Network Packet Broker Rules and Configurations

The Port Mirroring or SPAN (Switched Port Analyzer) method of monitoring network traffic has been the perennial focus of network visibility. With port mirroring enabled, the switch sends a copy of all network packets seen on one port (or an entire VLAN) to another port, where the packet can be analyzed. As a SPAN port is unidirectional and network traffic is bidirectional, the aggregate traffic could be twice as much as the SPAN port connection. Also, in times of congestion, the switch may not be able to mirror 100% of the network traffic to the SPAN Port. In both cases the result of using SPAN ports for network monitoring applications is unacceptable because some packets may not make it to the monitoring appliance.
As enterprise networks assumed mission-critical importance and consequently network architectures became more complex, the shortcomings of using SPAN ports for network monitoring have become more apparent.
Specifically, network bandwidths have continued to see exponential growth while networks have been facing a range of unique security threats such as Distributed Denial of Service (DDos), malware and encrypted attacks that demand detection and remediation in real-time. As a result, networks commonly deploy a range of specialized monitoring, security, and performance management tools requiring a pervasive visibility strategy enabled by Network Packet Brokers (NPBs) vis-à-vis limited SPAN only-based approaches.
Network Packet Broker (NPB) Overview
NPBs are devices that receive network traffic (such as input from multiple SPAN ports) and can manipulate that traffic before breaking it down into streams of related data and transmitting that data to their respective monitoring, performance management, and security tools. In a considerably short time and due to several highly important benefits, Network Packet Brokers have become the go-to device for enterprises to improve their network visibility and network security.
- Efficient and flexible traffic filtering. The NPB filters and routes network traffic to network security and monitoring tools as appropriate. This critical functionality provided by NPBs ensures the efficiency, reliability, and effectiveness of each of the in-place monitoring tools.
- Data Deduplication. During the deep packet inspection process, the NPB removes all such packets that contain redundant data, which is crucial for preventing monitoring tools from being overloaded.
- Packet Optimization. NPBs optimize packet traffic in several additional ways such as conditional packet slicing and time stamping enabling security and monitoring tools to function more efficiently and effectively.
- Enhanced Network Fault Tolerance. Network Packet Brokers support fault tolerance or the ability to minimize any unplanned downtime caused by events such as power failures, failure of associated network tools or of the NPB itself enhancing the availability and security of enterprise network.
- Load-balancing for Enhanced Security. NPBs provide load-balancing or forwarding of traffic on a policy basis to associated network monitoring and security tools for improved effectiveness of such tools.
NPBs typically intercept traffic at key network locations such as Internet ingress and egress points in enterprise data centers, network carrier boundaries and core/aggregation and access switching/routing links and forward such traffic to network security and monitoring devices such as Network Intrusion Detection, Network Intrusion Prevention, Network Performance Analysis and troubleshooting equipment.
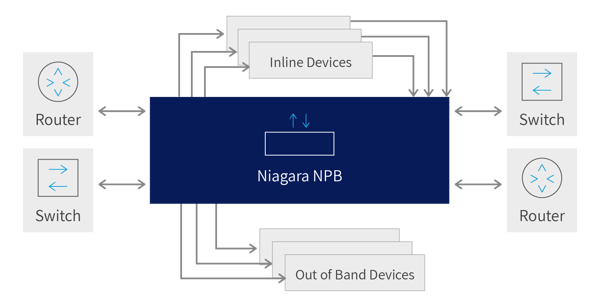
Figure 1. Typical monitoring points where Network Packet Brokers are used
NPBs typically support a range of flexible traffic forwarding rules based on a variety of characteristics such as OSI layer 2-3 packet fields (MAC address range, IP address range, protocol and port, etc.) including packets encapsulated within MPLS labels and tunneling protocols such as GRE and PPTP.
Advanced network packet broker functionalities include the ability to inspect encrypted traffic, identify and remove duplicate packets before forwarding them to tools and generate flow summaries for consumption by network tools.
The flexibility of a rule-based approach to directing traffic between network links and traffic analysis or security tools is what permits network administrators and security specialists to respond quickly and proactively to any kind of network event. Administrators can define and refine rules in seconds in order to observe traffic at any point in the network, eliminating the need to change physical wiring.
Because NPB’s are often tasked with monitoring extremely high-speed data links (and can also aggregate data originating at multiple slower links into a single fast stream), they provide the ability to load balance traffic across multiple similarly configured tools. Load balancing permits a group of tools to process a workload larger than any single instance of the tool would be capable of. When necessary, load balancing can be configured to maintain session state so that network flows between two endpoints are always directed to the same tool instance.
NPB Configuration Rules
Network packet brokers can be configured to run traffic through a chain of network tool devices, including load balanced clusters of devices, permitting in-depth analysis of network traffic for security threats, logging or performance analysis. Network tools are generally deployed in one of two configurations: out-of-band and inline.
Passive tools, such as network monitoring and performance analysis systems, are out-of-band devices. Out-of-band devices receive a copy of the data selected using NPB rules for inspection, and the traffic is not returned to the network following analysis.
Devices that must inspect or manipulate the data before it continues through the network are inline devices. These devices may return the data (modified or not) to the network or, based upon their own configuration, may elect to drop certain frames. DDoS prevention devices are one example of in-band tools. Traffic that is identified as part of a potential DDoS attack are dropped and other types of packets are returned to the network for delivery to their ultimate destination.
Network Packet Broker configuration rules are based upon two fundamental concepts. The first are “filters” while the second are “configuration maps”. Filters determine which packets are recognized as being significant by the NPB. When a filter’s definition matches a packet in the Packet Broker, this is triggers additional processing on the packet by the NPB. Configuration maps define a set of input and output ports on the front panel of the NPB and determine which filters will be applied to traffic traversing those ports.
A basic example of filters and configuration maps is a rule which accepts network traffic on a single input panel port, applies the “pass all” filter and forwards matching traffic (which in this case would be every packet) to a specific output port. Visually, this configuration would look like this:
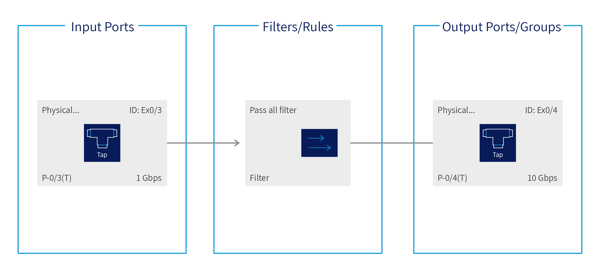
Figure 2. Visual Representation of a “pass-all” filter
A more complex example, shown below, includes configuration maps with multiple input ports (i.e. aggregation), multiple output ports (i.e. regeneration or duplicating the matched packets) and filters that match specific packet characteristics.
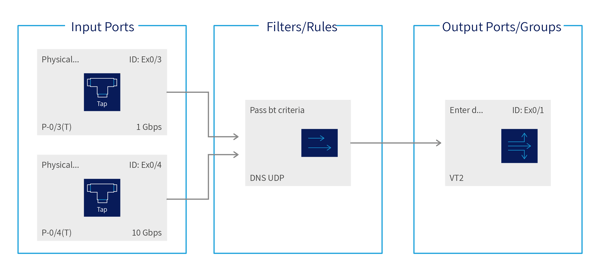
Figure 3. Passing all UDP traffic from a pair of input ports to a port group
The NPB user interface provides shortcuts for defining common filters based on L2-L4 attributes, such as MAC address, IP address, Protocol and Port. User-defined filters are also supported.
Besides user-defined filters, NPBs typically offer a range of predefined filters corresponding to the most often deployed end-user configurations. These filters can include:
- Network Layer 2 fields: Source and Destination MAC address
- IPv4 Network Layer 3 fields: IPv4 address, Network protocol number, Fragmentation information, etc.
- IPv6 Network Layer 3 fields: IPv6 address, flow label, traffic class
- Network Layer 4 fields: TCP or UDP source or destination port, TCP flags (useful when the network tool only wants to see session setup/teardown)
In summary, filters provide the NPB’s ability to only deliver packets of potential interest to network tools while withholding packets that would not contribute to the tool’s ability to do its job. Filtering unnecessary traffic allows tools to analyze networks carrying more traffic than they are capable of processing and improves the efficiency with which these tools operate.
NPB Configuration Use Cases
Rule and configuration capabilities enable NPB systems to flexibly and seamlessly deliver key benefits for security, performance management and network monitoring. This section focuses on how NPB configuration plays a critical role in enabling load-balancing and resiliency capabilities for associated in-line security services.
Load-Balancing
It is imperative that NPBs distribute traffic across associated security tools in a manner that is proportional to each security tool’s capabilities. If there is a mismatch between the traffic distribution and the processing capacity of each tool, some tools may become overloaded while resources lay idle on other tools. Thus, the overall performance of toolset will be impacted. On the other hand, if traffic is evenly distributed across tools with very dissimilar capabilities, the least performing tool will determine the performance limit for the toolset.
NPBs typically offer multiple load balancing configuration options, each with its own use case. For example, load balancing based on MAC addresses may outperform balancing based on TCP/IP connection 5-tuple, but the former is more likely to cause uneven traffic distribution across security tools. An example implementation may use a load balancing policy based on source/destination IP addresses and ports but the optimal load balancing policy for a deployment will depend on the security tools performance capabilities as well as the typical traffic levels for the network.
Network Bypass
NPB configuration also enables network bypass capabilities for high availability of associated security service. This enables security tool software upgrades to be completed without network downtime as well as fast failover recovery in the event of security tool failure. NPBs can be configured to support an adequate number of specific types of security tools and bypass thresholds so that a tool failure or offline maintenance period will not cause disruption to specific network security functionality.
The NPB monitors security tool availability and health by sending a heartbeat packet at designated intervals. If a certain number of these packets are not returned to the NPB within the timeout period, the NPB will consider the security tool (or toolset) as unresponsive and activate the bypass function.
For example, the NPB can be configured to transmit Ethernet heartbeat packets every 250ms. In the event of a single tool engine failure, traffic is redistributed across similar available tools engines. If more than one tool fails, traffic will bypass the entire engine group. The NPB can also be configured to fail open in the case of a power failure.
Conclusion
Due to the mission-critical availability and complexity requirements of enterprise networks, the benefit of using a pervasive visibility strategy enabled Network Packet Brokers (NPBs) vis-à-vis limited SPAN only-based approaches have become apparent. In a relatively short time frame, NPBs have become the preferred solution for enterprises to improve their network visibility and network security due to a range of benefits including flexible traffic filtering, data deduplication, enhanced network availability, packet optimization, and load-balancing.
NPBs capture traffic at vital network locations and transmit the traffic to network security and monitoring tools based on modifiable configuration rules using a range of packet properties. Innovative NPB features include the capability to analyze encrypted traffic, detect and eliminate duplicate packets prior to forwarding and produce traffic flow synopses for utilization by network tools.
Network tools are typically coupled to NPBs in either inline or out-of-band deployment scenarios. Passive tools, such as network monitoring and performance analysis systems, are out-of-band devices which are simply forwarded traffic using NPB rules for inspection, while the traffic is not returned to the network after analysis. Inline devices, on the other hand, may either return the data to the network or, using internal rules, may choose to discard specific packets. DDOS prevention devices and next-generation firewalls are examples of in-band tools.
Network Packet Broker configuration rules are based upon two essential capabilities: “filters” and “configuration maps”. Filters govern which packets are identified as being important and necessitate added handling by the NPB. Configuration maps describe a collection of input and output ports of the NPB and govern which filters will be employed to traffic utilizing those ports.
The combination of filters and configuration maps enable the NPB’s capability to filtering superfluous traffic allowing network tools to analyze additional traffic than they are capable of processing and improving the effectiveness of such tools.
Among use cases, NPB configuration performs an important part in enabling load-balancing and resiliency capabilities for coupled in-line security services. NPBs typically offer multiple load balancing configuration options, for example, load balancing based on MAC addresses may outperform balancing based on TCP/IP connection 5-tuple, but the former is more likely to cause uneven traffic distribution across security tools. NPB configuration also enables network bypass capabilities for high availability of associated security service. This allows security tool software upgrades to be completed without network downtime as well as fast failover recovery in the event of security tool failure.

