The Zombie Phish Is Back with a Vengeance

Keep a close on your inboxes—the Zombie Phish is back and it’s hitting hard.
Last October, on the eve of Halloween, the CofenseTM Phishing Defense CenterTM reported on a new phishing threat dubbed the Zombie Phish. This phish spreads much like a traditional worm. Once a mailbox’s credentials have been compromised, the bot will reply to long-dead emails (hence, Zombie) in the inbox of the infected account, sending a generic phishing email intended to harvest more victims for the Zombie hoard.
We saw a massive surge in cases during the last quarter of 2018, which appeared to drop off in late December. The Zombie lay dormant for a few months, but now it’s rising up from the dead and has been infecting mailboxes at an alarming rate. In a recent five-day stretch alone, one of our PDC customers reported 146 separate Zombie Phish emails targeting its users.
Email Body: If we compare the message body to message body to the 2018 campaign, we see some similarities. The message body itself is simple HTML used to display a button. The button has an embedded URL which redirects the victim to the phishing page.
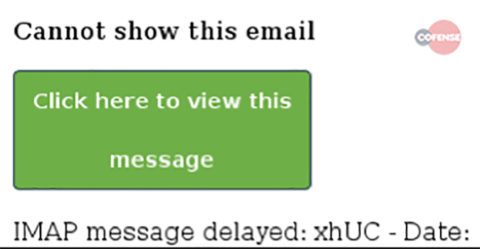 .
. 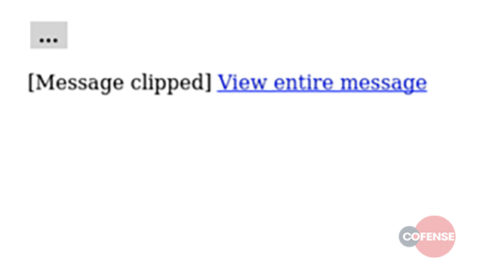
The image on the left is the message sent in the campaign of 2018 and the one on the right is the part of the new Zombie wave. As you can see, the more recent one has been simplified.
Message body in plain text: Viewing the message body in plain text we can see the true destination of the hyperlink.
<html> <body> <p><font color="#010101" size="3">This mail originated from outside our organisation - xxxxxx@uk.issworld.com</font></p> <table> <tbody> <tr> <td style="background-color: #d4d4d4;"><strong> ... </strong></td> </tr> </tbody> </table> <p>[Message clipped] <”hxxp://online[.]inboxvzo[.]host/bundoc/nonenforceable[.]php?thaddaus=">View entire message</a> </p> </body> </html>
Fig 2. Email Body in Plain Text
Below are some known URLs and domains which have been confirmed to be from the same zombie phish threat. Note how they all follow a similar pattern, using web mails-style words for the subdomains. This makes blocking the threat at the gateway difficult, since these appear to use automatically generated infection URLs to evade detection.
hxxp://online[.]inboxvzo[.]host/bundoc/nonenforceable[.]php?thaddaus=
hxxp://mobile-mail[.]readksh[.]host/compts/cainogenesis[.]asp?jerseys=
hxxp://web-client[.]serviceqtw[.]host/isomerization/shadowgraphic[.]asp?sunfall=
hxxp://reader[.]serviceykp[.]host/joya/gleg[.]asp?acct=
hxxp://mail-web[.]maildpk[.]host/identifiability/shieldless[.]php?houstonia=
hxxp://mail-web[.]mailbko[.]host/naughts/carnificial[.]asp?uniter=
hxxp://mail-message[.]mailwoe[.]host/stendal/squinty[.]html?dehortation=
hxxp://web03[.]mailfwj[.]host/cacomorphosis/unappreciably[.]php?trebleness=
Phishing Page: The phishing page itself has not changed since the last campaign. The victim is greeted with a simple “Hello” followed by his/her email address. The phish will also search the domain of the email address and append your company logo to add legitimacy to the page, tricking unsuspecting users into thinking they are logging into their enterprise webmail account.
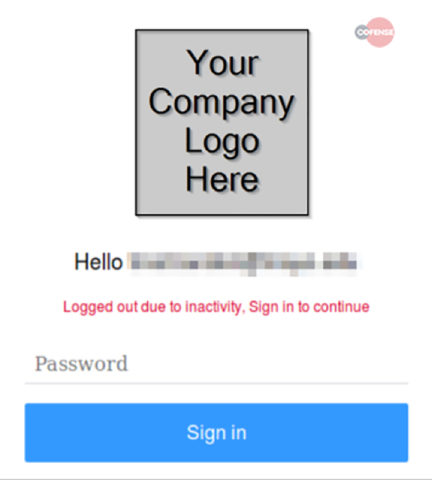
Fig 4. Phishing Page
Gateway Present: This email was found in an environment running Symantec Email Gateway (SEG)
Conclusion: The Zombie Phish was one of 2018’s breakout email threats. Read more about it in the just-released Cofense Phishing Threat and Malware Review 2019.
The post The Zombie Phish Is Back with a Vengeance appeared first on Cofense.

