Hackers Are Using Corona Virus Fear Factor to Steal Your Money

If you are thinking;
how low can scammers go, the answer is; very low. Individuals, and even large
corporations, are currently massively targeted by fraudsters that capitalize on
the unprecedented situation around the Coronavirus outbreak, which generated
brand-new opportunities for them. Criminals exploit the fear and trust of users
worldwide to trick them to hand over their sensitive data. Inboxes are flooded
with fear-mongering e-mails linking to fake sites, which are asking for
credentials, or with malware, hiding as a useful instruction manual, or
application that is advising on how to protect from the virus. These are
designed with only one purpose, which is to steal your sensitive data. This
article should bring you up to speed regarding the attacks, which ThreatMark’s
team has seen so far.
Before we start with our list, please note that the majority of attacks mentioned below start with phishing. The rules on how to detect phishing sites are quite simple, and we had already written about them. If you keep those security measures, you will be safe from this kind of attack.
BlackWater and Emotet Malware
A new backdoor malware named BlackWater has begun to spread, pretending to be COVID-19 related information. Phishing e-mails are carriers of the malicious executable file called “Important – COVID-19.docx.exe” that uses the Word icon. Unfortunately, since Windows hides file extensions by default, the user is tricked into thinking this is a valid Word document. This trick has been used many times before and it seems that it is still working quite well.
If opened, the first thing that malware does is extracting the Word document to the computer and opening it. The content of this document consists of information about the COVID-19 virus, which works like a decoy for malware, as it installs malicious payload to the computer. By the time that the victim is reading instructions, malware extracts the file sqltuner.exe and starts using it for calling for commands from the C&C center through CloudFlare service, which makes it harder for investigators to block it. Even though is it not completely clear what BlackWater does exactly, without any doubt, it represents a new generation of malware.
Similar to the BlackWater, another infamous malware called Emotet has been spread in Japan through malicious e-mail attachments feigning to be sent by a Japanese disability welfare service provider, reporting on where the infection is spreading. The e-mail contains a document that attempts to download the Emotet malware onto the victim’s computer.
Targeted Attacks
Coronavirus
outbreak themed attacks have also been targeting specific institutions by using
specially crafted RTF documents. These had been sent to members of the
Mongolian public sector, allegedly containing information from the country’s
Ministry of Foreign Affairs.
Such a list of functionalities can be easily misused for circumventing the authentication element in the banking application. A detailed analysis of this attack can be found here. In short, RTF files were weaponized by a tool called RoyalRoad, which embeds objects exploiting several vulnerabilities of Microsoft Word that allows the attacker to:
- Take screenshots
- List files and directories
- Create and delete directories
- Move and delete files
- Download files
- Execute new process
- Generate a list of all services

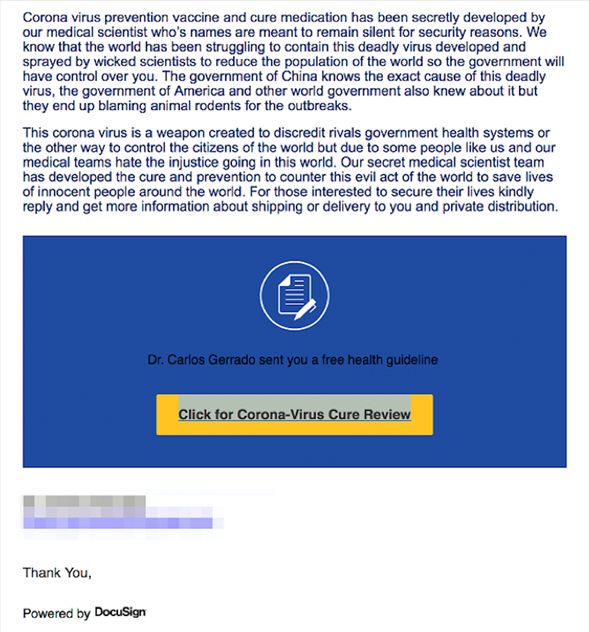
Cures Not Released to The General Public
A perfect example of two elements that work together very well is fear and secrecy. The following e-mail claims that a cure for the virus has been developed in secrecy to lure users into viewing an attached health report. After clicking on the link, users are prompted to enter their credentials, which are subsequently stolen by the attacker. If you think that not many users have been tricked, think again.
As
expected, while quarantine and home offices last, the Internet will be the
primary (and the only possible) channel of work/study for many. With this
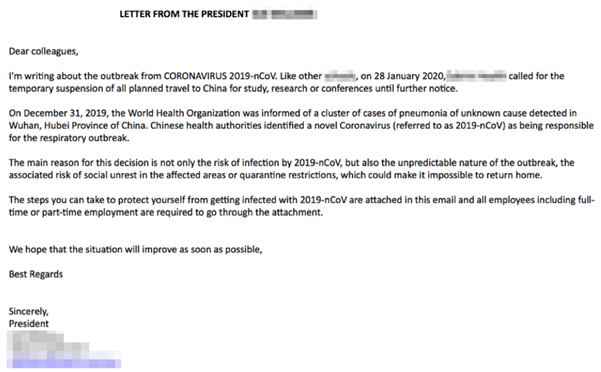
context, it seems logical that the company’s directors are reporting scam
e-mails as well. Based
on the research by the CNBC Technology Executive
Council, more than 36% of executives stated that cyberthreats have increased since
the majority of their employees have been working from home.
Below is an example of a well-crafted e-mail message luring receivers into opening the attached Word document. The document contains a link to a fake Microsoft Office phishing website collecting company credentials.
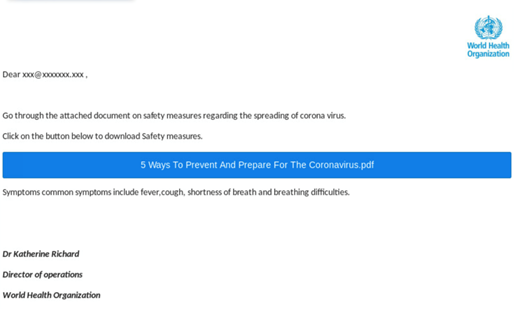
Impersonating the World Health Organization (WHO) and Center for Disease Control and Prevention (CDC)
Attackers use domain names similar to the ones used by the World Health Organization (WHO) – who.int – and the Center for Disease Control and Prevention (CDC) – cdc.gov to impersonate official bodies fighting the disease. These e-mails either contain an attachment or a direct link to the phishing website.
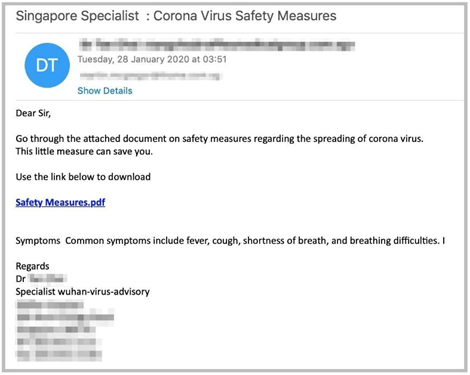
Another example of unsolicited health advice and safety measures:
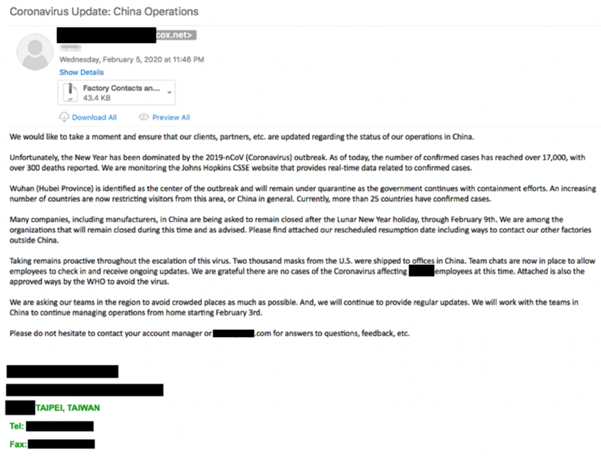
Updates regarding operations in China
Attackers have also been abusing facts about disrupted operations in China and its effects on supply chains worldwide. The example e-mail below contains a ZIP file, which in turn contains a remote access trojan, capable of giving the attacker full access to the victim’s computer.
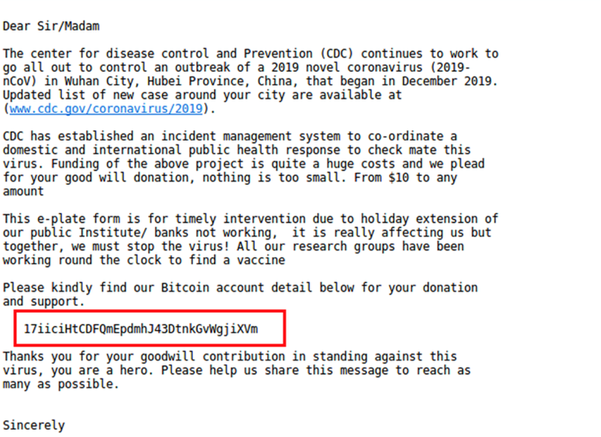
Charity Abuse
This e-mail
attempts to have the recipient transfer funds to help developing a vaccine or
cover other medical costs. One of the more obvious signs of this not being an
official campaign is the fact that the attacker asks for funds to be sent in
Bitcoin.
In case you would like to donate to the WHO to fight abuse, there is only one official place to do so – the COVID-19 Solidarity Response Fund available at the official website of the WHO.
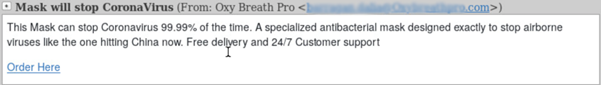
Sale of Facial Masks
The high demand for facial masks and respirators opened another attack vector – an offer for ordering facial masks that is made by attackers, which if clicked on, leads to a website asking the user for sensitive personal and financial information.
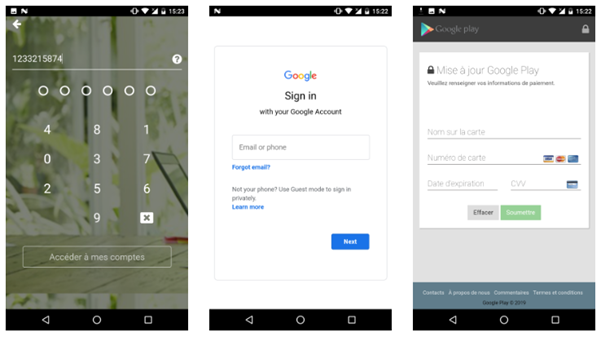
Mobile Devices Are Not Spared Either
The vector here is, once again, very straightforward. Attackers hide malware into a seemingly helpful application promising critical medical information (map of spreading, identifications of symptoms and so on) about the outbreak but delivering malicious content instead. Among many, there is Cerberus, hidden in the application “providing help with ways to get rid of Coronavirus”. What you get is malware, stealing your SMS, keylogging all your keystrokes and other features, jeopardizing your sensitive data and money.
Phishing attempts and scams are occurring in light of COVID-19 outbreak will be with us for a while. The same goes for remote work of your employees & them accessing the company’s infrastructure from their homes. If you care about not being breached, teach your staff how to recognize phishing e-mails and fraudulent applications. If your company has an online service accessible by your clients where clients are connecting to, consider our AFS solution. You would be able to monitor and identify users that visited a phishing site before or if their devices are infected by a malware. These two barriers, together with a verification of a user’s identity using behavioral biometrics markers, make your system impossible to penetrate.
The post Hackers Are Using Corona Virus Fear Factor to Steal Your Money appeared first on ThreatMark.

