Attacking the internal network from the public Internet using a browser as a proxy

Though not a new attack, it is not very widely known outside of the security research community that a malicious JavaScript hosted on the public Internet can attack the internal network. Since a browser will by default have access to localhost as well as the local LAN, these public-to-private attacks can bypass not only the corporate/consumer perimeter firewall, but also the local host-based firewall.
Motivation for the research
Of the little bit of documentation that exists on attacks against the internal network, most resources describe it in terms of inter-protocol exploitation (attacking non-HTTP via HTTP), whereas our focus is on intra-protocol exploitation (attacking HTTP via HTTP). We are not aware of any one-stop resource describing these attacks from an intra-protocol perspective, and gathering these techniques in a whitepaper is our attempt to fill a void regarding documentation of these attacks, as well as to bring attention to an underrated attack surface.
Malicious actors are aware of these attacks, but defenders need to be informed as well.
Attack overview
Even in the face of Same-origin Policy (SOP), we can discover internal hosts, do limited port scanning, and do service fingerprinting. We will even show an example of compromising a vulnerable internal service despite SOP!
Internal service fingerprinting from the public Internet may look like this:
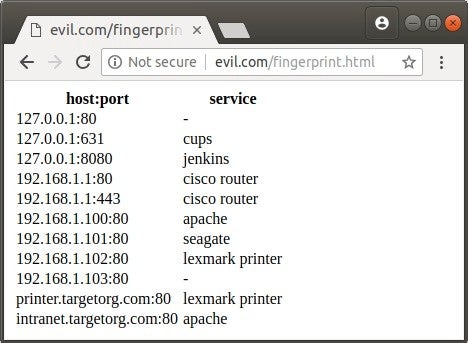
We will also show an edge case of actually surfing the internal network from the outside.
Protection
For the average end-user, there is no silver bullet for complete protection, but there are still many small things you can do to decrease your attack surface. In our whitepaper we will discuss means of protection, directed at different target audiences. Additionally, we will discuss means of detecting these attacks from a network traffic analysis perspective.
Browser vendors should consider disallowing connections crossing the public/private IP boundary by default, in the direction from public to private.

