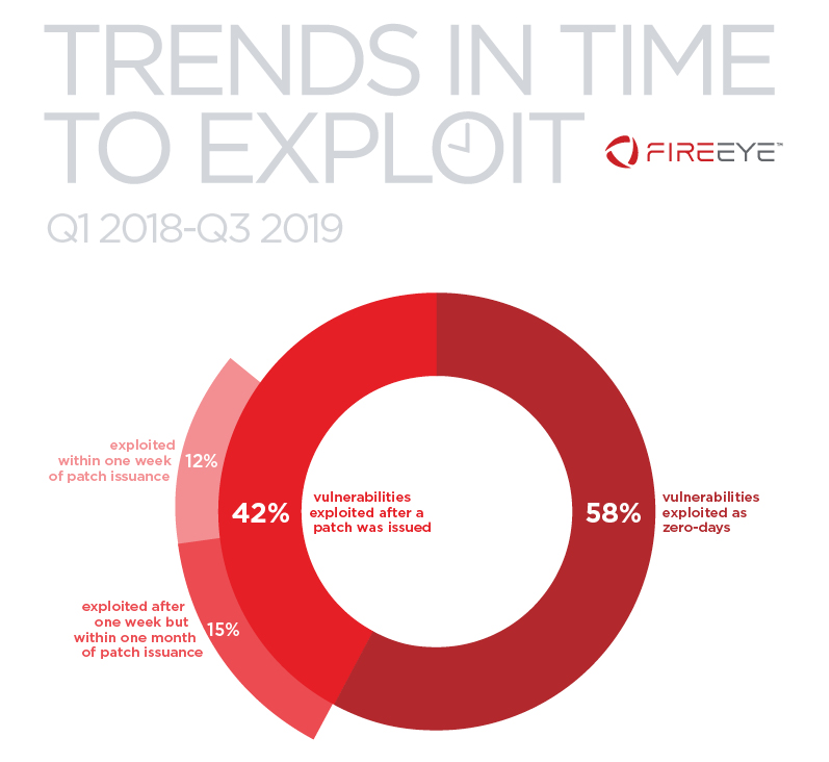
Figure 1: Percentage of vulnerabilities
exploited at various times in relation to patch release
FireEye Mandiant Threat Intelligence analyzed 60 vulnerabilities
that were either exploited or assigned a CVE number between Q1 2018 to
Q3 2019. The majority of vulnerabilities were exploited as zero-days –
before a patch was available. More than a quarter were exploited
within one month after the patch date. Figure 2 illustrates the number
of days between when a patch was made available and the first observed
exploitation date for each vulnerability.
We believe these numbers to be conservative estimates, as we relied
on the first reported exploitation of a vulnerability linked to a
specific date. Frequently, first exploitation dates are not publicly
disclosed. It is also likely that in some cases exploitation occurred
without being discovered before researchers recorded exploitation
attached to a certain date.
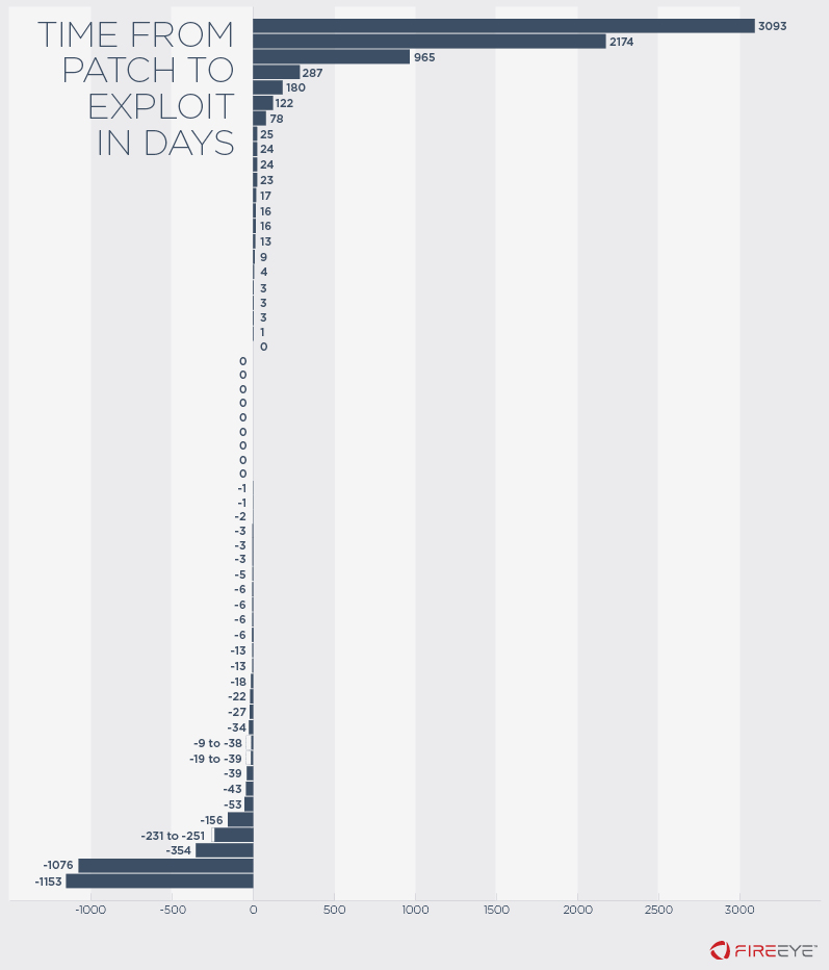
Figure 2: Time between vulnerability
exploitation and patch issuance
Time Between Disclosure and Patch Release
The average time between disclosure and patch availability was
approximately 9 days. This average is slightly inflated by
vulnerabilities such as CVE-2019-0863, a Microsoft Windows server
vulnerability, which was disclosed in December 2018 and not patched
until 5 months later in May 2019. The majority of these
vulnerabilities, however, were patched quickly after disclosure. In
59% of cases, a patch was released on the same day the vulnerability
was disclosed. These metrics, in combination with the observed
swiftness of adversary exploitation activity, highlight the importance
of responsible disclosure, as it may provide defenders with the slim
window needed to successfully patch vulnerable systems.
Exploitation After Patch Release
While the majority of the observed vulnerabilities were zero-days,
42 percent of vulnerabilities were exploited after a patch had been
released. For these non-zero-day vulnerabilities, there was a very
small window (often only hours or a few days) between when the patch
was released and the first observed instance of attacker exploitation.
Table 1 provides some insight into the race between attackers
attempting to exploit vulnerable software and organizations attempting
to deploy the patch.
|
Time to Exploit for Vulnerabilities First Exploited after a |
|
|
Hours |
Two vulnerabilities were successfully |
|
Days |
12 percent of vulnerabilities were exploited |
|
One Month |
15 percent of vulnerabilities were exploited |
|
Years |
In multiple cases, such as the first observed |
Table 1: Exploitation timing for patched
vulnerabilities ranges from within hours of patch issuance to years
after initial disclosure
Case Studies
We continue to observe espionage and financially motivated groups
quickly leveraging publicly disclosed vulnerabilities in their
operations. The following examples demonstrate the speed with which
sophisticated groups are able to incorporate vulnerabilities into
their toolsets following public disclosure and the fact that multiple
disparate groups have repeatedly leveraged the same vulnerabilities in
independent campaigns. Successful operations by these types of groups
are likely to have a high potential impact.
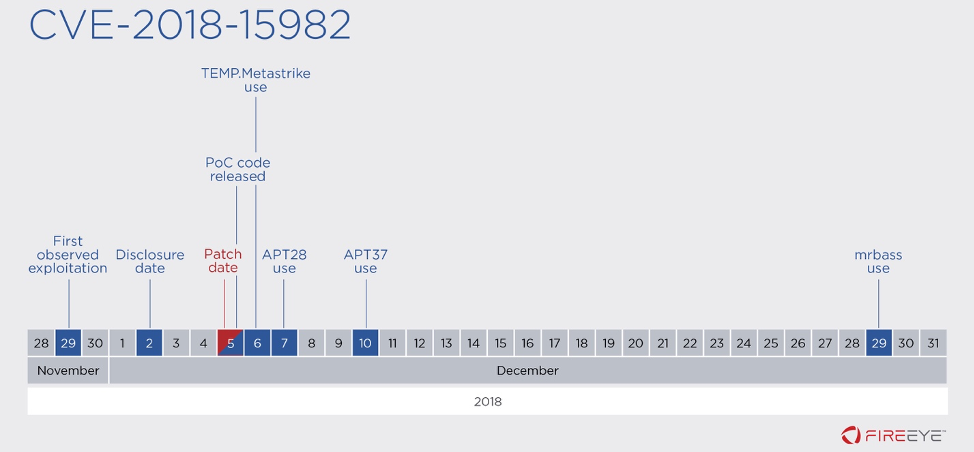
Figure 3: Timeline of activity for CVE-2018-15982
CVE-2018-15982: A use after free vulnerability in a file package in
Adobe Flash Player 31.0.0.153 and earlier that, when exploited, allows
an attacker to remotely execute arbitrary code. This vulnerability was
exploited by espionage groups—Russia’s APT28 and North Korea’s
APT37—as well as TEMP.MetaStrike and other financially motivated attackers.
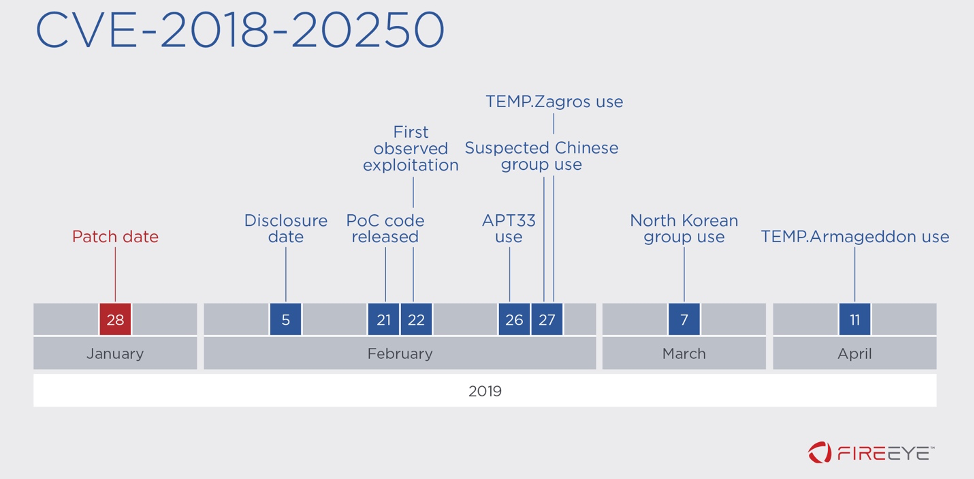
Figure 4: Timeline of activity for CVE-2018-20250
CVE-2018-20250: A path traversal vulnerability exists within the ACE
format in the archiver tool WinRAR versions 5.61 and earlier that,
when exploited, allows an attacker to locally execute arbitrary code.
This vulnerability was exploited by multiple espionage groups,
including Chinese, North Korean, and Russian, groups, as well as
Iranian groups APT33 and TEMP.Zagros.
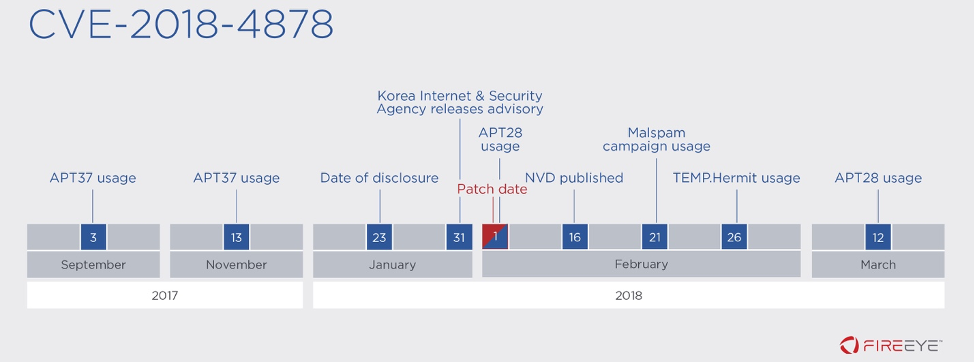
Figure 5: Timeline of Activity for CVE-2018-4878
CVE-2018-4878: A use after free vulnerability exists within the
DRMManager’s “initialize” call in Adobe Flash Player 28.0.0.137 and
earlier that, when exploited, allows an attacker to remotely execute
arbitrary code. Mandiant Intelligence confirmed that North Korea’s
APT37 exploited this vulnerability as a zero-day as early as September
3, 2017. Within 8 days of disclosure, we observed Russia’s APT28 also
leverage this vulnerability, with financially motivated attackers and
North Korea’s TEMP.Hermit also using within approximately a month of disclosure.
Availability of PoC or Exploit Code
The availability of POC or exploit code on its own does not always
increase the probability or speed of exploitation. However, we believe
that POC code likely hastens exploitation attempts for vulnerabilities
that do not require user interaction. For vulnerabilities that have
already been exploited, the subsequent introduction of publicly
available exploit or POC code indicates malicious actor interest and
makes exploitation accessible to a wider range of attackers. There
were a number of cases in which certain vulnerabilities were exploited
on a large scale within 48 hours of PoC or exploit code availability
(Table 2).
|
Time Between PoC or Exploit Code Publication and First |
Product |
CVE |
FireEye Risk Rating |
|
1 day |
WinRAR |
CVE-2018-20250 |
Medium |
|
1 day |
Drupal |
CVE-2018-7600 |
High |
|
1 day |
Cisco |
CVE-2018-0296 |
Medium |
|
2 days |
Apache |
CVE-2018-11776 |
High |
|
2 days |
Cisco |
CVE-2018-0101 |
High |
|
2 days |
Oracle |
CVE-2018-2893 |
High |
|
2 days |
Microsoft |
CVE-2018-8440 |
Medium |
|
2 days |
Drupal |
CVE-2019-6340 |
Medium |
|
2 days |
Atlassian |
CVE-2019-3396 |
High |
Table 2: Vulnerabilities exploited within two
days of either PoC or exploit code being made publicly available, Q1
2018–Q3 2019
Trends by Targeted Products
FireEye judges that malicious actors are likely to most frequently
leverage vulnerabilities based on a variety of factors that influence
the utility of different vulnerabilities to their specific operations.
For instance, we believe that attackers are most likely to target the
most widely used products (see Figure 6). Attackers almost certainly
also consider the cost and availability of an exploit for a specific
vulnerability, the perceived success rate based on the delivery
method, security measures introduced by vendors, and user awareness
around certain products.
The majority of observed vulnerabilities were for Microsoft
products, likely due to the ubiquity of Microsoft offerings. In
particular, vulnerabilities in software such as Microsoft Office Suite
may be appealing to malicious actors based on the utility of email
attached documents as initial infection vectors in phishing campaigns.
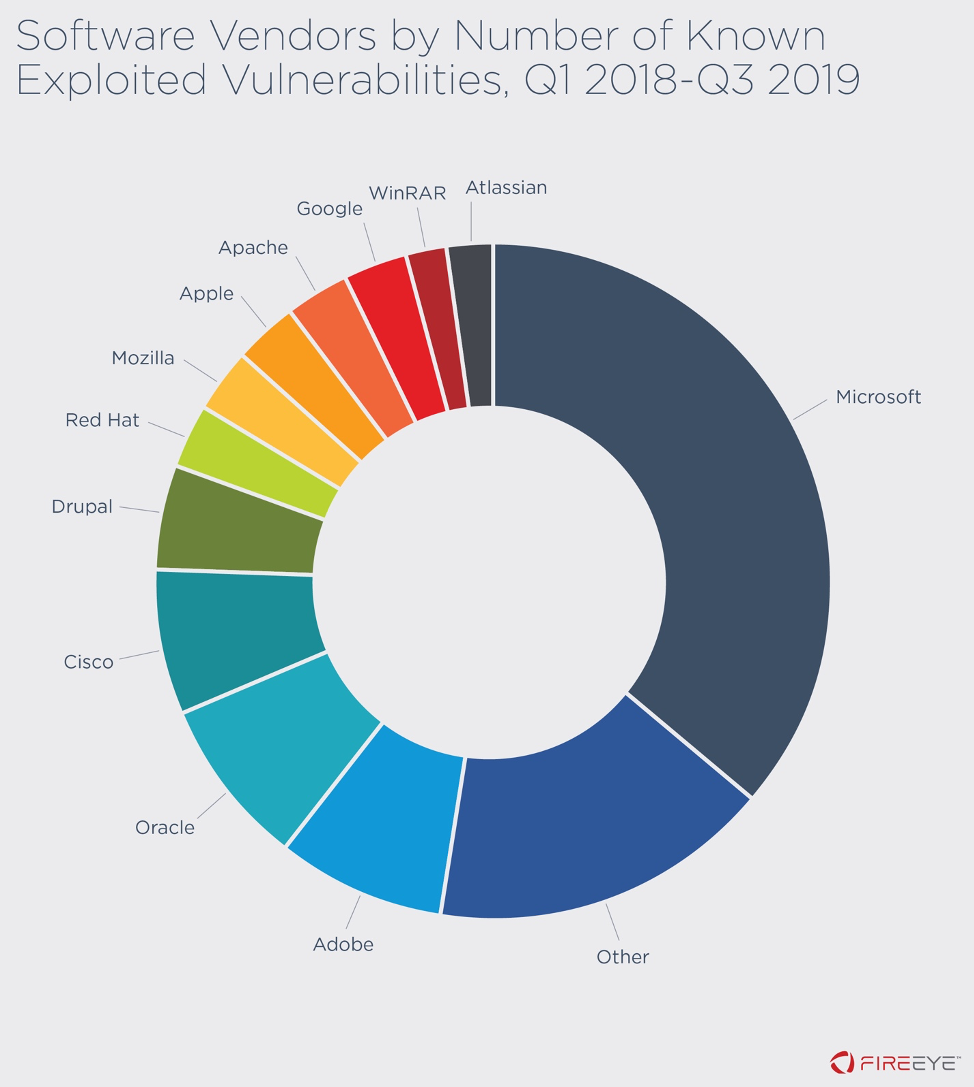
Figure 6: Exploited vulnerabilities by
vendor, Q1 2018–Q3 2019
Outlook and Implications
The speed with which attackers exploit patched vulnerabilities
emphasizes the importance of patching as quickly as possible. With the
sheer quantity of vulnerabilities disclosed each year, however, it can
be difficult for organizations with limited resources and business
constraints to implement an effective strategy for prioritizing the
most dangerous vulnerabilities. In upcoming blog posts, FireEye
Mandiant Threat Intelligence describes our approach to vulnerability
risk rating as well as strategies for making informed and realistic
patch management decisions in more detail.
We recommend using this exploitation trend information to better
prioritize patching schedules in combination with other factors, such
as known active threats to an organization’s industry and geopolitical
context, the availability of exploit and PoC code, commonly impacted
vendors, and how widely software is deployed in an organization’s
environment may help to mitigate the risk of a large portion of
malicious activity.
Register today to hear FireEye Mandiant Threat Intelligence experts
discuss the latest in vulnerability
threats, trends and recommendations in our upcoming April 30 webinar.

