Anatomy of an insider breach originating from a contractor’s laptop

Written by: Keith Siepel, IT Manager at Hydrotech, Inc. (Guest Contributor for Darktrace)
On the morning of Thursday, February 14, 2019 at 7:51 a.m. EST, a contract instructor turned on their computer as they had every morning that week to prepare for their upcoming class. They connected their laptop to our WiFi network, just as they had each morning, and proceeded to check email.
Unfortunately, this morning was a little different, as while they were checking email, their computer was checking other things on our network:
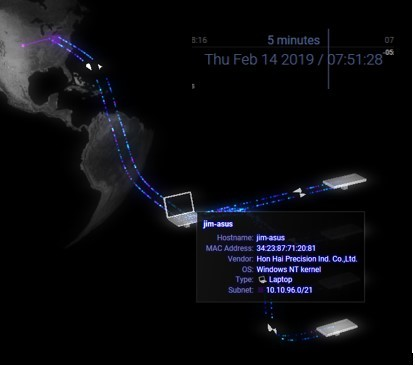
18 seconds later…

Our Darktrace system notified us via email of a potential problem and by marking the device in yellow on their Threat Visualizer.
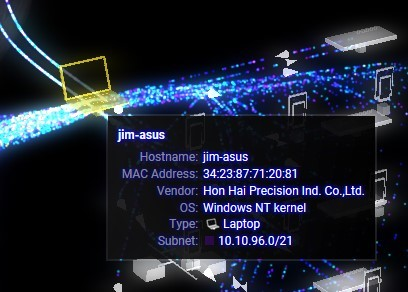
Notice that the time lapse from the initial scanning process until the offending system is marked as a problem is approximately 15 seconds.
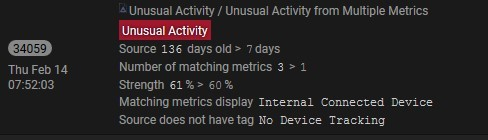
Subsequently the Darktrace system upgraded the threat status to “red” and notified us a second time of a network scan in progress. Darktrace also marked the offending device with a dark red/orange color to indicate the severity of the threat. Note the time in the bottom left corner is exactly 11 seconds after the first warning.
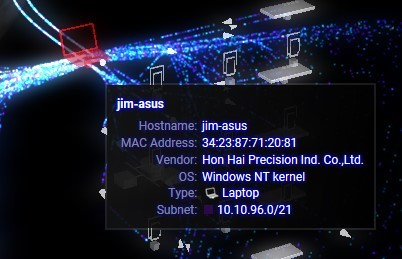
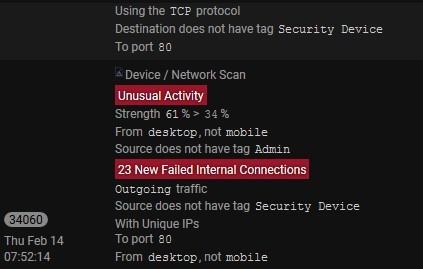
By 7:53 a.m., the instructor’s laptop had attempted connections to every device on the network and prompted the following image on the Darktrace Threat Visualizer interface, leaving no doubt that there was a problem with the instructor’s laptop.

The offending laptop was removed from our network. We weren’t going to wait to see how long it might take for our other, signature-based systems to identify and remediate this problem.
Working with the instructor, I scanned the laptop with various tools in an attempt to identify and remove the malware that created this network scan. Unfortunately, we were not able to find malware running on this device using traditional tools. Subsequently, we determined that the source of this breach probably originated from a USB drive that was shared with the contract instructor by one of his students the night before.
Just as Darktrace detected a zero-day trojan on our network in January, I was able to identify and remove a threat from our network using Darktrace before I spent days, weeks, or even months waiting for our antivirus/malware signatures to hopefully identify it.
Written by: Keith Siepel, IT Manager at Hydrotech, Inc. (Guest Contributor for Darktrace)
Original Article

