Making Use of Cyber Attribution Reports

Having recently read the Office of Director of National Intelligence’s (ODNI’s) “A Guide to Cyber Attribution,” I began to think of ways ThreatQ can help analysts use cyber attribution reports to improve their security operations.
ThreatQ can be a central repository for the intelligence reports analysts produce, allowing the information to link object types, be searched and act as a knowledge base for analysts and security teams. The platform also has the capability to export and share information to tools, data lakes and other teams or organizations if desired.
The ODNI’s report is a framework that enables attribution of an attack to a particular country or actor. The attribution indicators can be uploaded in ThreatQ and the key information pieces can be parsed and linked. This includes adding any of the object types related to the report, such as an attribute for the point of origin, the organization directing the activity or the confidence level of the information, as shown in Figure 1. These attributes can be used when searching the platform for related information or scoring to prioritize indicators.
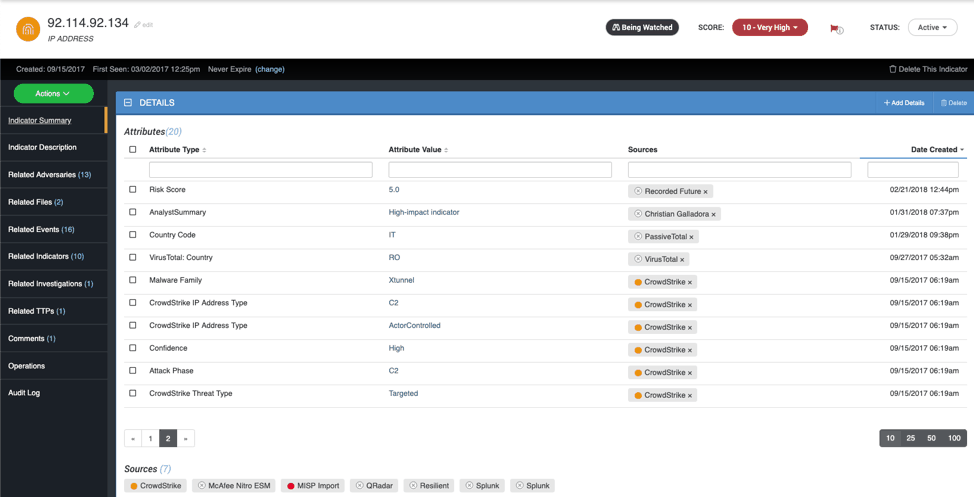
Figure 1 – Listed Attributes and Multiple Sources
The report lists the following indicators in determining attribution: tradecraft, infrastructure, malware, intent, along with indicators from external sources. Keep in mind, these indicators are not the same as Indicators of Compromise but indicators used to determine attribution.
Within ThreatQ’s Threat Library there are different categories we refer to as object types. These object types are primarily based on STIX 1.x and 2.x objects, but are not limited to this and new object types can be created to fit your organization’s needs. This is important because ThreatQ provides a location to store the tradecraft used such as the tactics, techniques and procedures (TTPs). This information can be linked to the report or to any of the other indicator types.
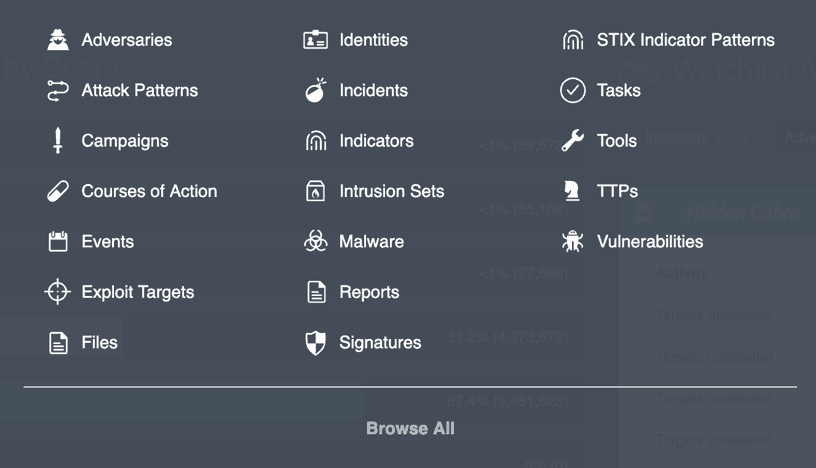
Figure 2 – Threat Library Object Type Examples
From the object types listed in Figure 2, the analyst can associate different infrastructure types to the report. As an example, adding a social media account to the Identities object type or a compromised server IP to the Indicators object type. The same can be applied to Malware. The indicator type of Intent could be applied to ThreatQ’s Campaigns object type if an analyst wanted to link intent outside of the report.
One of ThreatQ’s most notable features is the ability to deduplicate information within the platform. This is especially useful when bringing in information from external sources. Instead of having multiple records of, say, the server IP used earlier, it will list the IP once, but list multiple sources (see Figure 1). The attributes associated with the IP address will also list the source of the information.
ThreatQ in Action
Let’s take a look at an example of what the information contained within a report would look like in ThreatQ, using FireEye’s report “APT37 (REAPER) The Overlooked North Korean Actor”. A Report object is created and the context of the report is copied to ThreatQ. Looking at Figure 3, the next step is to add Attributes; this adds context that can be filtered or searched on. In the case of Indicators, a score can be applied to attributes to aid in prioritizing the Indicator. You can see that a Confidence Level has been applied to the report along with Intent as Attributes in Figure 3.
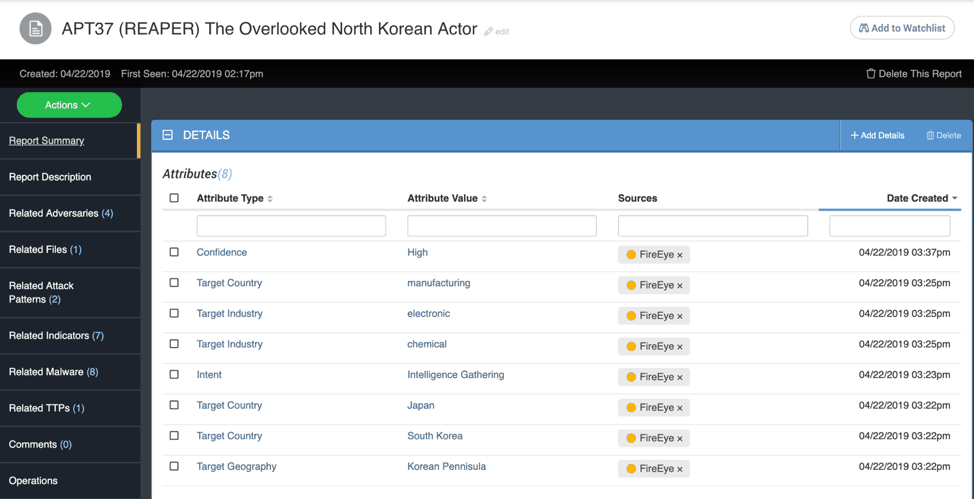
Figure 3 – APT37 Report
On the left of Figure 3 you can observe related objects to the report. Some of these include references to additional adversaries mentioned in the report, attack patterns used such as “spear phishing attachment,” related Indicators like CVEs and so on. Demonstrating how objects can be linked, when you click on a linked object, the FireEye report is also shown as a related object (see Figure 4).
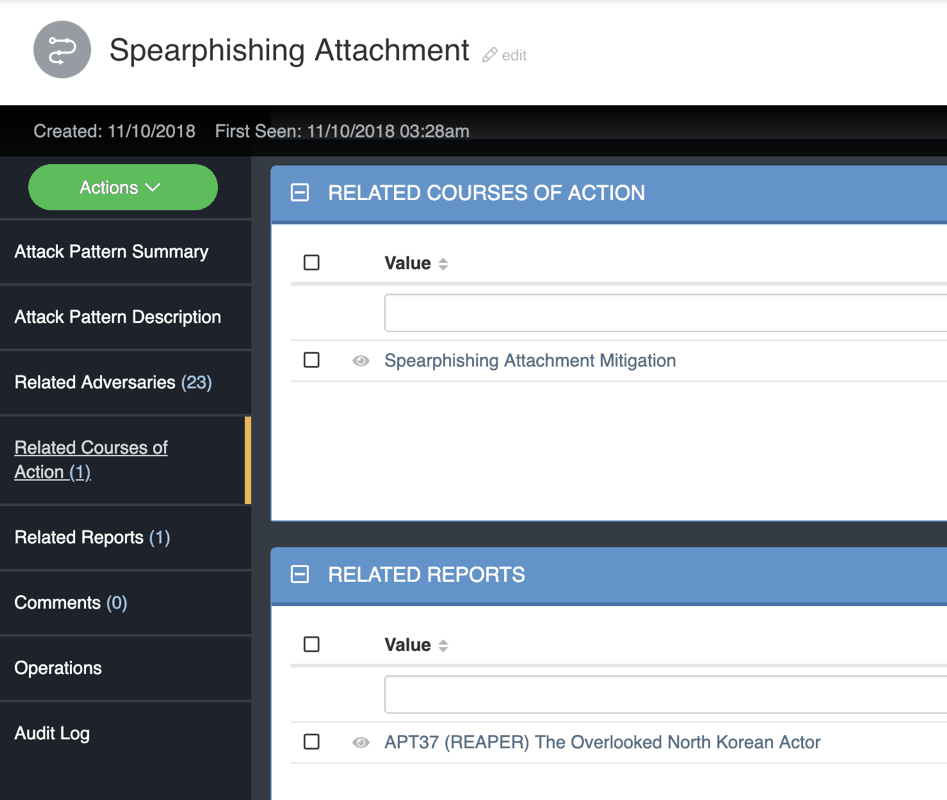
Figure 4 – Related Object
While ThreatQ is not a tool for determining attribution, it can be used to store the information from the tools and analytics the analysts used in making their determination. As these examples show, information in the ODNI’s report can be linked and searched for further research and analysis, making ThreatQ a very useful tool for retaining cyber attribution information and the history of that information.
The post Making Use of Cyber Attribution Reports appeared first on ThreatQuotient POSTED BY ROSS HAMMER

