Partner Perspectives: Maintaining Order in Chaotic Times

Erkang Zheng is the CISO of LifeOmic and the General Manager of JupiterOne.
One of the key challenges facing growing cloud-native organizations is the ability to maintain your security and compliance posture despite your employees’ access to critical data from numerous locations and devices. This ‘chaos’ is increasing as more organizations adopt bring-your-own-device (BYOD) policies and as teams are becoming increasingly distributed both across borders and with more employees working from home. There are no signs of these trends slowing down.
It has been said ‘chaos is a ladder,’ and would-be malicious attackers see your scattered, constantly changing digital environment very much the same way as the once throne-bound Lord Baelish. Your organization’s ability to scale as a business is dependent on your ability to ensure your security posture remains intact amidst the chaos.
For cloud-native organizations, that means not only protecting your endpoints, but understanding the complete blast radius each endpoint (should it be breached) would incur. To do that, organizations need to map these endpoints and their relationships to the critical resources, assets, code repositories and other data in the cloud to which they have access.
Integrating JupiterOne and CB Defense
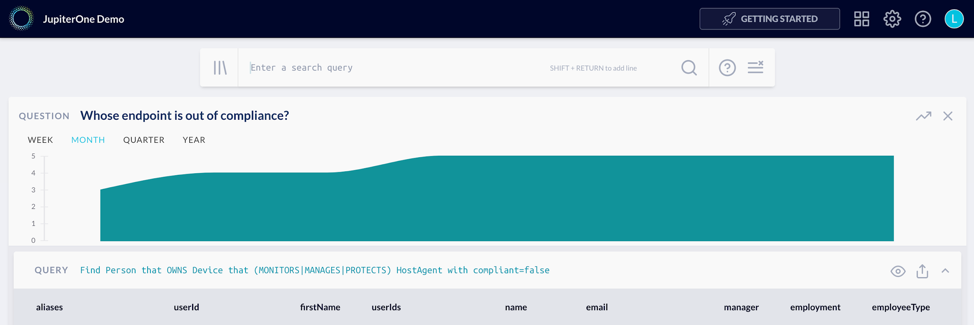
JupiterOne’s managed integration with CB Defense allows security teams to ask simple questions that return robust insights to quickly spot vulnerabilities.
For example, a security analyst can easily analyze how many endpoints are out of compliance, who the individuals are (including their employment status), and how that has changed over time.
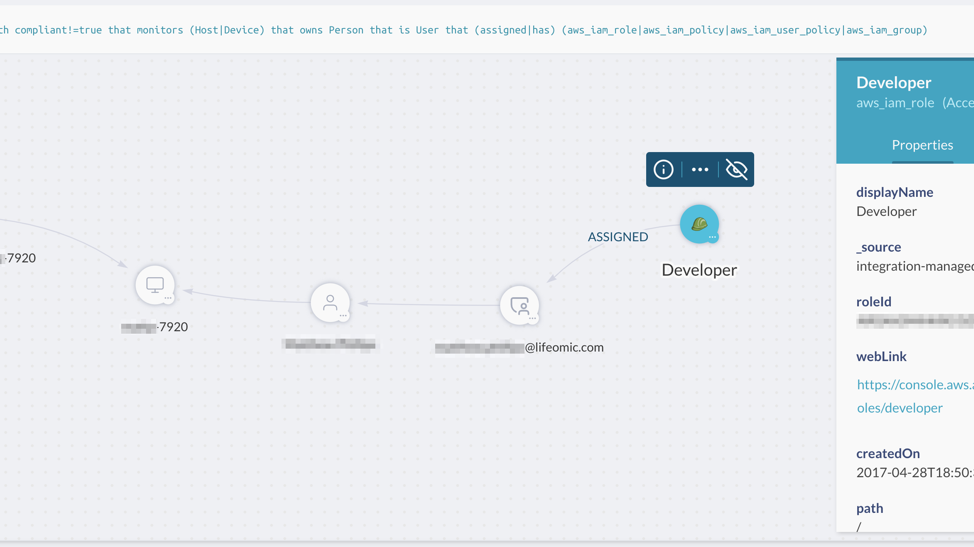
After you’ve identified those users, you can easily drill down to the resources that the user can access. If you wanted to see which of the non-compliant users has AWS access, that is simple:
Keeping Up with the Complexity
JupiterOne’s centralized security operations and compliance platform integrates directly with an organization’s Endpoint Detection and Response (EDR) solution, such as CB Defense, as well as their cloud environment, code repositories, identity and access providers, code scanners, vulnerability detection solutions and ticketing providers to create a complete map of your digital environment. This includes collecting the specific up-to-date details around configuration, access, etcs, and all the relationships therein – all kept up to date automatically through API-based integrations and analysis.
The mapping (which occurs on a graph database) doesn’t stop there. JupiterOne also connects these resources to an organization’s security policies, procedures, frameworks and compliance requirements. It’s automated governance powered by data and context.
This graph of an organization’s digital environment provides a complete view of their security and compliance operations in a single location. Leveraging this graph makes it easy to search for potential issues, create rules for monitoring vulnerabilities and risks, as well as produce evidence for attaining and maintaining compliance. The context that comes from connecting the data in CB Defense and your other cloud resources in JupiterOne makes it easy to cut through the chaos and hone in on what needs your attention.
By leveraging the integration between CB Defense and JupiterOne, security teams in growing cloud-native organizations can overcome the chaos and unlock scale.
To learn more about the integration between JupiterOne and CB Defense, check out JupiterOne’s page on the Carbon Black Partner Locator.
The post Partner Perspectives: Maintaining Order in Chaotic Times appeared first on Carbon Black.