Modular cryptojackers now deliver illicit cryptomining to cover multiple platforms at once

Cryptojacking attacks are not going away any time soon. Instead, they’re becoming more sophisticated – and more dangerous – by using advanced modular malware with worm capabilities as a delivery mechanism.
A complex backdoor, called Plurox, was recently discovered by MalwareHunterTeam. It has a pluggable architecture and is able to spread itself over a local network, with the help of the EternalBlue exploit, and start cryptominers downloaded from the command and control (C&C) server.
The modular technology was introduced in the nation-state-targeted cyberattacks such as APT (Advanced Persistent Threat). At every step of the cyber-kill chain (see the MITRE ATT&CK model), attackers push the new modules needed to go forward – elevating privileges, for example, to establish a foothold, perform lateral movement within a local network, hide traces, and so on. This agile approach to cyberattacks is very efficient and specific to controlled targeted attacks.
This particular version of backdoor can download a networking plugin. The UPnP module enables port forwarding on the router using the UPnP protocol for 135 (MS-RPC) and 445 (SMB) ports for the specified IP addresses. The UPnP plugin helps establish a hidden communication channel by forwarding ports on the router so the internal reconnaissance from an infected computer may look like a communication initiated by the router.
The SMB plugin spreads the infection locally via the NSA’s EternalBlue code exploit of the CVE-2017-0144 vulnerability in SMB v.1 protocol.
Finally, Plurox installs a specific variant of cryptomining malware that fits the target computer architecture – enabling the main purpose of the backdoor: cryptojacking.
What you should know about the Plurox backdoor.
- Plurox employs network worm capabilities to propagate in a local network using the EternalBlue exploit.
- The TCP protocol facilitates communication with the C&C server.
- The backdoor can download and run cryptominers, UPnP, and SMB network plugins.
- The SMB module runs the EternalBlue exploit to propagate in the local network.
Plurox can download different cryptominers suitable for the particular architecture in place.
Cryptominer plugins
The Plurox backdoor can download eight different cryptomining plugins for different architectures using different open source libraries for computing:
- auto_proc
- auto_cuda
- auto_miner
- auto_opencl_amd
- auto_gpu_intel
- auto_gpu_nvidia
- auto_gpu_cuda
- auto_gpu_amd
Let’s take a closer look at some of them.
Miner auto_miner{32,64}.exe
auto_miner.exe is an XMRig cryptominer built on the MinGW POSIX WinThreads for Windows library source code:
SHA256: be653e4f2b5923dc633fdfa2df8fc99cd2cdc4d3b4d47cf89ce3dfcd88ea4176
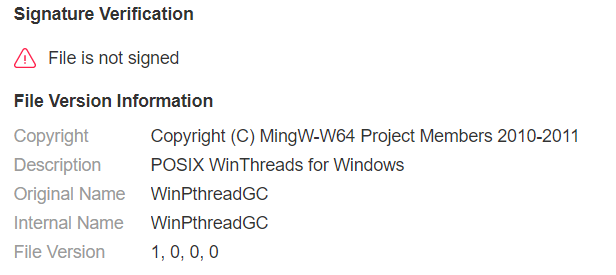
The cryptominer has embedded autoconfiguration and was supposed to be run as “svchost.exe”. However, once started, it doesn’t create a new process.
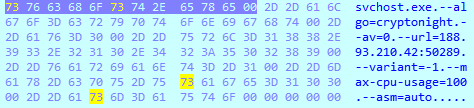
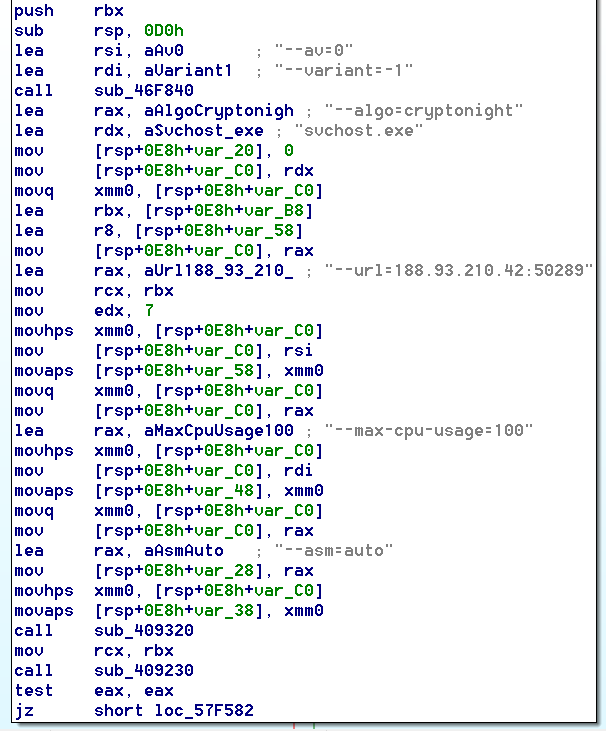
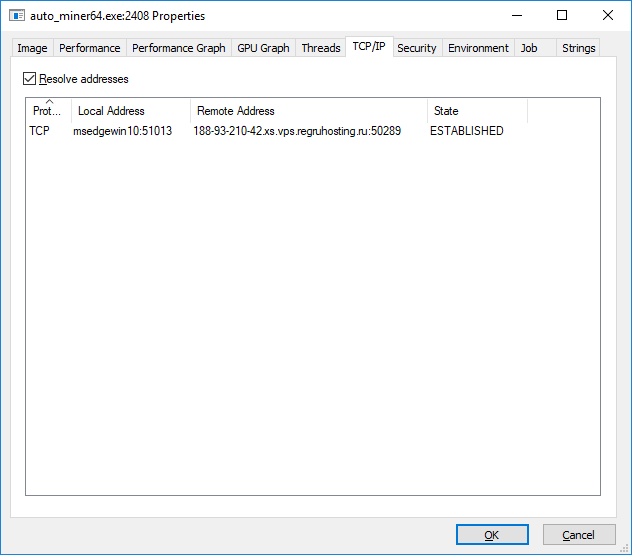
After launch, it creates multiple threads and sends a TCP connection request to the mining pool: ‘188.93.210.42:50289’ or ‘188-93-210-42.xs.vps.regruhosting.ru:50289’. The server is located in the Russian Federation.
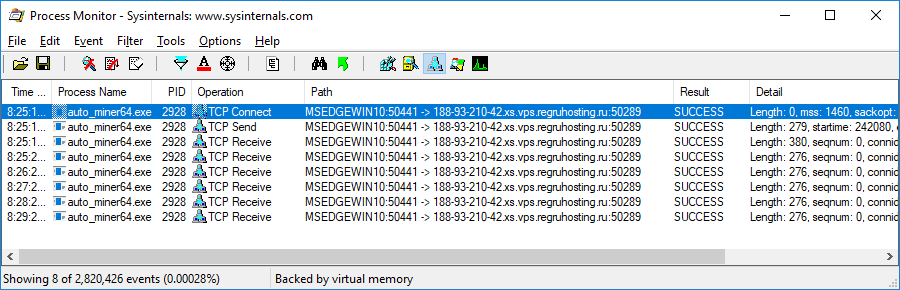
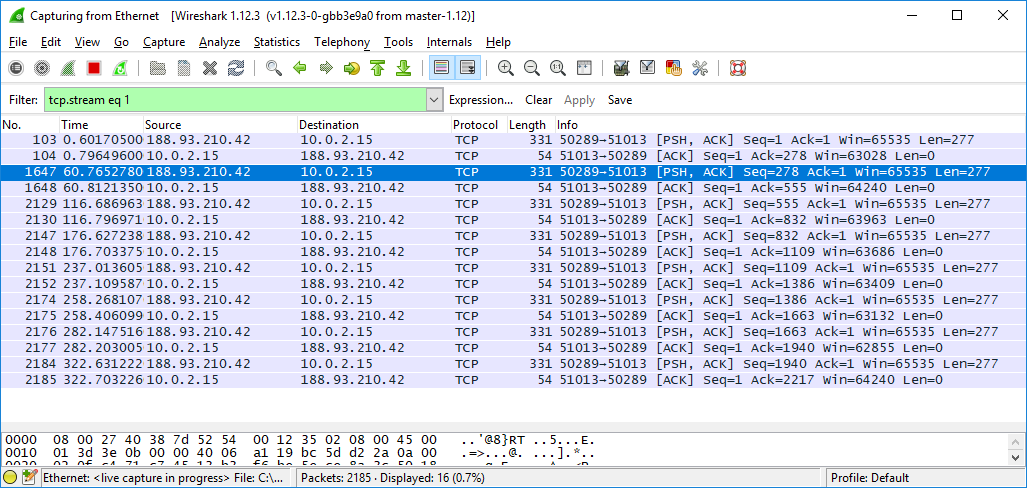
Examples of the JSON messages sent via the Stratum protocol:
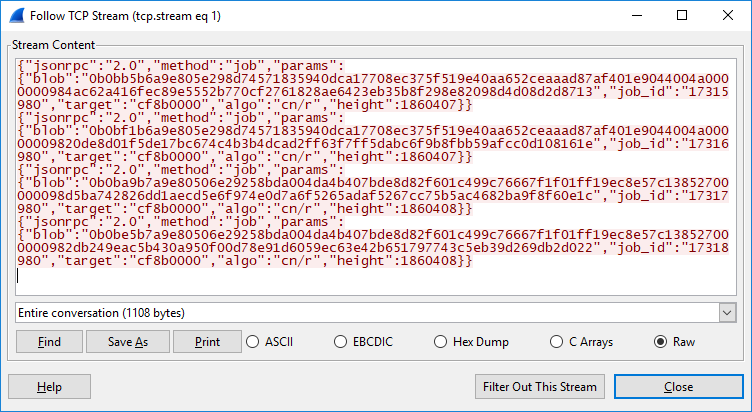
Based on the data received from the pool, the cryptominer works in the following mode:
- Algorithm: CryptoNightR (Monero’s variant 4).
- Protocol: Stratum
- Version: XMRig 2.14.1
CPU usage for cryptomining is unlimited (the limit is set to 100%).
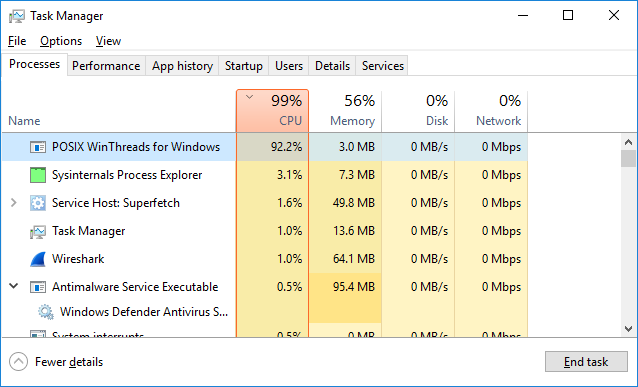
auto_miner32.exe – SHA256: 45799254deda2ee21e92a205f00f8e8fad29c40cf4603c5e47d1f2fd7c22f568
auto_miner64.exe – SHA256: be653e4f2b5923dc633fdfa2df8fc99cd2cdc4d3b4d47cf89ce3dfcd88ea4176
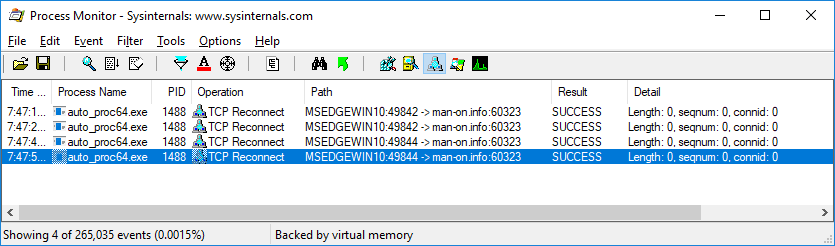
Miner auto_proc{32,64}.exe
This is the same miner, but with a different mining pool address: 89.108.99.143:60323 or man-on.info:60323. The mining pool (proxy) was not responding at the time this report was written. The physical location is in the Russian Federation.
auto_proc_32.exe – SHA256: 6fed231759406d4492f8a124130e25580833206a965f722ff85b10d369991143
auto_proc_64.exe – SHA256: 2f8f6896b326818e40c9383ce5d187ae7a75d713d4d82d5fb5937c3d8b66829b
auto_opencl_amd{32,64}.exe
auto_opencl_amd{32,64}.exe is an implementation of the parallel computing framework OpenCL for the AMD CPU architecture.
This miner autoconfiguration looks as follows:
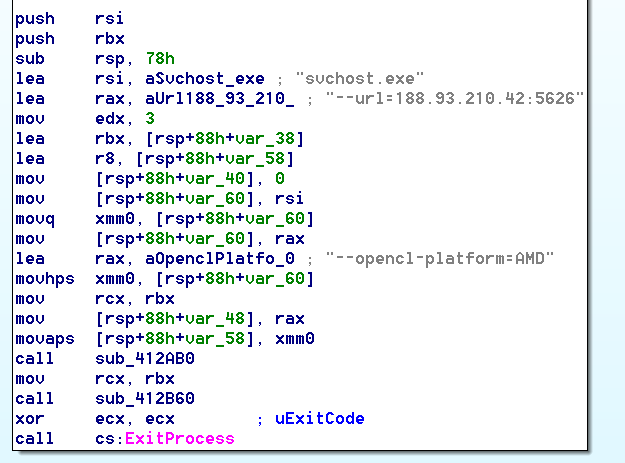
auto_opencl_amd32.exe SHA256: 47207d3881e9e26cfc8beee92d0a4a2d1f6309a10bfeb04a1a567ca66c7835eb
auto_opencl_amd64.exe SHA256: 09656ee499434f59e75333b5ab7e8220781d3a0c4623be71498214ab43dbaa5c
The rest of the miners (auto_gpu_intel, auto_gpu_nvidia, auto_gpu_cuda, and auto_gpu_amd) have the same functionality and mining pool addresses but are compiled for architectures with GPUs.
IoCs
188.93.210.42:50289
188-93-210-42.xs.vps.regruhosting.ru:50289
188.93.210.42:5626
188-93-210-42.xs.vps.regruhosting.ru:5626
89.108.99.143:60323
man-on.info:60323
Conclusion
The cyberattack through the Plurox backdoor shows that cryptojacking is still a highly profitable activity and that it’s worth it for attackers to invest their resources in the development of the sophisticated cyber kill chain that leverages network worm capabilities to deliver cryptominers. SMB and UPnP protocols extend the attack coverage and hijack more computing resources. Moreover, the variety of targeted computing platforms enable mining in heterogeneous environments.
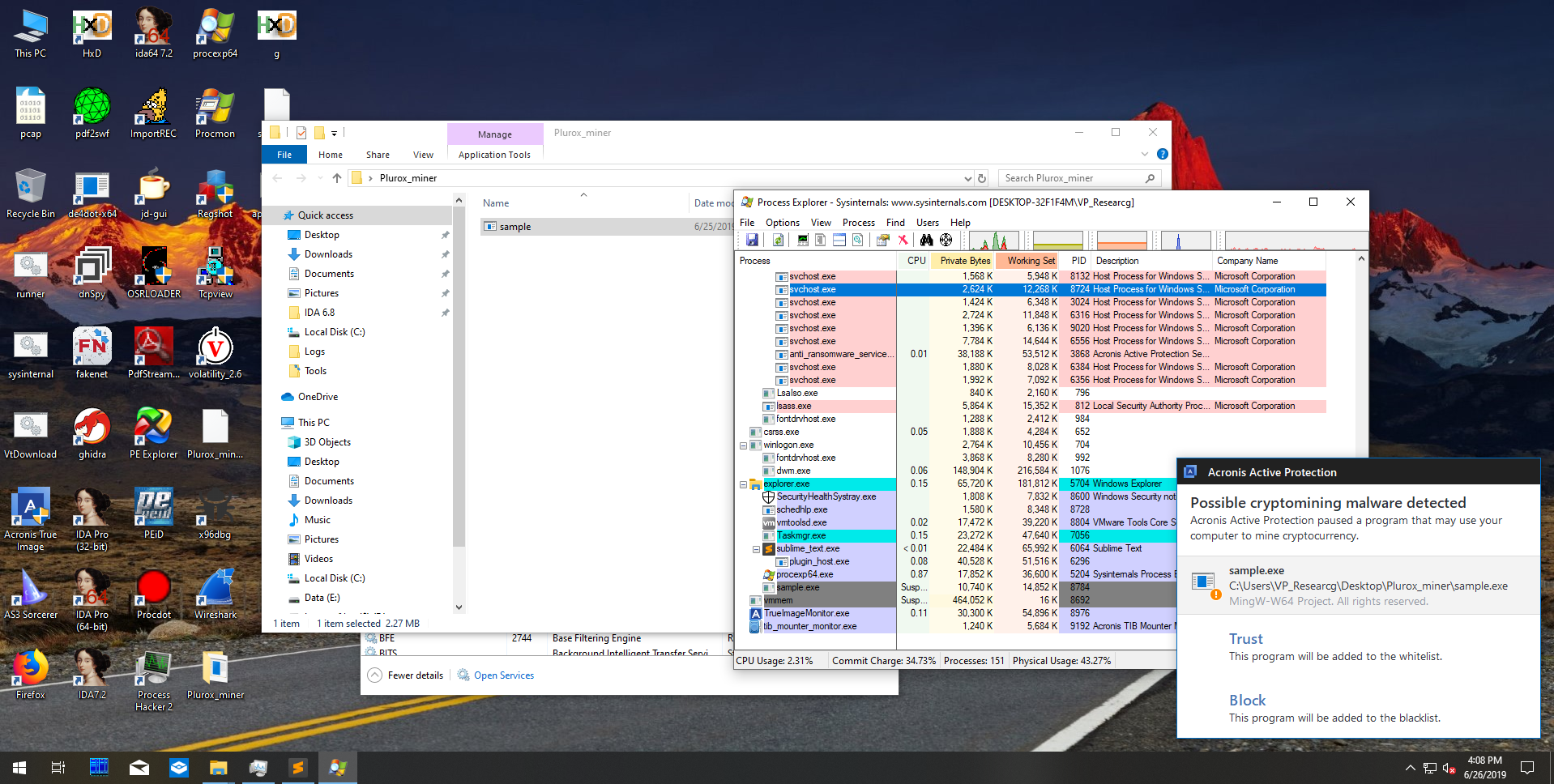
The good news is that Acronis Backup 12.5 successfully detects the cryptominers delivered by the Plurox backdoor. As a result, users of our solution are comprehensively protected.

