Amid COVID-19, Global Orgs See a 148% Spike in Ransomware Attacks; Finance Industry Heavily Targeted
Cyber criminals often exploit fear and uncertainty during major world events by launching cyberattacks. These attacks are often performed with social engineering campaigns leveraging malicious emails that lure victims to install malware that steals financial data and other valuable personal information or, in some cases, turns a user’s computer into a crypto mining zombie.
In light of the COVID-19 surge, we looked into attack data from the VMware Carbon Black Cloud to determine the shift to remote work, how cyber attackers have stepped up their campaigns, when these campaigns are being launched, and what industry has been most frequently targeted.
Increases in Remote Working
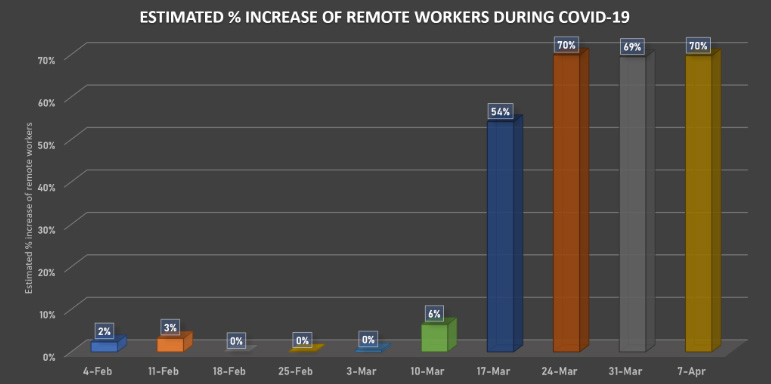
According to VMware Carbon Black analytics, there has been a clear shift to remote working tied to self-isolation orders. Between February 4, 2020 and April 7, 2020, we’ve seen an estimated 70% increase in remote work.
NOTE: This data does not include people who were already working from home and/or commuting between their homes and offices. The percentages are estimates based on aggregated metadata collected by the VMware Carbon Black Cloud sensor.
Resource: To help with the increase in remote work, we’ve compiled a list of some of the key things you can do to ensure your defenses are up—on or off the corporate network.
Increased Ransomware & Spikes Correlated to Notable Coronavirus News
In March 2020, ransomware attacks increased 148% over baseline levels from February 2020.
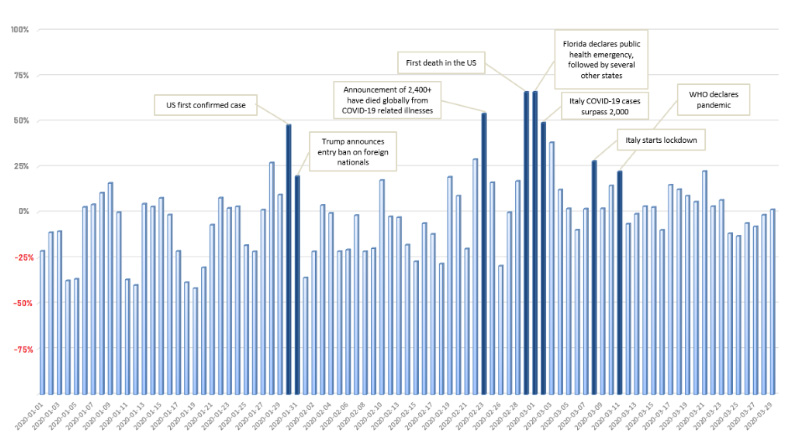
Notable spikes in attacks can also be correlated to key days in the COVID-19 news cycle, suggesting attackers are being nefariously opportunistic and leverage breaking news to take advantage of vulnerable populations.
Among the notable spikes seen in our data:
January 30, 2020 – 48% spike in attacks over baseline levels as the U.S. announces its first COVID-19 case
January 31, 2020 – a 20% spike in attacks over baseline levels as Donald Trump announces a U.S. entry ban on foreign nationals
February 23, 2020 – 54% spike in attacks over baseline levels on the day it was announced that more than 2,400 people have died globally from COVID-19 related illnesses
February 29, 2020 – 66% spike in attacks over baseline levels on the day multiple U.S. states declared public health emergencies
March 1, 2020 – 66% spike in attacks over baseline levels on the day the first COVID-19 death was announced in the United States
March 2, 2020 – 49% spike in attacks over baseline levels as Italy COVID-19 cases surpass 2,000
March 8, 2020 – a 28% spike in attacks over baseline levels on the day Italy declares a public lockdown
March 11, 2020 – 22% spike in attacks over baseline levels as WHO declares COVID-19 a pandemic
Relative Percentage Increase & Decrease By Day For Notable Alerts Observed In VMware Carbon Black Data
Note: “Baseline” is represented on the Y-Axis by 0% in the chart below
Attackers Heavily Target the Finance Industry
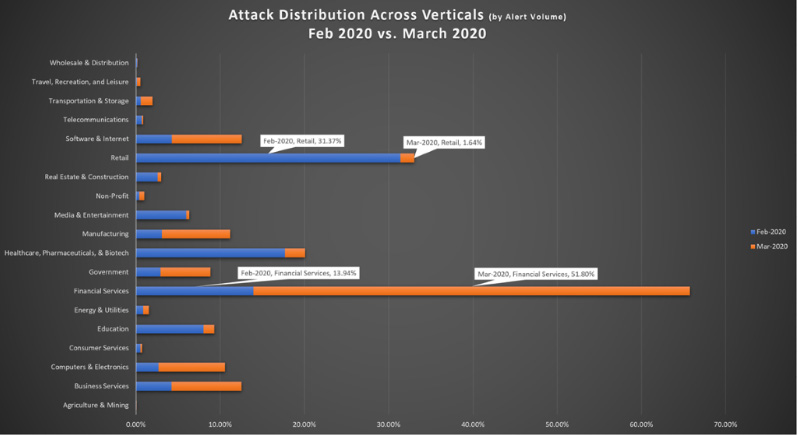
The finance sector has been increasingly targeted during the COVID-19 surge. Between February and March, we saw a 38% increase in cyberattacks against financial institutions. Of note, February shows that the retail sector led the majority of observed threats with just over 31%, but shrank to 1.6% in March, suggesting that as retail organizations shifted to remote business models, attacks actually went down and attackers shifted to target financial organizations.
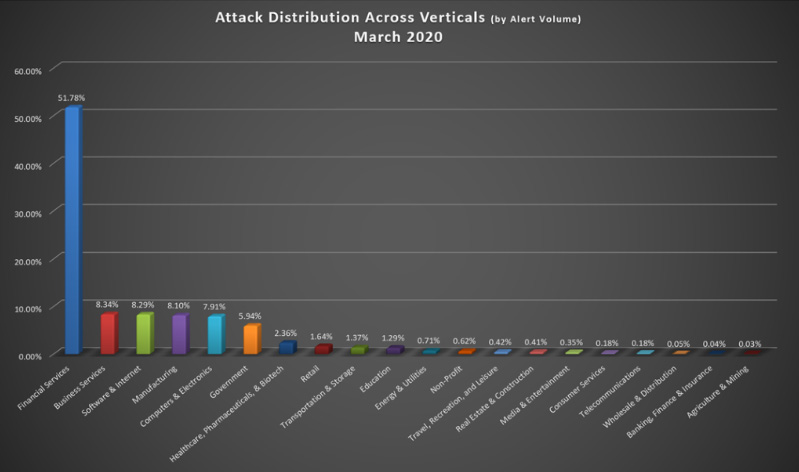
In March, financial-related attacks accounted for 52% of all attacks seen across the VMware Carbon Black dataset, an unprecedented anomaly in our data tracking. Healthcare, normally a top-three vertical for targeting, finished March as the seventh most frequently targeted industry, according to our findings.
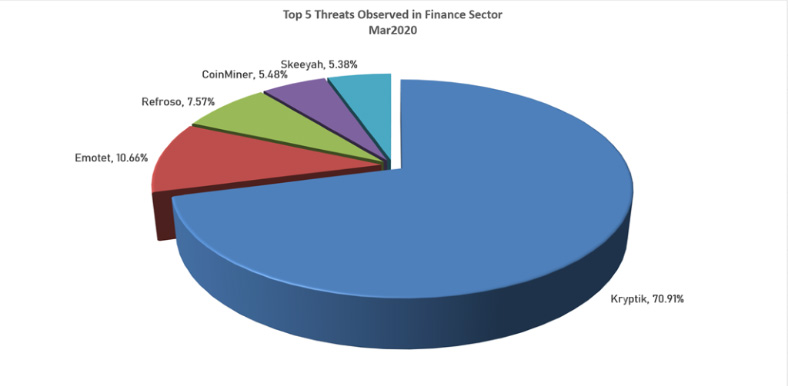
Targeting the Financial Sector
Of the 52% of attacks targeting the financial services sector in March 2020, 70.9% of those came from the Kryptik trojan, which attempts to target victim machines via nefarious installers. It then attempts to acquire admin rights to make registry modifications, allowing it to execute each time a Windows machine boots.
The Kryptik trojan can be very persistent and, without the appropriate visibility, can be difficult to detect as it often deletes its executable file after running.
As noted by a threat profile from the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC): “[The Kryptik trojan] queries the Windows registry for the .ini or .dat file paths. It also queries registry subkeys for the actual host, username, and password related to the specific FTP client application. Kryptik searches the registry, querying for both ftpIniName and InstallDir that hold the wcx_ftp.ini file. The trojan can recover many common FTP clients, email clients, file browsers, and file manager programs. Kryptik also can update itself and remotely download new versions.”
Kryptik was among the infections found in the notorious attack targeting the Ukrainian power grid in late 2015.
Conclusion
As the COVID-19 battle continues globally, it’s clear attackers will continue to target vulnerable populations and organizations. As the VMware Carbon Black Threat Analysis Unit (TAU) has found, attackers have been using COVID-19 to launch phishing attacks, fake apps/maps, trojans, backdoors, crypto miners, botnets and ransomware. Increased vigilance and visibility into enterprise-wide endpoint activity are more paramount than ever.
We believe comprehensive visibility starts with collecting and then analyzing key data that can uncover cyberattacker behaviors. Modern cybersecurity is all about keeping pace and staying ahead of attackers. And one of the only ways to do so is through comprehensive insights that can be derived from big data analytics. Without big data analytics, companies can only focus on finding and stopping known methods and attacks, which leaves them vulnerable to new and emerging attacks. Security teams must be able to predict and prevent not only known attacks, but future and unknown ones too. Innovative processes like big data analytics take advantage of all available data – unfiltered endpoint data, event streams, attackers’ tactics and techniques, global threat intelligence, and more – to provide the most comprehensive protection possible. With the power of big data analytics, security teams can uncover the most disruptive and damaging hidden tactics, identify root causes, and stop malicious threats before they are fully developed.
For a complete look at VMware Carbon Black COVID-19 cybersecurity resources, click here.
The post Amid COVID-19, Global Orgs See a 148% Spike in Ransomware Attacks; Finance Industry Heavily Targeted appeared first on VMware Carbon Black.