Why Network Visibility is Critical for DDoS Mitigation by Niagara Networks

Distributed Denial of Services (DDoS) Overview
Denial of service is a form of cyber-attack in which attackers overload computing or network resources with so much traffic that legitimate users are prevented from accessing to online services such as online banking and e-commerce. Enterprise websites are a preferred target since they provide the most engagement with an organization’s customers, partners, subscribers and followers.
Attacks are called “distributed” when the attack traffic originates from multiple hosts. Historically, DDoS attacks originate from Internet-connected PCs that are compromised by malware. These PCs are called “bots” and are typically under the control of a Command-and-Control (C&C) server operated by the attacker or “Botmaster”
.png?width=525&name=Blog%20Why%20Network%20Visibility%20is%20Critical%20for%20DDoS_diagram-01%20(1).png)
The word “bot” (from robot) refers to automated software programs that perform specific tasks on a network of computers with some degree of autonomy. “Botnets” are a set of computers controlled by a C&C computer to execute commands as directed. Typically, computers become bots when attackers illicitly install malware that secretly connects the computer to a botnet; attackers then perform tasks such as sending spam, hosting or distributing malware, or attacking other computers.
The C&C computer can issue commands directly, often through Internet Relay Chat (IRC) or by using a decentralized mechanism, such as peer-to-peer (P2P) networking. Computers in a botnet are often called nodes or zombies. The DDoS attacks work in phases. In the first phase, the attacker compromises the weak machines in the network from around the world. In the second phase, a set of tools (also called malware) are installed on the compromised systems to attack the victims by controlling them from a C&C server.
DDoS Evolution
DDoS attacks have evolved significantly over the past 25 years, from manual efforts launched by groups of protestors to botnets made of connected devices to automated attacks exploiting vulnerabilities in server protocols. The attacks started on multi-user systems and then moved to servers. Later attack methods toyed with using workstations and home computers. More recently, attackers have settled on one of two techniques, using massive number of unsecured IoT devices to distribute an attack or amplifying and reflecting an attack using a vulnerable network protocol.
Initial accounts of DDoS attacks are mainly incidental. In the late 1990s, protest groupings started employing the Internet as a means of initiating simulated sit-ins to block entry to web sites as a method of opposition. Perhaps the first group to exercise this power was the Strano Network, a collection of likeminded people who worked to protest the French government’s nuclear policy. Rather than using a program to repeatedly connect to a Web site, the Strano Network asked participants to visit and repeatedly reload the targeted sites.
The first decade of the century marked the heyday of the computer worm. In 2009, approximately 50,000 computers affected with the MyDoom worm were used to target business, financial, and government web sites in the United States and government sites in South Korea. The attack caused little stoppage but prompted press and security firms to hold North Korea responsible for initiating the attack.
2016 saw DDoS attacks expanding to utilize IoT growth. In September and October of 2016, almost 50,000 IoT devices in 164 countries flooded targets with DDoS traffic up to 280 Gbps. This DDoS attack used mostly digital video cameras and recorders to send relatively sophisticated traffic to victims’ networks. The resulting attacks on the website of infrastructure service provider DynDNS topped 620 Gbps, according to Internet infrastructure firm Akamai.
Network Visibility for DDoS Protection/Detection
As discussed earlier, during the past several years, the nature of DDOS threats have evolved from being specific types of threats, for example, botnets, to a coordinated combination of threat types — e.g. distributed denial of service (DDoS) attacks followed by login hack attempts. In addition, the nature of the attack sources for DDoS, has also changed. The use of IoT devices, bring your own device (BYOD) and virtualization has led to less well-defined network perimeters and unclear network boundaries. As a result, the scale, severity and frequency of large DDoS attacks continue to grow unchecked.
Enterprise and service provider networks are complex. Ideally, a DDoS mitigation solution should have broad visibility of the overall network, using multiple inline detection appliances. A centralized controller would coordinate these inline devices, thereby allowing the security admins to detect attacks that are spread over multiple network edge devices. This distributed but centrally managed model provides a comprehensive understanding of all network traffic, which is required to detect attacks rapidly.
Enterprises and service providers are best served by DDoS alleviation solutions that offer advanced protection, a high level of performance, and rapid detection and mitigation times. Companies must also ensure that network infrastructure is not disabled during DDoS attacks—an especially challenging goal during the most colossal attacks. A solution that incorporates DPI-based techniques with application session awareness and traffic shaping enables the proactive creation and real-time enforcement of policies limiting traffic to critical network infrastructure elements. Protecting these devices from excessive traffic ensures that essential traffic is prioritized and flows uninterrupted.
Many enterprises deploy a network visibility fabric consisting of a network packet brokers to connect their traffic analysis tools with traffic data for DDoS protection/detection. A visibility fabric can also connect live traffic with inline security tools like next-generation firewalls (NGFW), web application firewalls (WAF), and intrusion prevention systems (IPS). Organizations deploy and use these network visibility fabrics to provides specific DDoS alleviation security tools with consistent access to traffic, but they also leverage the advanced traffic grooming and filtering features of network packet brokers to right-size data flows to individual tools.
![]()
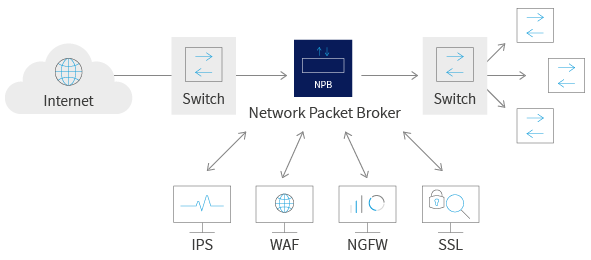
Niagara Networks for Pervasive Network Visibility
The rock-solid design of an enterprise or service provider network architecture enable the network and security teams to handle all DDoS attacks as they occur, by being able to clearly ‘see’ what is happening across the network always – and then take appropriate action. Such full visibility, usually referred to as Pervasive Network Visibility, is based on having the right set of DDoS mitigation tools and devices distributed across the network topology, continuously monitoring and inspecting the data traffic, collecting and analyzing data, and sending relevant notifications – as needed.
Niagara Networks offers a broad range of industry-leading network visibility solutions and tools include network taps, network packet brokers (NPBs), and bypass switches. These are designed to be placed in key network access points to empower the network’s own self-sustaining DDoS security mechanisms while being flexible and manageable enough to allow IT to step in immediately with the appropriate tools and features to handle all attack scenarios.
With the right solutions and tools – that are smarter, quicker, and more robust – set up correctly to ensure pervasive network visibility, the network security team will always be on top of all possible DDoS attack scenarios. This will ensure network security and stability while furthering the enterprise ROI.
If your enterprise values enduring DDoS mitigation, take the first step towards protecting your network by optimizing your network visibility. Schedule a consultation with a Niagara Networks visibility expert today to assist you.

